This window lets you add or edit the user to authentication mappings that define your Advanced AAA configurations. You can access this window from the Add
or Edit buttons in the
AAA Configuration window.
| NOTE: | You can also access AAA Configurations in the Advanced
Configuration View, by selecting Tools > Management and Configuration > Advanced Configurations
from the menu bar. In the left-panel tree,
expand the AAA Configurations folder. Your configurations are listed below the
folder. |
|---|
Click areas in the window for more information.
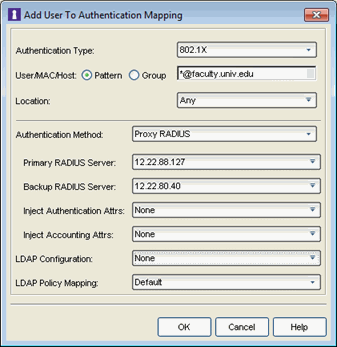
Select the authentication type that the end-system must match for
this mapping. Note that individual types of 802.1X authentication are
not available for selection because at this point in the authentication
process, the fully qualified 802.1X authentication type cannot be
determined. Select "Any" if you don't want to require an authentication match. Select 802.1X (TTLS-INNER-TUNNEL) or 802.1X (PEAP-INNER-TUNNEL) to authenticate via another RADIUS server using an inner tunnel to protect the authentication request.
The
Management Login authentication type allows you to set up a mapping
specifically for authenticating management login requests, when an
administrator logs into a switch's CLI via the console connection, SSH, or
Telnet. This allows you to send management requests to a different
authentication server than network access requests go to. This
authentication type can be used to authenticate users locally, or proxy
them to specific RADIUS or LDAP servers. Make sure that the Management
Login mapping is listed above the "Any" mapping in the list of mappings
in your Advanced AAA Configuration. In addition, you must set the Auth.
Access Type to either "Management Access" or "Any Access" in the
Add/Edit Switches window for this authentication type.
Select the Pattern radio button and enter the username, MAC address, or hostname that the end-system must match for this mapping. Or, select the Group radio button and select a user group or end-system group from the drop-down list. If you enter a MAC address, you can use a colon (:) or a dash (-) as an address delimiter, but not a period (.).
Select the location group that the end-system must match for this mapping, or select "Any" if you don't want to require a location match. You can also add a new location group or edit an existing one.
Authentication Method
Select the authentication method that the end-system must match for
this mapping:
Proxy RADIUS, LDAP Authentication, or Local Authentication.
Primary RADIUS Server - Use the drop-down menu to select the primary RADIUS server for this mapping to use.
You can also add or edit a RADIUS server, or
manage your RADIUS servers.
Backup RADIUS Server - Use the drop-down menu to select the backup RADIUS server for this mapping to use. You can also add or edit a RADIUS server, or manage your RADIUS servers.
Inject Authentication Attrs - Use the drop-down menu to select attributes to inject when proxying authentication requests to the back-end RADIUS servers. Select Edit RADIUS Attribute Settings within the drop-down menu to open the RADIUS Attribute Settings window, which allows you to add or edit an attribute group.
Inject Accounting Attrs - Use the drop-down menu to select attributes to inject when proxying accounting requests to the back-end RADIUS servers. Select Edit RADIUS Attribute Settings within the drop-down menu to open the RADIUS Attribute Settings window, which allows you to add or edit an attribute group.
LDAP Authentication - If you select LDAP Authentication, specify the LDAP configuration for this mapping to use.
Local Authentication - If desired, select the option to configure a password for all authentications that match the mapping. This option could be used with MAC authentication where the password is not the MAC address. For example, you may have MAC (PAP) authentication configured for all your switches, with the exception of MAC (MsCHAP) authentication configured for a wireless controller. For the wireless controller, you would add a new AAA mapping with the authentication type set to MAC (MsCHAP), the location set to the wireless controller location group, and the authentication method set to Local Authentication with the password for all authentications set to the static password configured on the wireless controller.
Use the drop-down list to select the LDAP configuration for the LDAP servers on your network that you want to use for this mapping. You can also add or edit an LDAP configuration, or manage your LDAP configurations. You must specify an LDAP configuration if you have selected LDAP Authentication as your authentication method. However, you might also specify an LDAP configuration if you use Proxy RADIUS to a Microsoft NPS server that is running on a domain controller. The domain controller is also an LDAP server that can do RADIUS requests and LDAP requests for users on that server.
Use the drop-down list to select the LDAP Policy Mapping for this mapping. You can also add or edit an LDAP Policy Mapping or open the Manage LDAP to Policy Mappings window. If you have selected an LDAP configuration, this option allows you to use a different LDAP policy mapping. This is useful if the LDAP configuration uses user attribute values that overlap with another LDAP configuration. For example, in the case of multiple companies where company A's Sales department uses one policy, but company B's Sales department uses a different policy.
For information on related windows: