NAC Profiles specify the authorization and assessment requirements for the end-systems connecting to the network. Profiles also specify the security policies applied to end-systems for network authorization, depending on authentication and assessment results.
NAC Manager comes with ten system-defined NAC profiles:
- Administrator
- Allow
- Default
- Guest Access
- Notification
- Pass Through
- Quarantine
- Registration Denied Access
- Secure Guest Access
- Unregistered
If desired, you can edit these profiles or you can define your own profiles to use for your NAC configurations. Use this window to create a new profile, or edit an existing profile. When you create a new profile, it is added to the Manage NAC Profiles window. When you edit a profile, it changes the profile wherever it is used, so you do not need to individually edit each profile.
To create a new profile, click the Add button in the Manage NAC Profiles window. To edit an existing profile, select a profile in the Manage NAC Profiles window and click the Edit button.
Click areas in the window for more information.
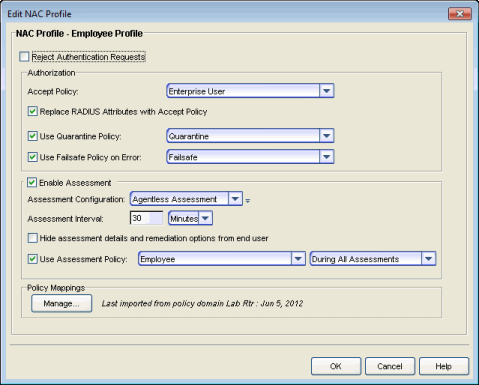
- Name
- Enter a name for a new profile. If you are editing a profile, the name of the profile is displayed and cannot be edited. To change the name of a profile, open the Advanced Configuration window (Tools > Management and Configuration > Advanced Configurations), expand the NAC Configurations folder and the NAC Profiles folder, right-click on the profile name and select Rename from the menu.
- Reject Authentication Requests
- If you check this checkbox, all authentication requests are rejected.
Authorization
- Accept Policy
- Use the drop-down menu to select the Accept policy you want to use in this
NAC profile. An Accept policy is applied to an end-system when:
- the Extreme Access Control (Access Control) engine authorizes the end-system locally (MAC authentication) and the end-system passes an assessment (if assessment in enabled).
- the "Replace RADIUS Attributes with Accept Policy" option is selected .
- If you select "No Policy", then the Access Control engine
does not include a Filter ID or VLAN Tunnel Attribute in the RADIUS
attributes returned to the switch, and
the default role configured on the port is assigned to the end-system.
This option is necessary when configuring single user plus IP phone authentication supported on
C2/C3 and B2/B3 devices.
If you select "Use User/Host LDAP Policy Mappings", then the Access Control engine uses the LDAP policy mappings you configured in NAC Manager. You can access the LDAP Policy Mappings window from the configuration menu button to the right of the drop-down menu.
| NOTE: | The Manage button at the bottom of this window opens the
Edit Policy Mapping window where you can define the policies available for selection from the drop-down menus in this window. You can also
use the window to specify the
policy to VLAN associations for RFC 3580-enabled switches. |
|---|
- Replace RADIUS Attributes with Accept Policy
- When this option is checked, the attributes returned from the RADIUS server are replaced by the policy designated as the Accept policy. If the RADIUS server does not return a Filter ID or VLAN Tunnel attribute, the Accept policy is inserted. When this option is unchecked, the attributes returned from the RADIUS server are forwarded back "as is" and the Accept Policy is only used to locally authorize MAC authentication requests. If the RADIUS server does not return a Filter ID or VLAN Tunnel attribute, no attributes are returned to the switch.
- Use Quarantine Policy
- Select this checkbox if you want to specify a Quarantine policy. The
Quarantine policy is used to restrict network access for end-systems
that failed the assessment. You must select the
Enable Assessment checkbox to
activate this checkbox.
If a Quarantine policy is not specified and you configured RADIUS in your AAA configuration, then the policy from the RADIUS attributes is applied (unless "Replace RADIUS Attributes with Accept Policy" is selected, in which case the Accept policy is used.) If "Authorize Authentication Requests Locally" is selected in your AAA configuration, then the Accept policy is applied to those locally authorized end-systems. This allows an end-system onto the network with its usual network access even though the end-system failed the assessment.
- Use Failsafe Policy on Error
- Select this checkbox if you want to specify a Failsafe policy to be
applied to an end-system when it is in an Error connection state. An
Error state results if the end-system's IP address could not be
determined from its MAC address, or if there a scanning error occurs and a
scan of the end-system could not take place. A Failsafe policy
allocates a nonrestrictive set of network resources to the connecting
end-system so it can continue its work, even though an error occurred in
Access Control operation.
If a Failsafe policy is not specified and you configured RADIUS in your AAA configuration, then the policy from the RADIUS attributes is applied (unless "Replace RADIUS Attributes with Accept Policy" is selected, in which case the Accept policy is used.) If "Authorize Authentication Requests Locally" is selected in your AAA configuration, then the Accept policy is applied to those locally authorized end-systems. This allows end-systems onto the network with their usual network access when an error occurs in Access Control operation.
Assessment
- Enable Assessment
- Select the Enable Assessment checkbox if you want to require that end-systems are scanned by an assessment server.
| NOTE: | If you require end-systems to be scanned by an assessment server, you need
to configure the assessment servers that performs the scans.
The Manage Assessment Settings window is the main window used to manage and
configure assessment servers. To access this window, select Tools > Management and Configuration > Assessment Settings
from the menu bar.
|
|---|
- Assessment Configuration
- Use the drop-down menu to select the assessment configuration to use in this NAC Profile. Use the configuration menu
button
 to
add a new assessment configuration or edit a configuration, if needed. Once an
assessment
configuration is created, it becomes available for selection in the
list.
to
add a new assessment configuration or edit a configuration, if needed. Once an
assessment
configuration is created, it becomes available for selection in the
list.
- Assessment Interval
- Enter an assessment interval that defines the interval between required
assessments:
- Minutes - 30 to 120
- Hours - 1 to 48
- Days - 1 to 31
- Weeks - 1 to 52
- None
- Hide Assessment Details and Remediation Options from User
- If you select this option, the end user does not see assessment or remediation information on the Remediation Web Page. They are informed that they are quarantined and told to contact the Help Desk for assistance.
- Use Assessment Policy
- Select this checkbox if you want to specify a certain policy to be
applied to an end-system while it is being assessed.
Use the drop-down menu to select the desired policy.
Select when to apply the policy:- During Initial Assessment Only — Only initial assessments receive the assessment policy. If the end-system is being re-assessed, it remains in its current policy.
- During All Assessments — All end-systems being assessed receive the specified assessment policy.
- If an assessment policy is not
specified and you configured RADIUS in your AAA configuration, then the policy from the RADIUS attributes is applied
(unless "Replace RADIUS Attributes with Accept Policy" is selected, in
which case the Accept policy is used.)
If "Authorize Authentication Requests Locally" is selected in your AAA configuration, then the Accept policy is applied to those locally authorized end-systems. This allows the end-system immediate network access without having to wait for assessment to be complete.
Policy Mappings
- Manage
- Opens the Edit Policy Mapping window where you can manually define the policies used for your NAC policy mappings. You can also use the window to specify the policy to VLAN associations for RFC 3580-enabled switches. The text to the right of the button is a summary of the latest management task performed on the policy mappings.
For information on related windows: