Use this window to either add a new rule to the selected ACL or edit an existing rule in an ACL. You can access this window from the ACL Editor by clicking the New or Edit button in the right-panel Editor tab.
ACL Manager supports five types of ACLs: S/K/N 7.x+, N-Series 6.x, X-Series, XSR, and Common. Each ACL type can contain a specific set of rules that define parameters that are appropriate for the devices that they support. Common ACLs can contain rules that are supported by all five types. The rule types that can be used with each of the five ACL types are listed in the ACL Rules Summary.
The parameters/fields in this window will change according to the rule type selected. This help topic provides information for each of the following rule types:
AH, ESP, or GRE Rules
AH, ESP, and GRE rules can be applied to allow or block AH, ESP, and GRE traffic from entering or leaving a router port. The rule definitions for AH, ESP, and GRE traffic share the same parameters. ESP and GRE rules can only be created in S/K/N 7.x+, N-Series 6.x, and XSR ACLs. AH rules can only be created in N-Series 6.x and XSR ACLs.
Sample ESP rule.
Click areas in the window for more information.
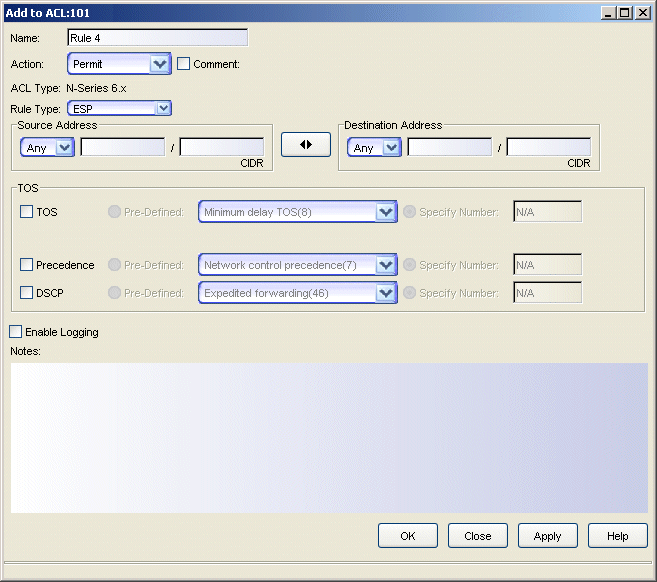
- Name
- The name given to this rule. The name is a string of up to 100 characters or numbers and is usually descriptive of the rule's function. This name is not used in the device. Rather, it serves as a means of identifying rules in ACL Manager.
- Action
- Permit - allow AH, ESP, or GRE traffic that matches the parameters in this rule to enter or
leave the port where this
rule is applied.
Deny - block AH, ESP, or GRE traffic that matches the parameters in this rule from entering or leaving the port where this rule is applied.
Remark - allows you to add a remark to the ACL. (Available on S-Series, K-Series, and N-Series devices with 7.x firmware only.)
If the Comment checkbox is checked, the rule will be commented out (disabled).
- Source Address
- Allow or block packets with this source address, based on the selected Action (permit/deny). This parameter can be defined as Any source address, a specific IP address or, as a subnet or range of addresses when used with the associated Mask parameter. Typing a slash after entering an address advances the entry marker to the mask field and automatically enters a mask (based on the address).
- Destination Address
- Allow or block packets with this destination address, based on the selected Action (permit/deny). This parameter can be defined as Any destination address, a specific IP address or, as a subnet or range of addresses when used with the associated Mask parameter. Typing a slash after entering an address advances the entry marker to the mask field and automatically enters a mask (based on the address).
- Mask
- The mask is used as a filter to define a range of IP addresses. Masks can be entered as CIDR or dotted-decimal format. Address bits from a source or destination address in the header of the packet are ANDed with the associated mask and compared against the source/destination address fields. For example, if you entered 172.90.00.00 into the Source/Destination field and typed 255.255.0.0 as the associated mask, then all incoming packets in the range 172.90.00.00 through 172.90.255.255 would result in an address match.
- TOS
- Allow or block packets with these ToS (Type of Service) or DSCP (Diffserv
Codepoint) values, based on the selected Action (permit/deny). The ToS/DSCP
field contained in the IP header of a frame is used by applications to
indicate the priority and Quality of Service for each frame.
- TOS - allow or block packets with the TOS value specified here. You can select from the pre-defined values or specify a decimal number between 0 and 255.
- Precedence - allow or block packets with the Precedence value specified here. You can select one of the pre-defined values or specify a precedence value of 0-7.
- DSCP - allow or block packets with the DSCP value specified here. You can select from the pre-defined values or specify a decimal number between 0 and 63.
NOTE: IPv4 defines the ToS field as setting the Precedence and Type of Service requested for a packet. IPv6 redefined this field as the DS (Differentiated Service) field containing a DSCP (Differentiated Service Codepoint) value, to define Per-Hop-Behavior (PHB) groups called Expedited Forwarding (EF) and Assured Forwarding (AF). For more information on these PHB groups, refer to RFC 2597 and RFC 2598.
- Enable Logging/Enable Verbose Logging
- These checkboxes let you enable or disable logging or detailed (verbose) logging for this rule. (Verbose logging is available on S-Series, K-Series, and N-Series devices with 7.x firmware only.) When enabled, a Log message is sent to the device console and if you have a Syslog server configured, the same message is sent to the Syslog server. For more information on logging functionality, refer to your router User's Guide.
- Notes
- Enter a description of the rule. This information will be displayed in the Editor tab in the ACL Editor.
ICMP or IP Rules
ICMP and IP rules share most of the same parameters, however different parameters apply to the rules depending on which type of ACL they are created for. These rules allow or block ICMP or IP traffic from entering or leaving a router port.
Sample ICMP rule.
Click areas in the window for more information.
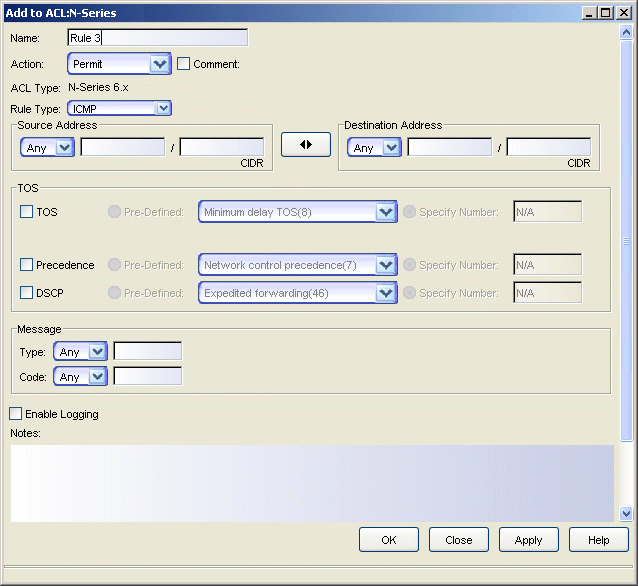
- Name
- The name given to this rule. The name is a string of up to 100 characters or numbers and is usually descriptive of the rule's function. This name is not used in the device. Rather, it serves as a means of identifying rules in ACL Manager.
- Action
- Permit - allow ICMP/IP traffic that matches the parameters in
this rule to enter or leave the port where this rule is applied.
Deny - block ICMP/IP traffic that matches the parameters in this rule from entering or leaving the port where this rule is applied.
Remark - allows you to add a remark to the ACL. (Available on S-Series, K-Series, and N-Series devices with 7.x firmware only.)
If the Comment checkbox is checked, the rule will be commented out (disabled).
- Source Address
- Allow or block packets with this source address, based on the selected Action (permit/deny). This parameter can be defined as Any source address, a specific IP address or, as a subnet or range of addresses when used with the associated Mask parameter. Typing a slash after entering an address advances the entry marker to the mask field and automatically enters a mask (based on the address).
- Destination Address
- Allow or block packets with this destination address, based on the selected Action (permit/deny). This parameter can be defined as Any destination address, a specific IP address or, as a subnet or range of addresses when used with the associated Mask parameter. Typing a slash after entering an address advances the entry marker to the mask field and automatically enters a mask (based on the address).
- Mask
- The mask is used as a filter to define a range of IP addresses. Masks can be entered as CIDR or dotted-decimal format. Address bits from a source or destination address in the header of the packet are ANDed with the associated mask and compared against the source/destination address fields. For example, if you entered 172.90.00.00 into the Source/Destination field and typed 255.255.0.0 as the associated mask, then all incoming packets in the range 172.90.00.00 through 172.90.255.255 would result in an address match.
- TOS
- Allow or block packets with these ToS (Type of Service) or DSCP (Diffserv
Codepoint) values, based on the selected Action (permit/deny). The ToS/DSCP
field contained in the IP header of a frame is used by applications to
indicate the priority and Quality of Service for each frame.
- TOS - allow or block packets with the TOS value specified here. You can select from the pre-defined values or specify a decimal number between 0 and 255.
- Precedence - allow or block packets with the Precedence value specified here. You can select one of the pre-defined values or specify a precedence value of 0-7.
- DSCP - allow or block packets with the DSCP value specified here. You can select from the pre-defined values or specify a decimal number between 0 and 63.
NOTE: IPv4 defines the ToS field as setting the Precedence and Type of Service requested for a packet. IPv6 redefined this field as the DS (Differentiated Service) field containing a DSCP (Differentiated Service Codepoint) value, to define Per-Hop-Behavior (PHB) groups called Expedited Forwarding (EF) and Assured Forwarding (AF). For more information on these PHB groups, refer to RFC 2597 and RFC 2598.
- Message
- ICMP rules can be defined to allow or reject traffic based on ICMP Message Type (0 to 255). When a Message Type is specified, an optional ICMP Message Code (1 to 255) can be used to create a more specific rule.
- Enable Logging
- These checkboxes let you enable or disable logging or detailed (verbose) logging for this rule. (Verbose logging is available on S-Series, K-Series, and N-Series devices with 7.x firmware only.) When enabled, a Log message is sent to the device console and if you have a Syslog server configured, the same message is sent to the Syslog server. For more information on logging functionality, refer to your router User's Guide.
- Notes
- Enter a description of the rule. This information will be displayed in the Editor tab in the ACL Editor.
IPINIP Rules
IPINIP rules allow or block IPINIP traffic from entering or leaving a router port. This type of rule can only be created in S/K/N 7.x+and X-Series ACLs.
Sample IPINIP rule.
Click areas in the window for more information.
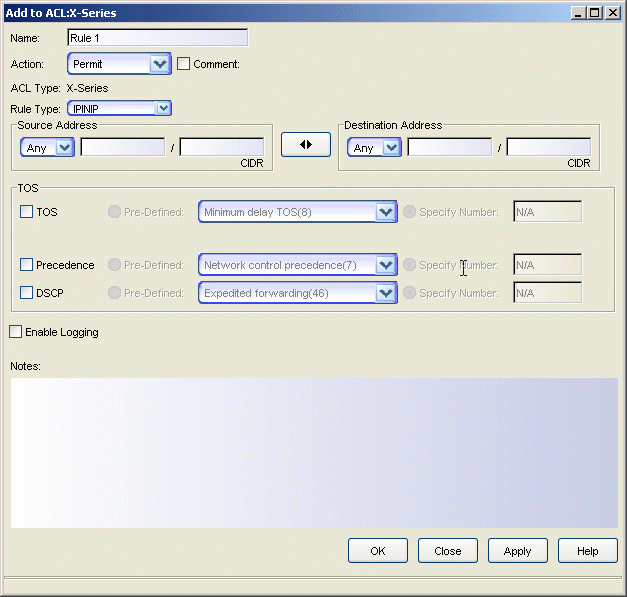
- Name
- The name given to this rule. The name is a string of up to 100 characters or numbers and is usually descriptive of the rule's function. This name is not used in the device. Rather, it serves as a means of identifying rules in ACL Manager.
- Action
- Permit - allow IPINIP traffic that matches the parameters in this rule to enter or
leave the port where this
rule is applied.
Deny - block IPINIP traffic that matches the parameters in this rule from entering or leaving the port where this rule is applied.
If the Comment checkbox is checked, the rule will be commented out (disabled).
- Source Address
- Allow or block packets with this source address, based on the selected Action (permit/deny). This parameter can be defined as Any source address, a specific IP address or, as a subnet or range of addresses when used with the associated Mask parameter. Typing a slash after entering an address advances the entry marker to the mask field and automatically enters a mask (based on the address).
- Destination Address
- Allow or block packets with this destination address, based on the selected Action (permit/deny). This parameter can be defined as Any destination address, a specific IP address or, as a subnet or range of addresses when used with the associated Mask parameter. Typing a slash after entering an address advances the entry marker to the mask field and automatically enters a mask (based on the address).
- Mask
- The mask is used as a filter to define a range of IP addresses. Masks can be entered as CIDR or dotted-decimal format. Address bits from a source or destination address in the header of the packet are ANDed with the associated mask and compared against the source/destination address fields. For example, if you entered 172.90.00.00 into the Source/Destination field and typed 255.255.0.0 as the associated mask, then all incoming packets in the range 172.90.00.00 through 172.90.255.255 would result in an address match.
- TOS
- Allow or block packets with these ToS (Type of Service) or DSCP (Diffserv
Codepoint) values, based on the selected Action (permit/deny). The ToS/DSCP
field contained in the IP header of a frame is used by applications to
indicate the priority and Quality of Service for each frame.
- TOS - allow or block packets with the TOS value specified here. You can select from the pre-defined values or specify a decimal number between 0 and 255.
- Precedence - allow or block packets with the Precedence value specified here. You can select one of the pre-defined values or specify a precedence value of 0-7.
- DSCP - allow or block packets with the DSCP value specified here. You can select from the pre-defined values or specify a decimal number between 0 and 63.
NOTE: IPv4 defines the ToS field as setting the Precedence and Type of Service requested for a packet. IPv6 redefined this field as the DS (Differentiated Service) field containing a DSCP (Differentiated Service Codepoint) value, to define Per-Hop-Behavior (PHB) groups called Expedited Forwarding (EF) and Assured Forwarding (AF). For more information on these PHB groups, refer to RFC 2597 and RFC 2598.
- Enable Logging
- This check box lets you enable or disable logging for this rule. When enabled, a Log message is sent to the console and if you have a Syslog server configured, the same message is sent to the Syslog server.
- Notes
- Enter a description of the rule. This information will be displayed in the Editor tab in the ACL Editor.
IP-Protocol Rules
IP-Protocol rules allow or block specific IP traffic from entering or leaving a router port. They can be used to define rules that specify any valid IP protocol other than those specified in other rules, (IP, ICMP, TCP, and UDP). For example, to specify a rule for IP encapsulation in IP, you can use IP protocol type 4 in the rule. IP-Protocol rules are only supported for S/K/N 7.x+ and N-Series 6.x ACLs.
Sample IP-Protocol rule.
Click areas in the window for more information.
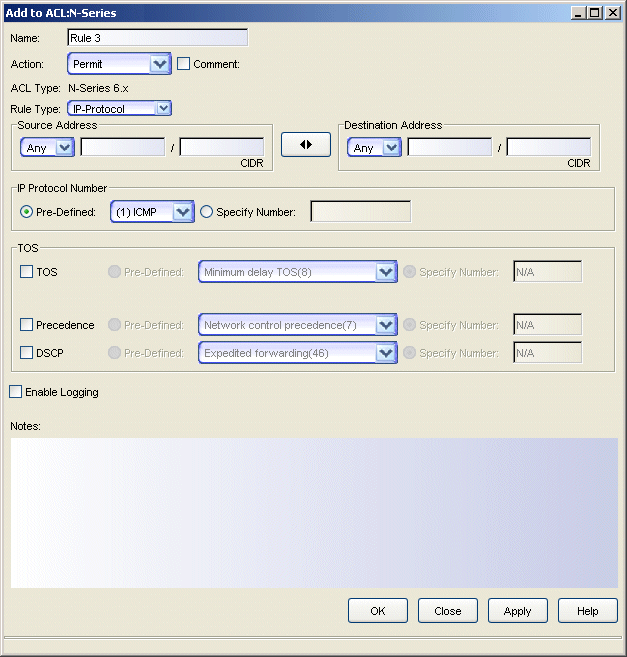
- Name
- The name given to this rule. The name is a string of up to 100 characters or numbers and is usually descriptive of the rule's function. This name is not used in the device. Rather, it serves as a means of identifying rules in ACL Manager.
- Action
- Permit - allow IP-Protocol traffic that matches the parameters in this rule to enter or
leave the port where this
rule is applied.
Deny - block IP-Protocol traffic that matches the parameters in this rule from entering or leaving the port where this rule is applied.
Remark - allows you to add a remark to the ACL. (Available on S-Series, K-Series, and N-Series devices with 7.x firmware only.)
If the Comment checkbox is checked, the rule will be commented out (disabled).
- Source Address
- Allow or block packets with this source address, based on the selected Action (permit/deny). This parameter can be defined as Any source address, a specific IP address or, as a subnet or range of addresses when used with the associated Mask parameter. Typing a slash after entering an address advances the entry marker to the mask field and automatically enters a mask (based on the address).
- Destination Address
- Allow or block packets with this destination address, based on the selected Action (permit/deny). This parameter can be defined as Any destination address, a specific IP address or, as a subnet or range of addresses when used with the associated Mask parameter. Typing a slash after entering an address advances the entry marker to the mask field and automatically enters a mask (based on the address).
- Mask
- The mask is used as a filter to define a range of IP addresses. Masks can be entered as CIDR or dotted-decimal format. Address bits from a source or destination address in the header of the packet are ANDed with the associated mask and compared against the source/destination address fields. For example, if you entered 172.90.00.00 into the Source/Destination field and typed 255.255.0.0 as the associated mask, then all incoming packets in the range 172.90.00.00 through 172.90.255.255 would result in an address match.
- TOS
- Allow or block packets with these ToS (Type of Service) or DSCP (Diffserv
Codepoint) values, based on the selected Action (permit/deny). The ToS/DSCP
field contained in the IP header of a frame is used by applications to
indicate the priority and Quality of Service for each frame.
- TOS - allow or block packets with the TOS value specified here. You can select from the pre-defined values or specify a decimal number between 0 and 255.
- Precedence - allow or block packets with the Precedence value specified here. You can select one of the pre-defined values or specify a precedence value of 0-7.
- DSCP - allow or block packets with the DSCP value specified here. You can select from the pre-defined values or specify a decimal number between 0 and 63.
NOTE: IPv4 defines the ToS field as setting the Precedence and Type of Service requested for a packet. IPv6 redefined this field as the DS (Differentiated Service) field containing a DSCP (Differentiated Service Codepoint) value, to define Per-Hop-Behavior (PHB) groups called Expedited Forwarding (EF) and Assured Forwarding (AF). For more information on these PHB groups, refer to RFC 2597 and RFC 2598.
- Enable Logging
- These checkboxes let you enable or disable logging or detailed (verbose) logging for this rule. (Verbose logging is available on S-Series, K-Series, and N-Series devices with 7.x firmware only.) When enabled, a Log message is sent to the device console and if you have a Syslog server configured, the same message is sent to the Syslog server. For more information on logging functionality, refer to your router User's Guide.
- Notes
- Enter a description of the rule. This information will be displayed in the Editor tab in the ACL Editor.
Standard Rules
Standard rules can be applied to allow or block IP traffic from a specific source address from entering or leaving a router port. A Standard rule cannot be created in Common ACLs.
Sample Standard rule.
Click areas in the window for more information.
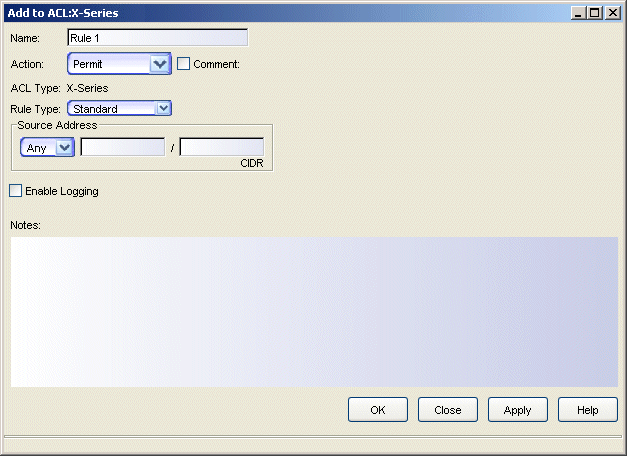
- Name
- The name given to this rule. The name is a string of up to 100 characters or numbers and is usually descriptive of the rule's function. This name is not used in the device. Rather, it serves as a means of identifying rules in ACL Manager.
- Action
- Permit - allow IP traffic that matches the parameters in this
rule to enter or leave the port where this
rule is applied.
Deny - block IP traffic that matches the parameters in this rule from entering or leaving the port where this rule is applied.
If the Comment checkbox is checked, the rule will be commented out (disabled).
- Source Address
- Allow or block packets with this source address, based on the selected Action (permit/deny). This parameter can be defined as Any source address, a specific IP address or, as a subnet or range of addresses when used with the associated Mask parameter. Typing a slash after entering an address advances the entry marker to the mask field and automatically enters a mask (based on the address).
- Mask
- The mask is used as a filter to define a range of IP addresses. Masks can be entered as CIDR or dotted-decimal format. Address bits from a source address in the header of the packet are ANDed with the associated mask and compared against the source address field. For example, if you entered 172.90.00.00 into the Source field and typed 255.255.0.0 as the associated mask, then all incoming packets in the range 172.90.00.00 through 172.90.255.255 would result in an address match.
- Enable Logging
- This check box lets you enable or disable logging for this rule. When enabled, a Log message is sent to the console and if you have a Syslog server configured, the same message is sent to the Syslog server.
- Notes
- Enter a description of the rule. This information will be displayed in the Editor tab in the ACL Editor.
TCP or UDP Rules
TCP and UDP rules allow or block TCP or UDP traffic from entering or leaving a router port. TCP and UDP rules can be created in S/K/N 7.x+, N-Series 6.x, X-Series, XSR, and Common ACLs. When created for S/K/N 7.x+, N-Series 6.x, and X-Series ACLs, these rules provide additional settings for Type of Service and Logging.
Sample TCP rule.
Click areas in the window for more information.
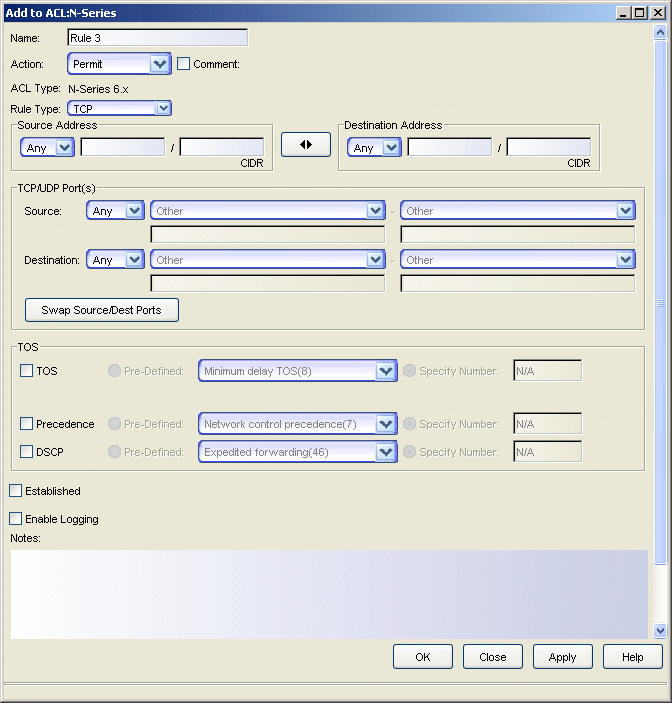
- Name
- The name given to this rule. The name is a string of up to 100 characters or numbers and is usually descriptive of the rule's function. This name is not used in the device. Rather, it serves as a means of identifying rules in ACL Manager.
- Action
- Permit - allow TCP/UDP traffic that matches the parameters in this rule to enter or
leave the port where this
rule is applied.
Deny - block TCP/UDP traffic that matches the parameters in this rule from entering or leaving the port where this rule is applied.
Remark - allows you to add a remark to the ACL. (Available on S-Series, K-Series, and N-Series devices with 7.x firmware only.)
If the Comment checkbox is checked, the rule will be commented out (disabled).
- Source Address
- Allow or block packets with this source address, based on the selected Action (permit/deny). This parameter can be defined as Any source address, a specific IP address or, as a subnet or range of addresses when used with the associated Mask parameter. Typing a slash after entering an address advances the entry marker to the mask field and automatically enters a mask (based on the address).
- Destination Address
- Allow or block packets with this destination address, based on the selected Action (permit/deny). This parameter can be defined as Any destination address, a specific IP address or, as a subnet or range of addresses when used with the associated Mask parameter. Typing a slash after entering an address advances the entry marker to the mask field and automatically enters a mask (based on the address).
- Mask
- The mask is used as a filter to define a range of IP addresses. Masks can be entered as CIDR or dotted-decimal format. Address bits from a source or destination address in the header of the packet are ANDed with the associated mask and compared against the source/destination address fields. For example, if you entered 172.90.00.00 into the Source/Destination field and typed 255.255.0.0 as the associated mask, then all incoming packets in the range 172.90.00.00 through 172.90.255.255 would result in an address match.
- Source Port
- Filter or forward packets using this source port argument, based on the selected Action (permit/deny). You can set the source port as Any source TCP/UDP port, select a TCP/UDP type from the list of well-known values, or select Other and manually enter the value in decimal form. TCP/UDP port address. You can also enter a range of values. (TCP/UDP port numbers are defined in RFC 1700.)
| TIP: | You can define a new value for a TCP/UDP port number using the Pre-Defined Well-Known IDs window. Once
defined, it is available for selection from the list of well-known values.
|
|---|
- Destination Port
- Filter or forward packets using this destination port argument, based on the selected Action (permit/deny). You can set the destination port as Any source TCP/UDP port, select a TCP/UDP type from the list of well-known values, or select Other and manually enter the value in decimal form. TCP/UDP port address. You can also enter a range of values. (TCP/UDP port numbers are defined in RFC 1700.)
- TOS
- Allow or block packets with these ToS (Type of Service) or DSCP (Diffserv
Codepoint) values, based on the selected Action (permit/deny). The ToS/DSCP
field contained in the IP header of a frame is used by applications to
indicate the priority and Quality of Service for each frame.
- TOS - allow or block packets with the TOS value specified here. You can select from the pre-defined values or specify a decimal number between 0 and 255.
- Precedence - allow or block packets with the Precedence value specified here. You can select one of the pre-defined values or specify a precedence value of 0-7.
- DSCP - allow or block packets with the DSCP value specified here. You can select from the pre-defined values or specify a decimal number between 0 and 63.
NOTE: IPv4 defines the ToS field as setting the Precedence and Type of Service requested for a packet. IPv6 redefined this field as the DS (Differentiated Service) field containing a DSCP (Differentiated Service Codepoint) value, to define Per-Hop-Behavior (PHB) groups called Expedited Forwarding (EF) and Assured Forwarding (AF). For more information on these PHB groups, refer to RFC 2597 and RFC 2598.
- Established
- Indicates whether this rule will allow TCP/UDP responses through the router, provided the connection between two hosts is already established.
- Enable Logging
- These checkboxes let you enable or disable logging or detailed (verbose) logging for this rule. (Verbose logging is available on S-Series, K-Series, and N-Series devices with 7.x firmware only.) When enabled, a Log message is sent to the device console and if you have a Syslog server configured, the same message is sent to the Syslog server. For more information on logging functionality, refer to your router User's Guide.
- Notes
- Enter a description of the rule. This information will be displayed in the Editor tab in the ACL Editor.
- Swap

- Exchanges the Source and Destination Address parameters. The source address and mask become the destination address and mask and vice-versa.
- Swap Source/Dest Ports

- Exchanges the Source and Destination Port parameters. The source port parameters become the destination port parameters and vice-versa.
For information on related windows:
For information on related tasks: