If your NAC deployment is configured for EAP-TLS, PEAP, or EAP-TTLS authentication and the authentication requests are not proxied, you will need to update your RADIUS server certificate to a CA certificate that your connecting end-systems trust. In addition, you will need to use this window to configure the AAA Trusted Certificate Authorities to designate which client certificates can be trusted.
This information is part of the AAA configuration and shared across all appliances in an appliance group. This allows end-systems to be trusted on any NAC appliance where they can authenticate. You can access this window from the Manage Appliance Certificates window or your AAA Configuration.
The information entered in this window is saved in the appliance configuration in the NetSight database and written to the appliance when it is enforced. When enforced, the RADIUS server on the appliance will be restarted automatically to load the changes. Changing this configuration affects all appliances that use the AAA configuration.
Click areas in the window for more information.
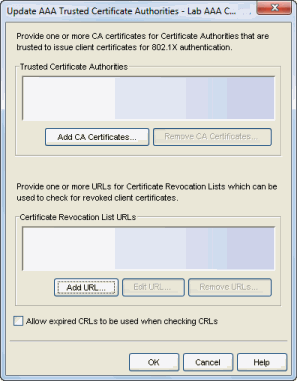
- Trusted Certificate Authorities
- Use Add CA Certificate and Remove CA Certificates to create a list of certificate authorities (CAs) that are trusted to issue client certificates for 802.1X authentication. When you add a CA, you must provide a file that contains the CA's certificate. The CA's name appears in the list.
- Certificate Revocation List URLs
- Use Add URL, Edit URL, and Remove URLs to create a list of CRL
distribution points which will be used to check for revoked client
certificates. When an end-user's access to the network has been revoked,
the end-user's client certificate is revoked.
This will cause the CA to add the revoked certificate's serial
number to its CRL. The NAC appliance will download a new copy of any
configured CRL every hour from the CRL distribution point identified by
the URL. If the CRL has been updated, the RADIUS server will be
restarted to load the new data. The RADIUS server will then
reject any client certificate found in the CRL.
When CRLs are used, there must be a CRL configured for every trusted certificate authority. Only CRLs that are distributed through an http:, https:, or file: URL are supported, and only CRLs that correspond to a listed trusted certificate authority can be used. Delta CRLs are not allowed.
- Expired CRLs
- Generally, CRLs are updated at about the same time the current CRL expires. By default, if a CRL has expired, all certificates from the corresponding certificate authority are rejected. If this option is selected, it allows the expired CRL to continue to be used until a new, updated version is downloaded.
For information on related tasks: