Flow alarms are used for reporting network traffic flow anomalies detected by the NetFlow flow collector. NetFlow is a flow-based data collection protocol that provides information about the packet flows being sent over a network. K-Series, S-Series, and N-Series devices support NetFlow flow collection. For more information about NetFlow, see the Flow Sensor Configuration Window Help topic.
Use the Alarms Manager window to create your flow alarm definition, and then use this window to identify the flow criteria that must be matched to trigger a flow alarm.
When creating flow alarms, be aware that NetSight might handle thousands of flows each second, and performance can degrade if there are too many flow alarms configured, or if the configured flow alarms match too many flows.
Here are two examples of how flow alarms can be useful on the network:
- Flow alarms can provide visibility of users with multiple devices hidden behind NAT gateways, by detecting network traffic with low TTL (IP Time to Live) values. This detection is based on the TTL field contained in the IP header of a frame. The TTL field indicates the maximum number of router hops the packet can make before being discarded. The TTL field is set by the packet sender and reduced by every router on the route to its destination. So, for example, if a packet from a Windows machine with a default TTL of 128 is detected by NetFlow with a TTL of 127, then it can be deduced that the packet has traversed a routed interface or NAT gateway, and an alarm can be triggered.
- Flow alarms can be used to detect suspicious or undesirable network traffic. This detection is based on the flow's source or destination IP address and (optional) port number. For example, flows from an internal or external web server, or flows from a web server to an external IP address, can be detected and cause an alarm to be triggered.
| NOTE: | There is no way to clear Flow alarms automatically. You can create an action-only alarm (Alarms Manager window, Other Options tab) to avoid the need to manually clear a Flow alarm. |
Click areas in the window for more information.
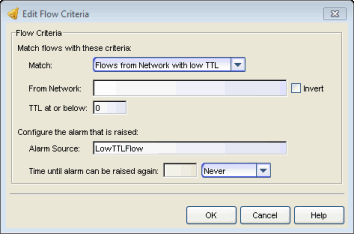
Use the drop-down menu to select the way the flow is matched for a flow alarm to be triggered, and then specify the corresponding values in the fields below.
- Flows from Network - Match a flow's source IP address to the specified network.
- Flows to Network - Match a flow's destination IP address to the specified network.
- Flows from Network from Port - Match a flow's source IP address and port number to the specified network and port.
- Flows from Port to Network - Match a flow's source port number and destination IP address to the specified port and network.
- Flows from Network with low TTL - Match a flow's source IP address and TTL value to the specified network and the "TTL at or below" value.
A network is identified as a set of IP masks. The mask is used as a filter to define a range of IP addresses. Masks can be entered in CIDR or dotted-decimal format.
- CIDR - CIDR format uses a slash followed by a number between 8 and 32, to define the number of contiguous, left-most "one" bits that define the network mask. For example, /16 indicates a 16-bit mask. Here is an example of a From/To Network value using the CIDR format:
10.20.30.0/16,10.20.80.0/24- Dotted-Decimal - Dotted decimal format represents network masks as four octets separated by periods. For example, a 16-bit mask in dotted decimal notation is 255.255.0.0. Here is an example of a From/To Network value using the dotted-decimal format:
10.20.30.0/255.255.0.0,10.20.88.0/255.255.255.0
For example, if you entered either 10.20.0.0/16 (CIDR) or 10.20.0.0/255.255.0.0 (Dotted-Decimal) in the From/To Network field, then all incoming packets in the range 10.20.00.00 through 10.20.255.255 would result in an address match.
If you select the Invert checkbox, it will be considered a match if the flow criteria does not match the specified values.
From Port
Enter the port number to be matched.
If the TTL value in the packet's TTL field is equal to or less than the value entered here, then the TTL criteria is a match.
Enter a phrase to be used as the source of the alarm, when the alarm is raised.
Time until alarm can be raised again:
Use this field to configure time-based suppression of the flow alarm. Once the alarm is triggered, it will not be triggered again until the specified time has passed. This prevents a large number of alarms being triggered, if many flows match the alarm criteria. If you select "Never", the alarm will only trigger one time. Once you manually clear the alarm, it can be triggered again.
For information on related windows:
For information on related tasks: