The NAC Assessment Deployment Guide describes a phased approach to introducing assessment into your Extreme Access Control deployment. A phased approach minimizes disruptions to your enterprise, introduces end users to remediation procedures gradually, and increases your understanding of the strengths and weaknesses in the network. While the phased approach described in this document is not required, it is the recommended way to approach implementing assessment in your network.
The guide also provides information on NAC Manager tools used to monitor and evaluate assessment results and provide data on overall network health. In addition, the guide includes a section with assessment diagnostic and troubleshooting information, including options for disabling assessment if the need should arise.
The following topics are discussed:
- Overview
- Phased Deployment
- Agent-less Assessment
- Agent-Based Assessment
- Combined Agent-less and Agent-Based Assessment
- Monitoring Assessment Results
- Diagnostics and Troubleshooting
Overview
This section provides an overview of the phased approach to assessment deployment and gives a brief introduction to the three phases. It also discusses concepts important to understanding how assessment works, such as how assessments are scored, where to view assessment results, and how end users are notified of assessment results.
Phased Deployment
The assessment phased deployment lets you introduce assessment into your Extreme Access Control deployment in three distinct phases, with each new phase increasing the overall security of your network. Each phase provides the groundwork for the next phase, allowing for a smooth transition to a stricter level of network security enforcement.
The three assessment phases are:
- Informational Assessment
End-systems connecting to the network are assessed for security compliance. The assessment results are reported, but no action is taken against end-systems with vulnerabilities. This allows you to use assessment as a data-gathering mechanism without end-systems being quarantined. - Warning Assessment
End-systems connecting to the network are assessed for security compliance. The assessment results are reported, and end-systems with vulnerabilities are notified. End users are provided with the means to remediate their vulnerabilities and achieve compliance, however end-systems which are not compliant can still access the network. - Quarantine Assessment
End-systems connecting to the network are assessed for security compliance. The assessment results are reported, and end-systems with vulnerabilities are quarantined. End users are provided with the means to remediate their vulnerabilities and achieve compliance. Only end-systems which are compliant can access the network.
This table provides a summary of the capabilities provided by each of the three assessment phases.
| Informational | Warning | Quarantine | |
|---|---|---|---|
| End-systems are assessed. | √ | √ | √ |
| Results are collected for analysis. | √ | √ | √ |
| End users are notified of vulnerabilities. | √ | √ | |
| End users are provided with remediation tools. | √ | √ | |
| Network access is denied to non-compliant end-systems. | √ |
How Assessments are Scored
When an assessment is performed on an end-system, a health result is generated. For each health result, there may be several health result details. A health result detail is a result for an individual test performed during the assessment. Each health result detail is given a score ranging from 0.0 (no risk) to 10.0 (high risk). The sum of all of the health result detail scores is the health result's total score. The greatest health result detail score is the health result's top score. These two values are measures of the end-system's over-all risk level. NAC Manager uses this risk level to determine whether or not the end-system will be allowed on the network or denied access (quarantined).
In NAC Manager, assessment tests are assigned a scoring mode which determines whether the resulting health result detail is applied towards the quarantine decision, or is used only for informational or warning purposes. Informational health result details can be used to gather information about the security risks on your network, while warning health result details allow you to notify end users when they have security risks that should be remediated. Informational or warning health result details have scores, however these scores are not considered when calculating the total score or top score. Therefore, informational or warning health result details do not impact the end-system's overall risk level.
An end-system's actual score is the sum of all of the health results, including informational and warning results. It is what the total score would have been if all the health result details had been applied. The actual score lets you see what the impact to end-system would be if informational health results are applied towards the quarantine decision.
For example, let's say an assessment is performed on an end-system, producing the following four health result details:
| Health Result Detail | Scoring Mode | Score |
|---|---|---|
| #1 | Apply Score | 1.0 |
| #2 | Apply Score | 3.0 |
| #3 | Informational | 2.0 |
| #4 | Warning | 3.0 |
The health result summary for the end-system would be:
Total Score 4.0 (Health Result Detail #1 plus #2)
Top Score 3.0 (Health Result Detail #2)
Actual Score 9.0 (Total of all health result details)
This table provides a summary of the capabilities provided by each of the three scoring modes.
| Informational | Warning | Apply Score | |
|---|---|---|---|
| Health result is recorded. | √ | √ | √ |
| Contributes to total score and top score. | √ | ||
| Considered in the quarantine decision. | √ | ||
| End user is notified. | √ | √ | |
| Contributes to actual score. | √ | √ | √ |
Viewing Health Results
You can view health result summaries and health result details information several places in NAC Manager. In the End-Systems tab, you can use the Health Result Details tab to view health result details for each end-system.
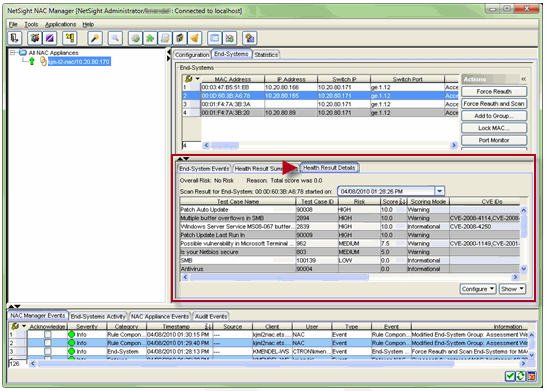
You can use the Health Result Summaries tab to view the total score and top score for each health result.
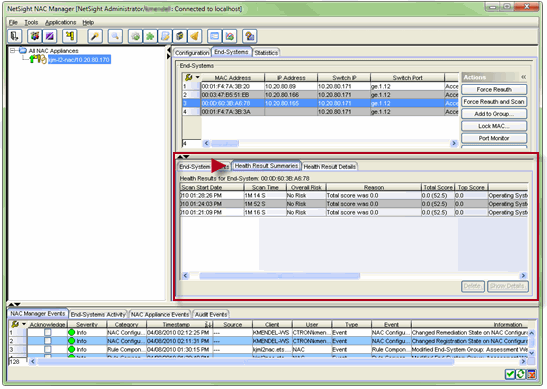
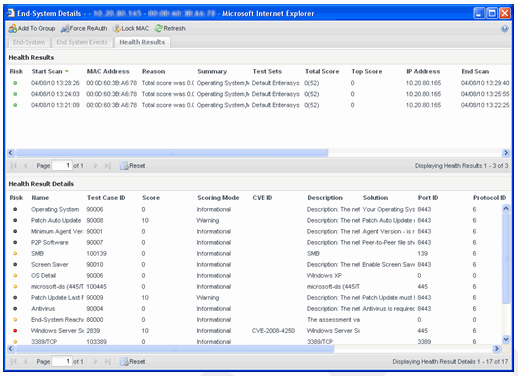
You can also access health result details and summary information in the Health Results tab of the End-Systems Details window.
End User Notification
NAC Manager uses a web portal to notify end users of assessment violations and provide remediation information. The assessment notification can take the form of a quarantine notification or a warning notification, depending on the assessment configuration. If you are using agent-based assessment, the agent can be used to notify end users of assessment violations via a desktop notification instead of the web portal.
Web Portal Notification
Here is how quarantine and warning notifications are handled by the web portal:
Quarantine Notifications: If an end-system is quarantined due to its overall risk level, it cannot access the network and all web page requests are redirected to the web portal. Through the web portal, the end user is notified of the end-system's violations that have caused the quarantine. Remediation information is provided so that end users can clear the violations. When violations are cleared, and the end-system has passed another scan, the end-system can gain access to the network. In the image below, the web portal informs an end user of the end-system's security violations and presents remediation information so the end user can repair the violations and reattempt network access.
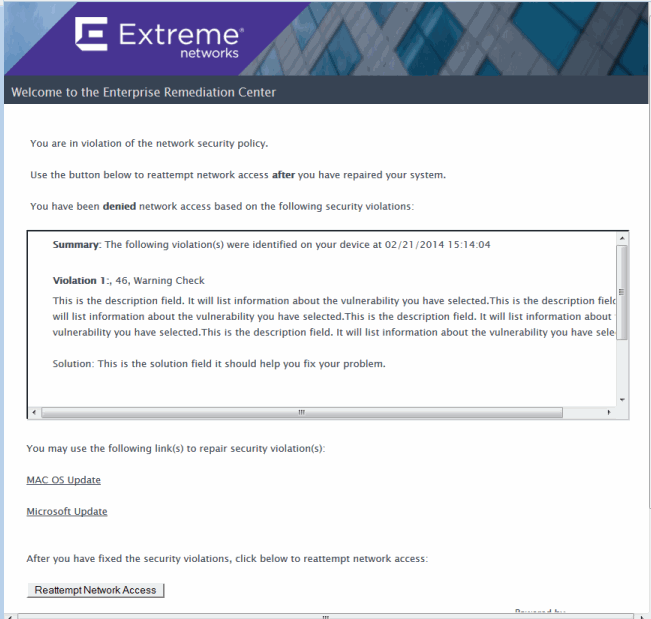
Warning Notifications: If an end-system has any health results that are warnings, all web requests are redirected to the web portal. Through the web portal, the end user is notified of the end-system's violations that have caused the warnings. Remediation information is provided so that the end user can repair the violations. The user only needs to acknowledge they have seen the warning notification. Once they do so, the end-system can gain access to the network. In the image below, the web portal informs an end user that they are in violation of network security policy, but is granted network access.
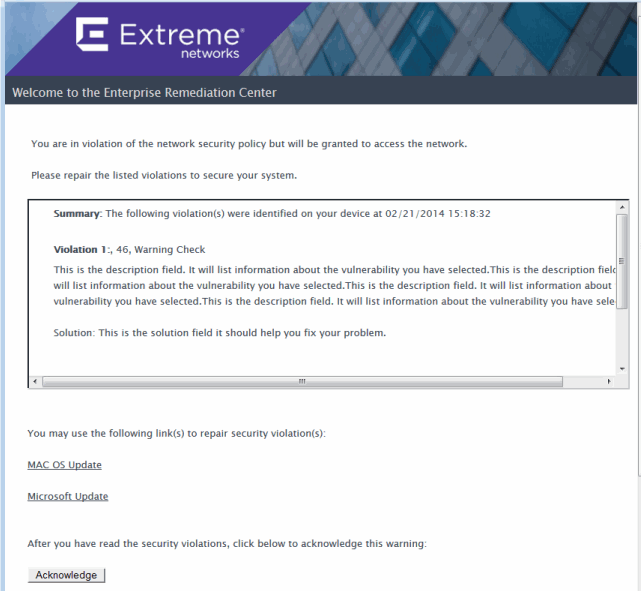
Agent Notification
If your Extreme Access Control deployment uses agent-based assessment, the agent can be used to notify end users of assessment violations and provide remediation information. The information is displayed in an agent window on the desktop instead of the web portal remediation page. This allows remediation to take place with less hits to the portal remediation web server. (However, if the end user opens a browser window, they will still get the portal remediation web page.) You must have the Allow Agent Remediation option enabled in the Advanced Agent Configuration window and the Display Agent Notification Messages option enabled in the Edit Agent-Based Test Set window to use this feature. For more information on agent notifications see How to Deploy Agent-Based Assessment.
Here is how quarantine and warning notifications are handled by the agent:
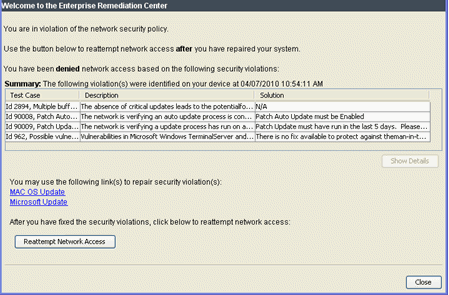
Quarantine Notifications: From a Quarantine Notification message or the agent icon, the end user can retrieve the list of violations that have caused the quarantine. Remediation information is provided so that end users can repair the violations. When violations are repaired and the end-system has passed another assessment, the end-system is allowed access to the network.
A sample agent remediation window for a Quarantine is shown below:
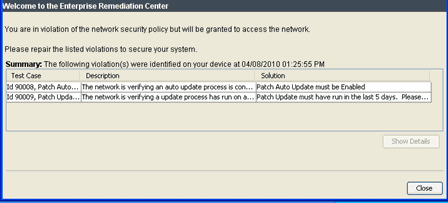
Warning Notifications:From a Warning Notification message or the agent icon, the end user can retrieve the list of violations that have caused the warnings. Remediation information is provided so that end users can repair the violations. The agent automatically acknowledges the warnings on behalf of the user, and the end-system immediately gains access to the network.
A sample agent remediation window for a Warning is shown below:
Phased Deployment
This section describes the three assessment phases and how they build on each other to provide a complete NAC assessment solution. The first phase implements informational assessment that provides a view into the security risks currently on your network. The second phase provides additional functionality allowing you to warn end users of security violations and provide remediation, while still allowing network access to all end users. The third phase provides the ability to quarantine non-compliant end-systems until they have remediated their violations. This phased approach allows you to derive value from the NAC assessment solution at each step along the way.
It is recommended that a new assessment configuration is created for each phase, rather than modifying the existing assessment configuration. This allows you to easily revert back to an earlier phase at any time by changing the assessment configuration that your NAC profile is using.
Informational Assessment
An Informational assessment will collect health results for the end-systems on your network, but will not use the health results to quarantine end-systems. This allows you to use assessment as a way to gather data about the security risks present on your network without denying end-systems access to the network. As data for end-systems is collected, you can use the NAC Manager search and reporting tools to gauge your overall network risk and identify frequently occurring vulnerabilities. See Monitoring Assessment Results for information on these tools.
When you create an Informational assessment configuration, all health results are configured with an Informational scoring mode. End-systems connecting to the network will be assessed, and health results will be collected over time. All end-systems will be considered to have no risk, and no end-systems will be quarantined.
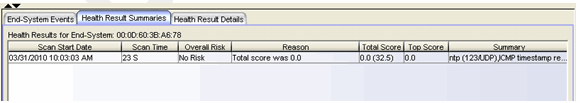
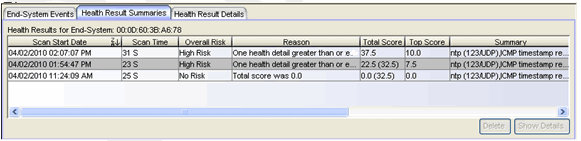
The Health Result Summaries tab (shown below) will always show an overall risk of No Risk, a total score of 0.0, and a top score of 0.0. This is because all test results are considered informational and none are applied toward risk assessment. The actual score is shown in parentheses next to the total score, showing what the total score would have been if all the health result details had been applied towards risk assessment.
The Health Result Details tab (shown below) will show all the test results collected during an assessment and all the scores for each test. You may find low, medium, or high risk test results. The scoring mode will be Informational for all test results.
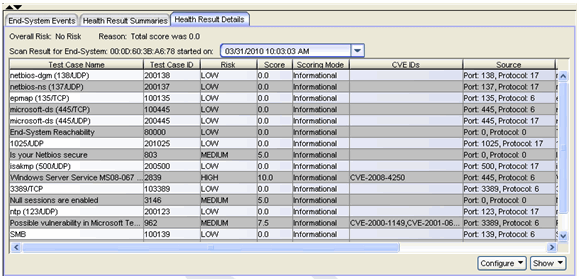
Warning Assessment
After you have collected Informational assessment results over a period of time, you can use NAC Manager's search and reporting tools to identify the top vulnerabilities that end users need to address. If enough end users have the top vulnerabilities, it may not be feasible to quarantine all the end-systems with these problems. A better strategy would be to warn end users that a problem was found with their end-system that needs to be addressed. Over time, as end users remediate their end-systems, the number of end-systems with the problem should diminish.
When you create a Warning assessment configuration, all health results that must be remediated will be configured with the Warning scoring mode, while all other health results will be configured with the Informational scoring mode. Like the Informational assessment configuration, all end-systems will be considered to have no risk, and no end-systems will be quarantined.
The Health Result Details tab (shown below) will show all the test results collected during an assessment and all the scores for each test. The scoring mode column will display whether the health result detail was informational or a warning.
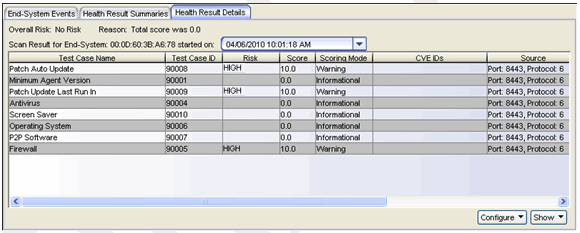
After assessment, users are warned of specific violations through the notification portal web page. When they acknowledge these notifications, they can continue accessing the network. If warnings are delivered to the desktop through the agent, the agent will present the violations and the remediation information on the desktop. The user does not need to use the web portal.
As users remediate their violations, the number of end-systems having violations will decrease, and new top vulnerabilities will be exposed. In addition, new tests can be added to the assessment configuration to provide more information on vulnerabilities. Warnings can be added for these new vulnerabilities as they are found, so that end users will remediate them. As this process continues, your overall network risk is reduced.
As an option, you can specify a time limit (called a Grace Period) for the end user to remediate their violations. If the end user does not correct the violations within the specified time limit, they are quarantined. Once the end user remediates the problems, they are removed from quarantine and allowed access to the network.
Because Warning assessment provides end-system remediation, you must enable remediation in your NAC Configuration to activate the web portal, and configure the Portal Configuration correctly to allow remediation of the vulnerabilities that you are warning the user about. For example, be sure that the Remediation Links and Custom Remediation Actions subtabs in the Assessment/Remediation section are sufficient for remediating the vulnerabilities that are of concern.
Quarantine Assessment
With Warning assessment, your network continues to face risk because end-systems with vulnerabilities are still allowed access on the network while they work to remediate their violations. To take the next step in security, you can use a Quarantine assessment configuration that immediately quarantines end-systems that are assigned a high risk level. This means that all health result scores are applied to the determination of the end-system's overall risk level, and end-systems are quarantined based on that risk level.
Before creating a Quarantine assessment configuration, review the scores and risk levels of common vulnerabilities seen in your network, and the end-systems that score highest on actual score. This should provide you with a good idea of how many end-systems would be quarantined if a Quarantine assessment configuration is deployed, and which users would be affected. The default Risk Level Configuration specifies the following high risk criteria:
- Any end-systems with a high-risk vulnerability (score of 7.0 or more) will be quarantined. This includes any end-system failing an agent-based test (score 10.0).
- Any end-systems with an actual score of 20.0 or more will be quarantined.
If you determine that the number of end-systems that would be quarantined would be disruptive to your enterprise, then you can continue with the Warning assessment configuration. Consider increasing the number of warning vulnerabilities or enabling a grace period (or decreasing the grace period time if you already have a grace period in effect) in order to encourage more compliance.
When you create a Quarantine assessment configuration, all health results will be configured with the Apply Score mode. End-systems will be assessed for risk on a scale of High Risk to No Risk, with High Risk end-systems being quarantined.
As an alternative, you can create scoring overrides for certain health results. For example, some health results can be made informational and other can continue to be warnings. This way, if there are specific vulnerabilities that you consider to be of no concern or that you wish to consider as warnings, you can still deploy a Quarantine assessment configuration and use scoring overrides to tailor how certain exceptions are handled.
Scoring overrides can also be used to adjust the scores of health results. For example, a vulnerability which scores 10 and is considered a high-risk can be changed to score 6 and be considered medium risk. This approach can be used if excluding the result altogether is not desired. Note that this affects how the vulnerability is categorized in searches and reports: if a vulnerability is rescored to be medium risk, it will appear as medium risk in all searches and reports as well.
The Health Result Summaries tab (shown below) will always show the overall risk, total score, and top score for the assessment. When every vulnerability found during assessment is applied to risk assessment, then the total score is always the same as the actual score, and the health result summary will display only a single score in the Total Score column. However, if end-systems have any vulnerabilities that are configured with scoring overrides as Informational or Warning, then the total score will be less than the actual score, and the actual score will be shown in parentheses next to the total score.
Over time, the Quarantine assessment configuration may need occasional adjustment. As high-risk vulnerabilities are discovered, you can use NAC Manager features such as scoring overrides to tailor how end-systems with these vulnerabilities should be treated: immediate remediation through quarantine, eventual remediation through assessment warnings, or no remediation. No remediation may be the proper choice:
- if a high-risk vulnerability poses no risk in your environment, due to the use of firewalls or other tools to defend your network. In this case, you may choose to ignore the vulnerability or change the score to 0.0.
- if the vulnerability is addressed by updates pushed out to end-systems by the network administrator, or if it otherwise requires an administrator to remediate. In this case, you may not want to quarantine end-systems until administrators have had sufficient time to update the end-system.
Because Quarantine assessment provides end-system remediation, you must enable remediation in your NAC Configuration to activate the web portal, and configure the Edit Portal Configuration window to allow remediation of the vulnerabilities for which a user is quarantined.
Agent-less Assessment
This section describes how to implement the three assessment phases for an assessment configuration using an agent-less test set. With agent-less assessment, the scoring mode used for all agent-less assessment tests is configured in the Agent-less Test Set window. Scoring overrides are used to change the scoring mode for specific test cases.
Agent-less Informational Assessment
To create an Informational assessment configuration, set the scoring mode in the agent-less test set to Informational. The Scoring Override Configuration selected for the assessment configuration should have no scoring overrides configured. You may wish to initially use a lighter, less exhaustive set of tests, and then change to more exhaustive tests after some time has passed. This will allow you to begin by dealing with a smaller set of results, and after you have addressed these issues, you can expand the test set to include more vulnerabilities.
Agent-less Warning Assessment
To create a Warning assessment configuration, set the scoring mode in the agent-less test set to Informational and add scoring overrides to your Scoring Override Configuration for each test case that should be a warning.
Initially, configure Warning scoring overrides for your most frequent and severe vulnerabilities. Add additional scoring overrides for more vulnerabilities over time. You can easily add Warning scoring overrides from the Health Result Details tab, as you view the health results of an end-system.
At some point, you may wish to invert your assessment configuration and scoring overrides. Rather than having a base scoring mode of Informational with scoring overrides for Warnings, you can have a base scoring mode of Warning with scoring overrides for Informational. In other words, instead of specifically calling out which tests are warnings, you call out which tests aren't. (Tests that score 0.0 will not generate warnings.)
Agent-less Quarantine Assessment
To create a Quarantine assessment configuration, set the scoring mode in the agent-less test set to Apply Score. Create a new Scoring Override Configuration and add scoring overrides for any vulnerabilities that you wish to have as exceptions. You can configure these scoring overrides to be Informational or Warning, or you can change the score. You can easily add scoring overrides from the Health Result Details tab, as you view the health results of an end-system.
Agent-Based Assessment
This section describes how to implement the three assessment phases for an agent-based assessment configuration. With agent-based assessment, the scoring mode used for each test result is configured directly in the test case. Scoring overrides are not used, except to configure how the "No Agent Detected" health result is handled.
No Agent Detected
Agent-based assessment requires an agent to be installed and running on end-systems in order to assess their risk. If no agent is running at the time of assessment, this will result in a high-risk "No Agent Detected" health result, which will quarantine the end-system. This health result must be handled specially, because no useful assessment results can be collected unless agents are installed and running on end-systems.
There are several ways that the "No Agent Detected" result can be handled.
- Quarantine end-systems that are not running the agent. End-users are redirected to the portal web page where they must download and start the agent in order to gain access to the network. This is the default behavior; nothing needs to be configured.
- Warn end-systems that are not running the agent. End-users are redirected to the portal web page where they are notified that they should download and start the agent soon. Once they acknowledge the warning they are allowed access to the network. To do this, add a Warning scoring override for Test ID 90000 to your Scoring Override Configuration.
- Do nothing to end-systems that are not running the agent. This method should be used if the agent is installed on end-systems by the network administrator and the end-user does not need to take any action. To do this, add an Informational scoring override for Test ID 90000 to your Scoring Override Configuration.
If the "No Agent Detected" result causes quarantine, users are redirected to the portal web page where they must install the agent in order to access the network. A link to install the agent is provided. Once the end user installs the agent, they will be rescanned. This will generate a new set of health result details for the end-system.
If the "No Agent Detected" result causes a warning, users are redirected to the portal web page where they are notified of their violation. Once they acknowledge the warning they can continue accessing the network. A link to install the agent is provided. When the end user installs the agent, they will be rescanned. This will generate a new set of health result details for the end-system.
Agent-Based Informational Assessment
To create an Informational assessment configuration, configure all test cases defined in the agent-based test set to have a Test Status of Informational. You may wish to begin with a smaller list of tests, and then add more tests after some time has passed. This will allow you to deal with a smaller set of results, and after you have addressed these issues, you can expand the test set to include more tests.
There are two basic types of assessment results found during this phase: results from end-systems that are running the agent and results from end-systems that are not.
For end-systems that are running the agent, the Health Result Details tab shows all the tests run, and all their scores. You may find passing (score 0.0) or failing (score 10.0) test results. The scoring mode will be Informational for all of them.
End-Systems that are not running the agent will have a single "No Agent Detected" health result detail, as shown below. It may have a scoring mode of Applied (quarantine), Warning, or Informational, depending on your configuration. You can measure your network's overall compliance with running the agent by searching for end-systems displaying this result (Test ID 90000). Use the search and reporting tools described in the Monitoring Assessment Results section.
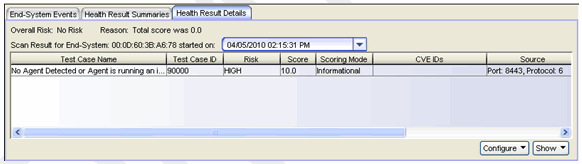
Agent-Based Warning Assessment
To create a Warning assessment configuration, start by configuring all test cases defined in the agent-based test set to have a Test Status of Informational. Then, for each test case that should be a warning, change the Test Status to Warning.
Initially, configure Warning test cases for your most frequent and severe vulnerabilities. Then, configure more test cases to be Warning over time. You can easily change the test status for agent-based test cases from the Health Result Details tab, as you view the health results of an end-system.
When you move to an agent-based Warning assessment, you may want to change how the "No Agent Detected" health result is handled. See the No Agent Detected section for more information.
You may also want to use the agent to warn end users of assessment violations and provide remediation information. To do this, you must have the Allow Agent Remediation option enabled in the Advanced Agent Configuration window and the Display Agent Notification Messages option enabled in the Edit Agent-Based Test Set window. For more information, see the Agent Notification section.
Agent-Based Quarantine Assessment
To create a Quarantine assessment configuration, configure all test cases defined in the agent-based test set to have a Test Status of Mandatory. You can make exceptions for individual tests that you wish to execute but exclude from risk assessment, by making those test cases Informational or Warning. You can easily change the test status for agent-based test cases from the Health Result Details tab.
When you move to an agent-based Quarantine assessment, you may want to change how the "No Agent Detected" health result is handled. See the No Agent Detected section for more information.
You may also want to use the agent to display assessment violations and provide remediation information instead of the portal web pages. To do this, you must have the Allow Agent Remediation option enabled in the Advanced Agent Configuration window and the Display Agent Notification Messages option enabled in the Edit Agent-Based Test Set window. For more information, see the Agent Notification section.
Combined Agent-less and Agent-Based Assessment
This section describes how to implement the three assessment phases for a combined agent-less and agent-based assessment configuration. A combined assessment includes both an agent-less test set and an agent-based test set in the assessment configuration. Each test set is configured independently. Assessment health results will contain both agent-less and agent-based results.
Combined Informational Assessment
To create a combined Informational assessment configuration, use the instructions for creating an agent-less Informational assessment and an agent-based Informational assessment as described above. You must also configure the "No Agent Detected" health result, as described above.
There are two basic types of assessment results found during this phase: results from end-systems running the agent, and results from end-systems that aren't. For end-systems running the agent, the Health Result Details tab shows all the tests that were run, and all their scores. The scoring mode is Informational for all of them.
End-Systems not running the agent display results for agent-less tests, and also a "No Agent Detected" result, as shown below. The "No Agent Detected" result may have a scoring mode of Applied, Warning, or Informational, depending on your configuration. You can measure your network's overall compliance with running the agent by searching for end-systems displaying this result (Test ID 90000). Use the search and reporting tools described in the Monitoring Assessment Results section.
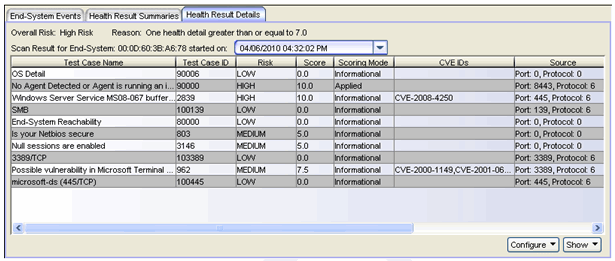
If the "No Agent Detected" result causes a quarantine or a warning, the user is notified through the portal web page, where they can download an agent, as described in the No Agent Detected section above. When end-systems download, install, and start the agent, they will be rescanned. This will generate a new set of health results.
Combined Warning Assessment
To create a combined Warning assessment configuration, use the instructions for creating an agent-less Warning assessment and an agent-based Warning assessment as described above. You must also configure the "No Agent Detected" health result, as described above.
When the user is redirected to the portal for notification, the list of violations presented will include warnings for both agent-less and agent-based results. Similarly, warnings for both agent-less and agent-based results can be delivered through agent notification.
Combined Quarantine Assessment
To create a combined Quarantine assessment configuration, use the instructions for creating an agent-less Quarantine assessment and an agent-based Quarantine assessment as described above. You must also configure the "No Agent Detected" health result, as described above.
When the user is redirected to the portal for remediation, the list of violations presented will include both agent-less and agent-based results. Similarly, violations for both agent-less and agent-based results can be delivered through agent notification.
Monitoring Assessment Results
This section describes how you can use NAC Manager's search functionality and statistical reports to help gauge your overall network security compliance and identify frequently occurring vulnerabilities. You can then use this information to modify your assessment configuration as needed.
Search by Assessment Results
You can access the
NAC Manager assessment-related searches using the Tools > Search for End-Systems by Assessment Results
menu option.
In addition, the NAC End-Systems View provides the same
search functionality, accessed from the Search for End-Systems by Assessment
button ![]() .
.
There are several search options provided. You can search by:
- Highest Test Case Scores to Lowest - Displays end-systems sorted according to their highest individual test case score (from the Health Result Details tab), listing the most vulnerable end-system with the highest score first. This search is only useful for Quarantine assessment because only applied scores count towards the high score.
- Highest Total Health Result Scores to Lowest - Displays end-systems sorted according to their total health result score (from the Health Result Summaries tab), listing the most vulnerable end-system with the highest total score first. This search is only useful for Quarantine assessment because only applied scores count towards the total score.
- Highest Total Health Result Actual Scores to Lowest - Displays end-systems sorted according to their actual health result score (from the Health Result Summaries tab), listing the most vulnerable end-system with the highest actual score first. The actual score is what the total score would be if all the health details were included as part of the quarantine decision, including those marked Informational and Warning.
- Selected Test Case - Searches for end-systems where a specific agent-based test case and score are part of their latest assessment results. This search can be used with Informational, Warning, and Quarantine assessments, however it is not useful for agent-less health results. In the Score field, use a score criteria to find only end-systems that pass or fail the test or use Score Any to find all end-systems that have a test result, pass or fail. This search is particularly useful for finding end-systems which are not running the agent, by searching for the Test Case "Agent Status - ID: 90000."
- Test Case ID - Searches for end-systems where a specific test case ID and score are part of their latest assessment results. This search can be used with Informational, Warning, and Quarantine assessments. For agent-based tests, use a score criteria to find only end-systems that pass or fail the test or use Score Any to find all end-systems that have a test result, pass or fail.
- Outstanding Warnings - Searches for end-systems that have received warnings and have acknowledged them, but have not yet cleared them.
- Unacknowledged Warnings - Searches for end-systems that have received warnings and have not yet acknowledged them.
In order to display the most current data, searches are limited to information from the latest assessment results for each end-system. Search results are displayed in the End-Systems tab, presented as a separate window.
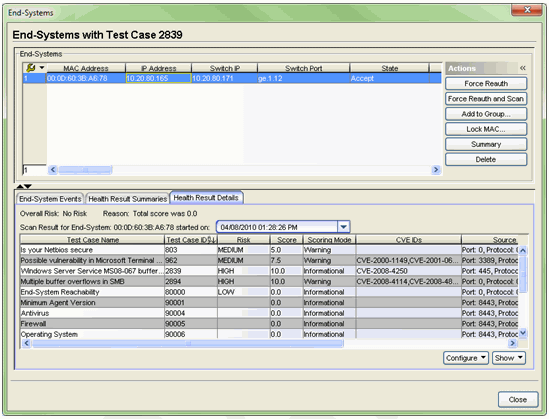
Statistical Reports
The right-panel Statistics tab presents end-system connection state statistics and vulnerability status information. For example, the End-System State chart (shown below) can show you the number of end-systems in the quarantine state.
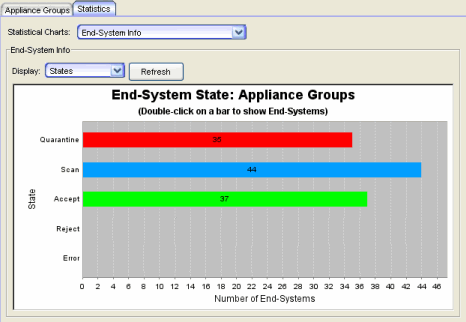
The following statistical charts can provide valuable information with evaluating the overall network risk. For more information on each chart, see the Statistics tab Help topic.
- End-System Info - The States sub-option displays the number of end-systems in the quarantine state. Click on the red Quarantine bar to view the end-systems which are quarantined.
- End-System Status - This chart will show you the percentage of end-systems in quarantine. Click on the red Quarantine section to view the end-systems which are quarantined.
- Most Frequently Occurring Vulnerabilities - Use this report to see which agent-less vulnerabilities are most prevalent on your network. There are sub-options to display only High Risk, Medium Risk, or Low Risk vulnerabilities. You can click on each vulnerability that is found to see which end-systems are currently reporting that vulnerability. This is useful with Informational and Warning assessment, as well as Quarantine assessment.
- End-System NAC Profile Allocation - This chart will show any end-systems that are assigned the Notification NAC Profile. These are end-systems with unacknowledged notifications. Click on the Notification section to view the end-systems which have unacknowledged notifications.
Control Dashboard
The Control tab in Management Center provides reports on end-system connection and assessment. For more information on these reports, see the Control tab Help topic.
Diagnostics and Troubleshooting
This section describes the tools available in NAC Manager to help diagnose and troubleshoot problems that may occur during the assessment process.
Analyze Health Results
Problems with assessment can sometimes be resolved by examining the collected health results displayed in the Health Result Summaries and Health Result Details sub tabs in the End-Systems tab. Looking through the health results, you can determine how often end-systems are assessed, which health results are causing an end-system to be quarantined, and which health results have changed over time. You can use the NAC Manager search and reporting tools to analyze health results across the entire network. See the Monitoring Assessment Results section for more information on these tools.
End-System Events
The End-System Events subtab in the End-Systems tab can often provide useful information about assessment. The tab displays events for each time an assessment is started and completed, showing when assessments have occurred, changes to the end-system after it was assessed, and whether any assessments are stuck or have been aborted.
Screen Preview
The Registration Administration web page, available on each Extreme Access Control engine, provides a Screen Preview feature that allows you to view the Warning notification page for any end-system. In the Screen Preview web page, enter the end-system's IP address and click the View for End-System button to see the portal web page that the end user would see. Using this view you can actually help the end-system remediate their violations. You can access the Screen Preview web page at https://<Access Control Engine Name or IP address>/screen_preview.
Extreme Access Control Engine Administration
To access status and diagnostic information for an Extreme Access Control engine, launch the Access ControlEngine administration web page by right-clicking on an Access Control engine in the left-panel tree and selecting WebView. (You can also access the administration web page using the following URL: https://<Access ControlEngineIP>:8444/Admin.) The default user name and password for access to this web page is "admin/Extreme@pp."
In the administration web page left-panel tree, expand the Status folder and the Log Files folder to view reports that provide assessment diagnostic information:
- Agent-Based - Displays information about the agent-based clients connected to NAC. Click the Show All button to display all connected agents.
- Assessment - Provides performance information related to NAC assessment.
- Captive Portal - Provides debug information for the web portal including statistics on the number of requests served and the interaction with Extreme Management Center.
- Agent Logs Tab - Displays the agent log files that have been retrieved from remote end-systems via the Client Diagnostics section on the Agent-Based tab page.
For more information, see the Access Control Engine Administration Web Page section of the NAC Deployment Guide.
Log Files
Extreme Access Control engine log files can also provide useful diagnostic information for assessment. You can enable diagnostics for assessment by going to the Access Control engine administration web page and enabling diagnostic groups that provide troubleshooting information. Launch the Access Control engine administration web page by right-clicking on the Access Control engine in the NAC Manager left-panel tree and selecting WebView or by using the following URL: https://<Access ControlEngineIP>:8444/Admin. The default user name and password for access to this web page is "admin/Extreme@pp."
Expand the Diagnostics folder in the left-panel tree and click on the Appliance/Server Diagnostics page. There are several useful diagnostic options to enable including:
- Assessment
- Assessment - Agent Based Connection Interaction
- Captive Portal - Authentication
- Captive Portal - Display
- Captive Portal - Processes and Configuration
- Captive Portal - Registration Administration
- Captive Portal - Registration and Remediation
View the debug information in the Access Control engine administration web page under the Log Files > Server Log tab or in /var/log/tag.log file on the Access Control engine. The assessment agent process has its own log file which can be found in /opt/nac/saint/logs/ on the Access Control engine.
For more information, see the Access Control Engine Administration Web Page section of the NAC Deployment Guide.
Disabling Assessment
When diagnosing and troubleshooting assessment on your network, it may become prudent to disable assessment, especially if end users are experiencing problems arising from its use. In some cases, it may even be necessary to do so very quickly. There are a number of options available for disabling assessment, with different options being more appropriate at different times.
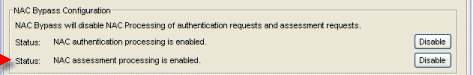
Disable Assessment on the Engine
In the NAC Manager right-panel Appliance Configuration tab, the NAC Bypass Configuration section has a Disable button that allows you to very quickly disable assessment on the selected engine. For example, if there is a problem with an assessment configuration, the Disable button lets you remotely disable assessment functionality on the engine until the problem has been resolved. You can then use the Enable button to re-enable assessment functionality. When assessment is disabled, the Extreme Access Control engine name and IP address are displayed in red text in the left-panel tree indicating that the engine is in Bypass mode.
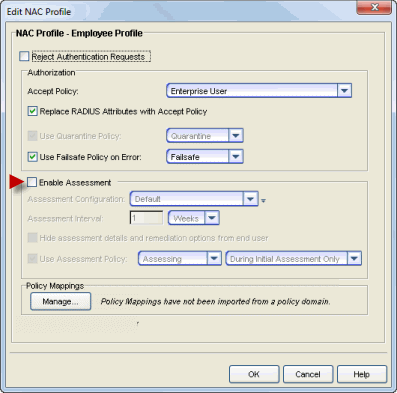
Disable Assessment in the NAC Profile
You can disable assessment for all end-systems that are assigned the same NAC Profile, by reconfiguring the NAC profile to disable assessment. To edit an existing profile, select a profile in the Manage NAC Profiles window and click the Edit button. In the Edit NAC Profile window, deselect the Enable Assessment option. This change must be enforced to your engines.
Change the Quarantine Policy
You can disable quarantine for all end-systems that are assigned the same NAC Profile, by reconfiguring the NAC profile to specify a Quarantine policy that allows network access, for example, the Enterprise User policy.
With this approach, end-systems assigned to that NAC profile are still assessed, and are still quarantined if determined to be high risk. However, being in quarantine will not affect the end user's ability to access the network, and end users will not be redirected to the portal web pages. (If you are using agent-based assessment and have agent notification enabled, the agent still reports to end-users that the end-system is quarantined.) End users already quarantined are not be affected by this change until they are re-assessed.
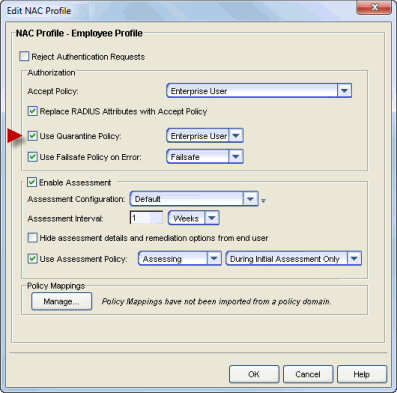
To edit an existing profile, select a profile in the Manage NAC Profiles window and click the Edit button, or use the Default Profile field in the Edit NAC Configuration window. This change must be enforced to your engines.
No Assessment End-System Group
This procedure allows you to disable assessment for certain end-systems by assigning them to an end-system group that uses a NAC Profile that does not have assessment enabled. You can create the end-system group in advance, so that it is ready to use when the need arises.
- From the Manage Rule Groups window, create an end-system group for No Assessment.
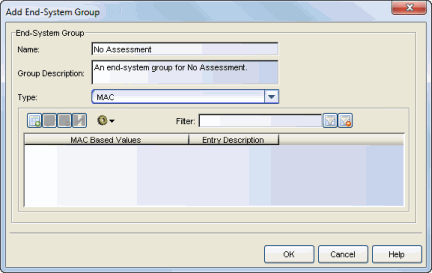
- From the NAC Configuration Rules panel, create a custom rule that assigns
end-systems in the No Assessment group to a NAC Profile
that does not enable assessment.
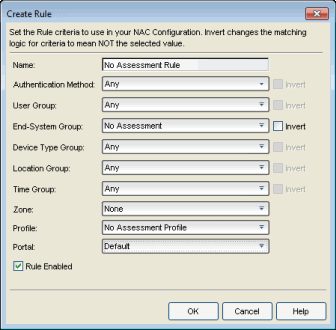
- Enforce these changes to your engines.
After you have created the end-system group, you can add an end-system to the group to disable assessment for that end-system. Remove them from the group to re-enable assessment. End-systems can be easily added and removed to and from end-system groups from the End-Systems tab.
Revert to Informational Assessment
You can revert from a Warning assessment or Quarantine assessment configuration back to an Informational assessment configuration at any time by changing the assessment configuration assigned in a NAC Profile. End-systems assigned to that profile are still assessed, but the health results will not quarantine any end-systems. You may have preserved your Informational assessment configuration from earlier use or you can prepare an alternate Informational assessment configuration to use if necessary. You can change the assessment configuration in the Edit NAC Profile window. You must enforce this change to your engines.
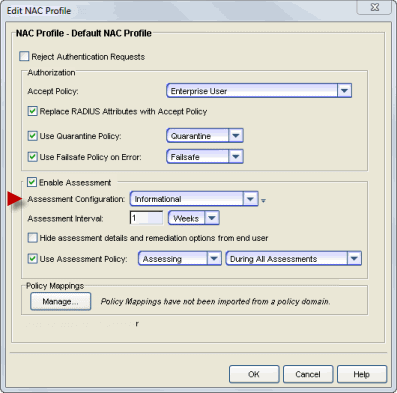
As an alternative, you can continue to use a Warning or Quarantine assessment configuration, and just change specific assessment tests to an Informational scoring mode. Agent-less test sets can be changed to Informational assessment by changing the Scoring Mode for the test set to Informational or by creating scoring overrides for specific tests. Agent-based test sets require changing the Test Status on the desired test cases to Informational.