This Help topic tells you how to configure RADIUS monitoring tools to monitor Extreme Access Control engine performance and availability.
Use the following steps to create a list of RADIUS monitoring clients and configure a special authentication mapping for your AAA configuration used to authenticate the clients.
If you have multiple engine groups, you can use the same tools to monitor different engine groups, but each engine group is configured separately.
- Select the All Appliances group or an individual engine group in the NAC Manager left-panel tree.
- In the right-panel Configuration tab, click on the Edit button in the RADIUS Monitor Clients field.
- The Configure RADIUS Monitor Clients window opens.
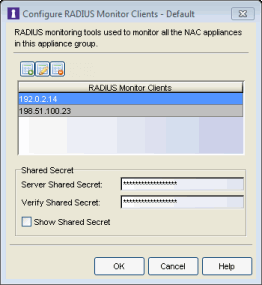
- Use this window to create a list of the monitoring tools (clients) used, and specify the shared secret to be used for all of them.
- Click the
 button. Enter the IP address for the first client and click OK. Repeat for each client that you want to add.
button. Enter the IP address for the first client and click OK. Repeat for each client that you want to add. - Enter the Server Shared Secret used. This is a string of characters used to encrypt and decrypt communications between the RADIUS Monitor clients and the engines. This string must match the shared secret configured on the client. Without the shared secret, the engines and clients will be unable to communicate. The shared secret must be at least 6 characters long; 16 characters is recommended. Dashes are allowed in the string, but spaces are not.
- Re-enter the shared secret to verify it.
- Click OK.
- Click the
- Use the NAC Manager
 toolbar button to open the NAC
Configuration window or use the Edit button in the
Configuration tab.
toolbar button to open the NAC
Configuration window or use the Edit button in the
Configuration tab. - Select the AAA configuration in the left panel.
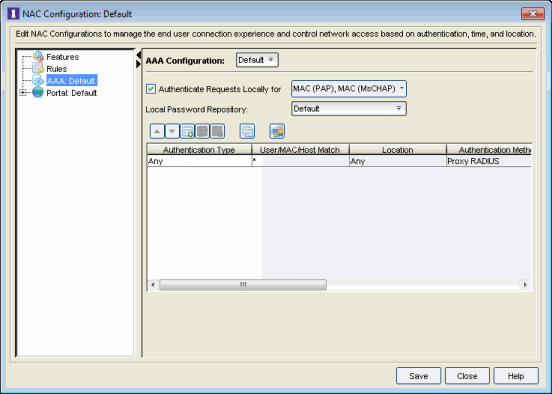
- In the right-panel mapping table, click the
 button to add a new mapping. (You must be using an advanced AAA Configuration in order to see the mapping table. If you are not, right-click on the AAA Configuration and select Make Advanced.)
button to add a new mapping. (You must be using an advanced AAA Configuration in order to see the mapping table. If you are not, right-click on the AAA Configuration and select Make Advanced.) - The Add User to Authentication Mapping window opens.
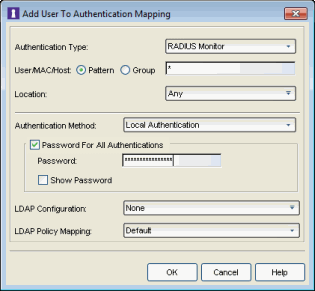
- Set the Authentication Type to RADIUS Monitor.
- Set the Authentication Method to Local Authentication and select the Password for all Authentications checkbox. Enter the desired password that will be used for all client authentications.
- Click OK.
- The new mapping will be listed in the mapping table. You can use the arrows to adjust the position of the new mapping in the table. In the screen below you can see that the RADIUS Monitor rule has been moved to the first row in the table because it is more granular. Click Save to save your changes.
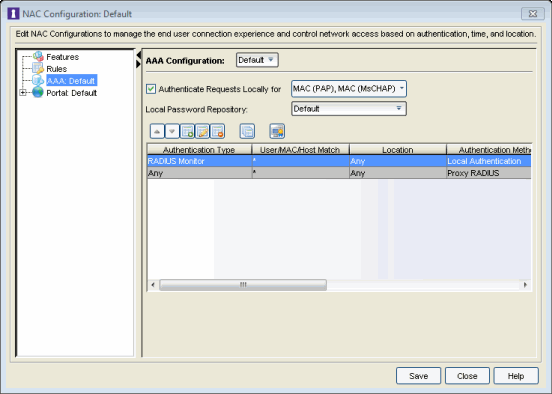
- Click the Enforce toolbar button to enforce the new configuration to your engine groups.
Any authentication request coming from an IP address that matches the list of RADIUS monitor clients will be authenticated using the password you provided in the AAA mapping. In these cases, the username does not matter. The password configured will not be able to be used for authentication from any other part of the network. The Access Control engine responds back with a basic accept to any RADIUS monitor client’s RADIUS request.
For information on related help topics: