This window lets you set the server certificate trust mode that specifies how all the servers in your Extreme Management Center deployment handles certificates received from other servers. You can access this window from the Server Information Window Certificates Tab.
Depending on your deployment, there can potentially many servers in Management Center and NAC. For example, there is the Management Center server, the Extreme Access Control appliance servers, and Access Control assessment servers. In addition, there may be external servers such as LDAP servers that both Management Center and Access Control may communicate with. As these different servers communicate, they use server certificates to determine whether or not they trust each other.
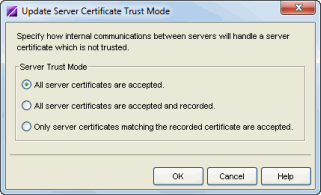
The trust mode is used to specify how the servers handle the certificates they receive from other servers. You can set the trust mode to one of the following options:
- Trust All (default mode) - All certificates from other
servers are accepted without a trust check. This mode is primarily used while setting up a Management Center/Access Control deployment,
and is also suitable when the network is sufficiently protected from spoofing
attacks.
This mode is also useful when troubleshooting trust problems on the network. It allows the Management Center server to communicate with all Access Control appliances, and configure those appliances to accept all certificates. This restores any communication that might have been broken due to a trust issue, and allows you to resolve the problem from NAC Manager. - Trust and Record - All certificates from other servers are
accepted without a trust check. Additionally, each server records the
certificate that it receives and associates that certificate with the sending server.
In this way, each server builds their own set of recorded certificates, creating
a list of certificates that they trust.
This mode is used initially until all servers build a complete set of certificates they need, and then the mode can be changed to Locked. It is important to give this phase enough time so that connections between the various servers can take place and all certificates are recorded. Administrators must ensure that no servers are spoofed during the time this mode is used. When you are confident that all certificates are exchanged and recorded, change the trust mode to Locked. - Locked - Any certificate from another server must match the
certificate that was recorded for that server during the Trust and Record phase. If the server
certificate does not match, then the server is not trusted.
This mode provides an extra level of security intended to detect and prevent someone from spoofing a server. If an IP address or hostname is hijacked and connections are routed to another server, that server is not trusted.
While the "Locked" mode is the most secure, if any server certificate is replaced, the new certificate will be rejected. Therefore, if you are replacing a server certificate, you should revert back to the "Trust and Record" mode until the new certificate has been recorded.
When the trust mode is changed, the Management Center server is immediately changed to use the new mode. Access Control appliances begin using the new trust mode when they are enforced.
For more information on how to use trust modes, see Advanced Security Options in the Secure Communication Help topic.
For information on related windows: