This Help topic describes how to replace the Extreme Management Center server certificate. During installation, Management Center generates a new, unique private server key and server certificate. While these provide secure communication, there may be cases where you want to update to a certificate provided from an external certificate authority, or add certificates in order to meet the requirements of external components with which Management Center must communicate. Additionally, you may want to use a "browser-friendly" certificate so that users don't see browser certificate warnings when they access web pages.
You need a server private key and server certificate to perform the certificate replacement. If you do not have these, this topic also includes procedures used to generate them.
Some instructions in this Help topic use OpenSSL software to perform certain tasks. OpenSSL is available on the Management Center engine or can be downloaded from http://www.openssl.org. After downloading and installing OpenSSL, add the OpenSSL tool to your path using the instructions in How to Add OpenSSL to Your Path in the Secure Communication Help topic. Other software tools can be used to perform these tasks, if desired.
Instructions on:
- Certificate Requirements
- Replacing the Certificate
- Verifying the Certificate
- Generating a Server Private Key and Server Certificate
Certificate Requirements
You need the RSA or DSA server private key (in PKCS #8 format) used to generate the server certificate. For "browser-friendly" certificates, the server certificate should identify the Extreme Management Center server by its fully qualified host name. If you do not have the server private key and server certificate, refer to the instructions for generating them.
If your certificate authority (CA) provides additional intermediate certificates, you need to provide those as well. The intermediate certificates can be used in whatever format the CA provides them. They may be in individual files, in a bundle file, or even in the same file as the server certificate.
| NOTE: | if you need to convert your key file to a PKCS #8 format, use the following OpenSSL command where <server.key> is the original non‑PKCS #8 formatted key file. (OpenSSL is available on Extreme Management Center and Extreme Access Control engines. The server.key file can be copied and converted on either engine.) openssl pkcs8 -topk8 -in <server.key> -out server-pkcs8.key -nocrypt |
Replacing the Certificate
The following steps assume that you have a replacement server private key and server certificate ready to use. If you do not, refer to the Generating a Server Private Key and Server Certificate section below.
| NOTE: | Whenever the Management Center server certificate is changed, other Management Center components may be affected by the change and stop trusting the server. Management Center clients and other servers must be configured to handle updated certificates using the client certificate trust mode and server certificate trust mode settings. Before updating the Management Center server certificate, be sure that the client and server trust modes are configured to trust the new certificate. For more information, see Update Client Certificate Trust Mode window and Update Server Certificate Trust Mode window. |
|---|
To replace the server private key and server certificate:
- Access the Server Information window from any Management Center application (Tools > Server Information). Click on the Certificates tab.
- Click the Update Server Certificate button. The Update Server Certificate window opens.
- Select the option to provision a private key and certificate from files.
- In the Private Key section, provide a file containing the private key that corresponds to the certificate. It must be encoded as a PKCS #8 file. Enter the path name of the file or use the Browse button to navigate to the file. If the file is encrypted with a password, check the password box and supply the password in the field.
- In the Certificate Files section, use the Add Files button to add one or more certificate files as provided by the certificate authority. This includes the server certificate, as well as any intermediate or chained certificates. You can multi-select files in the file chooser window, and the files can be added in any order.
- Click OK. You will see a confirmation window listing your file information so that you can confirm that the information you have provided is correct. Click Yes to proceed with the certificate replacement. The private key and server certificate will be updated on the Management Center server.
- Restart the Management Center server to deploy the new private key and server certificate. For instructions on how to restart the server, see How to Stop and Start the Extreme Management Center Server.
Verifying the Certificate
Once the new server certificate is installed and the server has restarted, use one of the following methods to verify that the server is now using the proper server certificate.
Use a Browser
- Access the Extreme Access Control Dashboard web page at
https://<NetSight Server FQDN>:8443/Monitor/jsp/nac/dashboard.jsp.or the Management Center web page athttps://<NetSight Server FQDN>:8443/Monitor/jsp/reporting/reporting.jsp. If your intention was to eliminate browser warnings, verify that no browser warnings are displayed when you access the web page. - Then, use your browser to view the certificate
used:
- Internet Explorer 7.0 or later: View > Security Report > View Certificates
- Mozilla Firefox 3.5 or later: Tools > Page Info > Security > View Certificates
Use OpenSSL
- Use OpenSSL to test the server connection
with the following command:
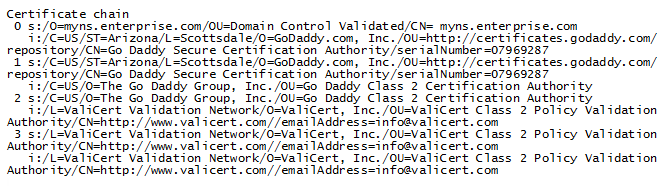
openssl s_client -connect <NetSight Server IP>:8443 - The output from this program includes a section titled "Certificate
chain". This enumerates the certificates returned by the server.
For each certificate, the Subject and the Issuer are displayed. With multiple
certificates, if the certificates are in the proper order, the issuer of each
certificate matches the subject of the following certificate. Here is a sample output from the program:
- You need to terminate the program with CTRL-C.
Generating a Server Private Key and Server Certificate
If you do not have a server private key and server certificate to use as a replacement, you can generate them using the instructions in the sections below. You need to:
- Generate a server private key. It is recommended that you use OpenSSL to generate an RSA key.
- Create a Certificate Signing Request.
- Submit the request to a Certificate Authority or generate a self-signed certificate.
- Verify the contents of the server certificate.
You can use the following steps regardless of whether you are using a commercial certificate authority or an in-house certificate authority.
Generate a Server Private Key
Use the following steps to generate an encrypted RSA private key.
- Enter the following command to use OpenSSL
to generate a password-encrypted PKCS #8 formatted server private key file. Use the
key size and output file name you prefer. (If you are unsure of the key size, use 2048.)
openssl genrsa <key size> | openssl pkcs8 -topk8 -out <output file>
For example:openssl genrsa 2048 | openssl pkcs8 -topk8 -out server.key - You are prompted for an Encryption Password. Be sure to make a note of the password that you enter. If the password is lost, you need to generate a new server private key and a new server certificate.
Create a Certificate Signing Request
Use the following steps to create a Certificate Signing Request (CSR).
- Enter the following command to generate a CSR file. Use the output
file name you used in step 1 above as the input file, and specify the output
file name you prefer:
openssl req -new -key <input file> -out <output file>
For example:openssl req -new -key server.key -out server.csr - You are prompted for information that appears in the certificate. When you are prompted for a
Common Name, specify the fully qualified host name of the Management Center server. For
example:
Common Name (eg, YOUR name) []:netsight1.mycompany.com
Submit the Request to a Certificate Authority
The procedure for submitting a CSR to a Certificate Authority (CA) varies with the service used. Usually, it is done through a website using a commercial service such as VeriSign. You can also use an in-house CA, which generates certificates used internally by your enterprise. You provide information including the contents of the CSR, and receive back one or more files containing the server certificate and possibly other certificates to be used in a chain.
Verify the Contents of the Server Certificate
It is important to verify that the new server certificate contains the data you supplied when creating the CSR. In particular, make sure the Common Name (CN) is the fully qualified host name of the Management Center server.
Use OpenSSL to view the contents of the server certificate file server.crt
using the following command: openssl x509 -in server.crt -text -noout