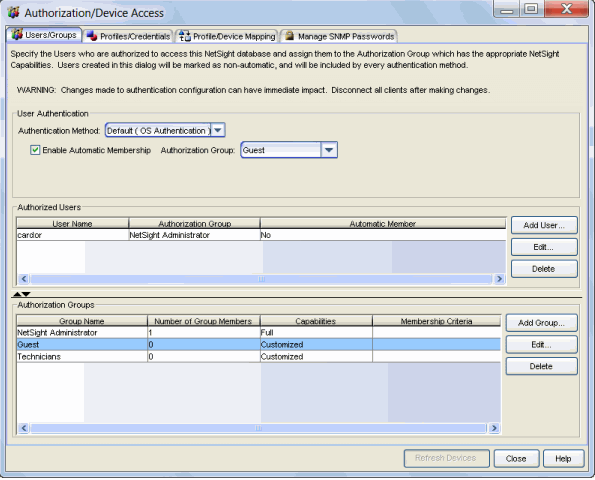
The Users/Groups tab is where you define the method that will be used to authenticate users who are attempting to launch an Extreme Management Center client or access the Management Center database using the Management Center Server Administration web page or the NAC Manager Dashboard. There are three authentication methods available: OS Authentication (the default), LDAP Authentication, and RADIUS Authentication.
The tab is also used to create the authorization groups that define the access privileges (called Capabilities) to specific Management Center application features. When a user successfully authenticates, they are assigned membership in an authorization group. Based on their membership in a particular group, users are granted specific capabilities in the application. For example, you may have an authorization group called "IT Staff" that grants access to a wide range of capabilities, while another authorization group called "Guest" grants a very limited range of capabilities.
| NOTE: | When changes to authentication and authorization configurations are made,
clients must be restarted in order to be subject to the new configuration. It is
suggested that you disconnect those clients affected by the changes made to your
authentication and authorization configurations. You can use the Client
Connections tab in the Server Information window to help identify which clients
are affected by the changes, and disconnect those clients. |
|---|
This Help topic contains an explanation of the different sections and fields in the User/Group tab. For complete steps in configuring authentication methods and creating authorization groups, see How to Configure User Access to Extreme Management Center Applications.
Click areas in the window for more information.
User Authentication
Use this section to configure the method that will be used to authenticate users who are attempting to launch a Management Center client or access the Management Center database using the Management Center Server Administration web page or the NAC Manager Dashboard. The following authentication methods are available: OS Authentication (the default), LDAP Authentication, and RADIUS Authentication.OS Authentication (Default)
With this authentication method, the Management Center Server uses the underlying host operating system to authenticate users. Use the Authorized Users table to create a list of users that will be allowed access and define their access capabilities.
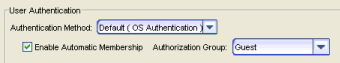
If desired, enable Automatic Membership and specify an authorization group. The Automatic Membership feature allows a user who has not been manually added to the Authorized Users table to be authenticated by the operating system, and dynamically added to the table and assigned to the specified authorization group the first time that they log in. These users are indicated by a "Yes" in the Automatic Member column of the Authorized Users table.
LDAP Authentication
With this authentication method, the Management Center Server uses the specified LDAP configuration to authenticate users.
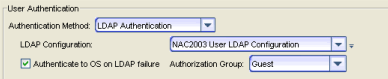
Use the drop-down list to select the LDAP configuration for the LDAP
server on your network that you want to use to authenticate users.
Use the configuration menu button ![]() (to the right of the drop-down list) to
add or edit an LDAP configuration, or manage your LDAP configurations.
(to the right of the drop-down list) to
add or edit an LDAP configuration, or manage your LDAP configurations.
With LDAP Authentication, you can configure dynamic assignment of users to authorization groups based on the attributes associated with a user in Active Directory. For example, you could create an authorization group that matches everyone in a particular organization, department, or location. When a user authenticates, the attributes associated with that user are matched against a list of criteria specified as part of each authorization group. The first group that has a criteria met by the user's attributes becomes the authorization group for that user. The user is then added to the Authorized Users table as an automatic member, with that authorization group.
The Authenticate to OS on LDAP failure feature provides the option to use OS Authentication automatic membership if the LDAP authentication should fail for any reason. Users authenticated by the operating system are dynamically assigned to the specified authorization group when they log in, and are automatically added to the Authorized Users table. These users are indicated by a "Yes" in the Automatic Member column of the table.
RADIUS Authentication
With this authentication method, the Management Center Server uses the specified RADIUS servers to authenticate users.
| NOTE: | The RADIUS Authentication mode supports the PAP authentication type. |
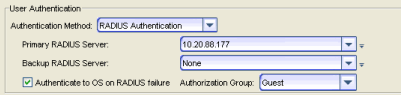
Use the drop-down list to select the primary RADIUS
server and backup RADIUS server (optional) on your network that you want to use to authenticate users.
Use the configuration menu button ![]() (to the right of the drop-down list) to add or edit a RADIUS server, or manage your
RADIUS servers.
(to the right of the drop-down list) to add or edit a RADIUS server, or manage your
RADIUS servers.
With RADIUS Authentication, you can configure dynamic assignment of users to authorization groups based on the attributes associated with a user in Active Directory. When a user authenticates, the attributes associated with that user are matched against a list of criteria specified as part of each authorization group. The first group that has a criteria met by the user's attributes becomes the authorization group for that user. The user is then added to the Authorized Users table as an automatic member, with that authorization group.
The Authenticate to OS on RADIUS failure feature provides the option to use OS Authentication automatic membership if the RADIUS server authentication should fail for any reason. Users authenticated by the operating system are dynamically assigned to the specified authorization group when they log in, and are automatically added to the Authorized Users table. These users are indicated by a "Yes" in the Automatic Member column of the table.
Authorized Users Table
This table lists all of the users who are currently authorized to access the Management Center database. From here you can add, edit, and delete users and define a user's membership in an authorization group. Each entry shows the user name and authorization group for the user, and whether the user was added as an Automatic Member.
Users that are manually added to the Authorized Users table using this tab will have the “automatic” attribute in the table set to No. These users have permission to log in, no matter what the authentication setting is set to: OS Authentication, LDAP Authentication, or RADIUS authentication. All authentication methods allow the non-automatic users to log in.
- Automatic Member
- Yes indicates that the user was automatically added to the authorization group via LDAP or RADIUS authentication, or the OS Authentication Automatic Membership feature. No indicates that the user is an authorized user that was manually added to the table.
- Add User
- Opens the Add User window where you can define the username, domain, and authorization group for a new authorized user.
- Edit (User)
- Opens the Edit User window where you can modify the authorization group membership for the selected user.
Authorization Groups Table
This table lists all of the authorization groups that have been created. Authorization groups define the access privileges to the Management Center application features. Based on their membership in a particular authorization group, users are granted specific capabilities in the application.
When users are added to the Authorized Users table, they are assigned an authorization group. With LDAP or RADIUS authentication, users are dynamically assigned to authorization groups based on the attributes associated with that user in Active Directory. The attributes are used to match against a list of criteria specified as part of each authorization group. The groups are checked in the order they are displayed in this table, from top to bottom. The first group that has a criteria matched by the user's attributes becomes the effective authorization group for that user.
Every user must be assigned to a group. A user whose attributes don't match any of the criteria specified for any of the groups will not be authenticated and will not be allowed to log in. For this reason, it is recommended to create a "catch-all" group (for example, you could use objectClass=person for an LDAP Active Directory), whose criteria is very generic and whose capabilities are highly restricted. This will help differentiate between a user who cannot authenticate successfully, and a user who does not belong to any group.
- Group Name
- This is the name assigned to the group. The Management Center Administrator group is created during installation and is granted Full capabilities and access. The Management Center Administrator group cannot be deleted and its capabilities can be viewed, but cannot be changed.
- Capabilities
- This column summarizes the capabilities granted to the associated group: Full (all capabilities) or Customized (a subset of capabilities).
- Add Group
- Opens the Add Group window where you can define the capabilities and settings for a new group.
- Edit (Group)
- Opens the Edit Group window where you can modify the capabilities and settings for a selected group.
Add/Edit User Window
This window lets you define a user's user name, domain, and membership in an authorization group. This information will be used to authenticate the user to the Extreme Management Center (Management Center) database.
Click areas in the window for more information.
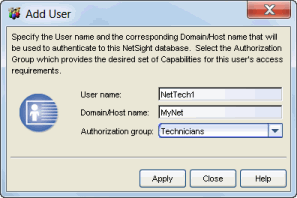
- Domain/Host name
- The user's domain/hostname that will be used to authenticate to the Management Center database.
- Authorization Group
- Use the drop-down list to select the authorization group where this user will be a member.
Add/Edit Group Window
This window lets you define a new authorization group or edit an existing group. For a description of each capability, see Authorization Group Capabilities.
Click areas in the windows for more information.
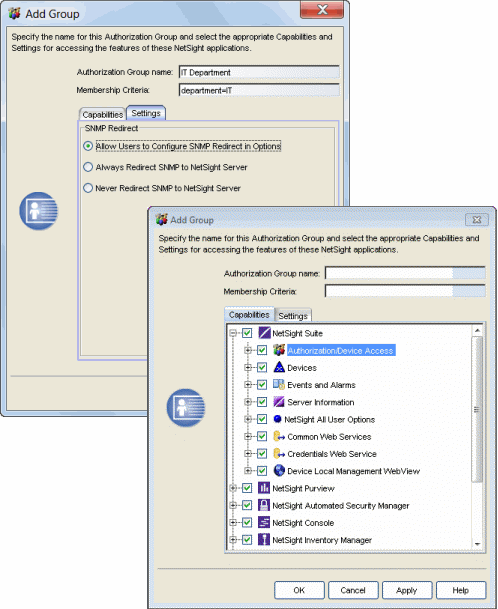
- Authorization Group Name
- This is the name given to the group. When adding a group, you can enter any text string that is descriptive of the members of this group.
- Membership Criteria
- When a user is successfully authenticated using LDAP or RADIUS
authentication, the
Active Directory attributes associated with that user are used to match against this list of
criteria to determine membership in the authorization group. The criteria is entered as name=value pairs, for example,
department=IT (LDAP) or Service-Type=Framed-User (RADIUS). A user must have the specified attribute with a
value that matches the specified value in order to meet the criteria
to belong to this group. Multiple name=value pairs may be listed
using a semicolon (";") to separate them. However, a user is
considered a member of the group if they match at least one of the
specified criteria; they do not need to match all of them.
NOTE: You cannot define membership criteria for the Management Center Administrator Group. Membership in the administrator group must be assigned manually using the Authorized Users table.
- Capabilities Tab
- Expand the Capabilities tree in this tab and select the specific capabilities to be granted to users that are members of this group. The capabilities are divided into suite-wide and application-specific capabilities. Access to a particular capability is granted when it is checked in the tree. For a description of each capability, see Authorization Group Capabilities.
- Settings Tab
- The Settings tab configures how SNMP requests will be handled for users that are members of this group.
- Allow Users to Configure SNMP Redirect in Options
- Lets users edit the Suite-wide Option setting for Client/Server SNMP Redirect.
- Always Redirect SNMP to NetSight Server
- Redirects all SNMP requests to the Management Center (NetSight) Server, regardless of the Suite-wide Option setting for Client/Server SNMP Redirect.
- Never Redirect SNMP to NetSight Server
- Never redirects SNMP requests to the Management Center (NetSight) Server, regardless of the Suite-wide Option setting for Client/Server SNMP Redirect.
For information on related windows:
For information on related tasks: