The Manage Appliance Certificates window provides a central location for managing the security certificates for your Extreme Access Control (Access Control) engines. You can access this window by right-clicking on any engine in the right-panel Appliances tab.
| NOTE: | Extreme Management Center automatically generates alarms as the Access Control Engine Internal Communications Server Certificate, the Captive Server Portal Server Certificate, the RADIUS Server Certificate, the AAA Configuration Truststore, and the Access Control Engine Truststore approach their expiration date. Extreme Management Center generates a Notification alarm 30 days before expiring, a Warning alarm 7 days before expiring, and a Critical alarm when the certificate expires. |
|---|
The top section of the window lets you modify the engine's security certificates. During installation, server certificates are generated for each Access Control engine. While these certificates provide secure communication, there may be cases where you want to update to a certificate provided from an external certificate authority, or add certificates in order to meet the requirements of external components with which NAC Manager must communicate. Additionally, you may want to use a "browser-friendly" certificate so that users don't see browser certificate warnings when they access web pages. You can use this section to:
- View and update the Captive Portal server certificate
- View and update the Internal Communications server certificate
- View and update the certificate configuration for agent-based assessment
- View and update the RADIUS server certificate
The bottom section of the window provides information about the AAA configuration used by the engine group to which the engine belongs. You can use this section to:
- View the configured AAA authentication behavior to determine whether certificates are used in the authentication process. If your Access Control deployment is using EAP-TLS, PEAP, or EAP-TTLS authentication and the authentication requests are not proxied, certificates are used to provide secure communication between the Access Control RADIUS server and end-systems that are authenticating. However, if your authentication behavior is configured to proxy all 802.1X authentication requests, then certificates are not used.
- View and update the AAA certificate authorities that are trusted to issue client certificates for 802.1X authentication. You only need to do this if your AAA authentication behavior uses certificates.
Any changes made in this window do not take effect until the engine is enforced.
Click areas in the window for more information.
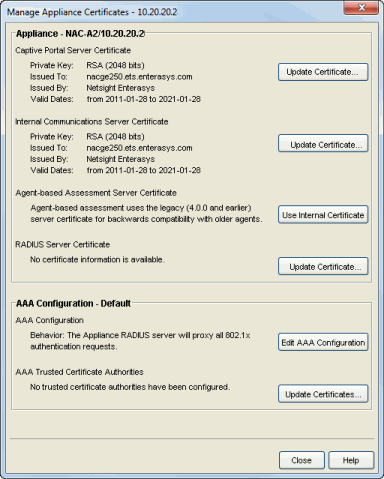
Appliance
Use this section to view the current configuration for the engine server certificates, and update the certificates, if desired. For complete instructions on replacing and verifying a certificate, see How to Update Access Control Engine Server Certificates.
- Captive Portal Server Certificate
- The Captive Portal server certificate provides secure communication for the Access Control captive portal web pages. Click Update Certificate to open the Update Captive Portal Server Certificate window where you can replace the certificate.
- Internal Communications Server Certificate
- The Internal Communications server certificate provides secure communication between components and for Access Control administrative web pages. Click Update Certificate to open the Update Internal Communications Server Certificate window where you can replace the certificate.
- Agent-Based Assessment Server Certificate
- The server certificate for agent-based assessment provides secure agent communications. Use the button to toggle between the following two
selections:
- Use Legacy Certificate - This option causes agent-based assessment to use the legacy (NAC Manager version 4.0.0 and earlier) server certificate in order to provide backward compatibility with older agents.
- Use Internal Certificate - Once agents have been upgraded, this option uses the Internal Communications server certificate for agent communications. Using the Internal Communications server certificate provides increased security and also allows you to update the certificate, if desired.
- RADIUS Server Certificate
- The RADIUS server certificate is the certificate sent to end-systems
during certain forms of 802.1X authentication (EAP-TLS, PEAP, and
EAP-TTLS). Click Update
Certificate to open the Update RADIUS Server Certificate window
where you can update to a certificate generated by a Certificate
Authority that your connecting end-systems are already configured to
trust.
NOTE: The current configuration displays "No certificate information is available" if you have not updated the RADIUS server certificate using this window, even though a certificate is generated during installation.
AAA Configuration
If your Access Control deployment is using EAP-TLS, PEAP, or EAP-TTLS authentication and the authentication requests are not proxied, you need to update your RADIUS server certificate to a CA certificate your connecting end-systems trust. In addition, you need to configure the AAA Trusted Certificate Authorities to designate which client certificates can be trusted.
This information is part of the AAA configuration and shared across all engines in an engine group. This allows end-systems to be trusted on any Access Control engine where they can authenticate.
- AAA Configuration
- This section displays the current authentication behavior configured for the engine and helps you determine whether certificates may be used during authentication. If the engine RADIUS server proxies all 802.1X authentication requests, then certificates are not used. If the engine RADIUS server can terminate 802.1X authentication requests, then certificates are used if you are using EAP-TLS, PEAP, or EAP-TTLS authentication. Use the Edit AAA Configuration button to access your AAA configuration to change this behavior.
- AAA Trusted Certificate Authorities
- Click Update Certificates to open the Update AAA Trusted Certificate Authorities window where you can create a list of trusted certificate authorities (CAs) to issue client certificates for 802.1X authentication, as well as create a list of CRL distribution points which are used to check for revoked client certificates. Changing this configuration affects all engines that use the AAA configuration.
For information on related tasks: