The End-Systems view displays end-system connection information, and lets you monitor end-system events and view the health results from an end-system's assessment. It can be accessed from the Control tab.
The End-Systems tab is the fourth tab displayed when accessing the Control tab. > A high-level overview of the functionality found in the Access Control tab is also available. For additional information, see Access Control.
In order to view the End-Systems view, you must be a member of an authorization group assigned the appropriate Extreme Management Center capabilities:
- NetSight OneView > Access OneView
- NetSight NAC Manager > OneView End-Systems Read Access or Read/Write Access
This Help topic provides information on the following table features:
- Tools Menu
- End-Systems Column Definitions
- Sorting and Filtering
- Buttons, Search Field, and Paging Toolbar
Tools Menu
Select an end-system in the table and use the Tools menu  to access the following options:
to access the following options:
- Show Details
- Opens the End-System Details browser window providing details on the selected end-system. You can also open the End-System Details window by double-clicking a row.
- Edit Custom Information
- Opens a window where you can edit the custom information fields for the end-system. You must display the Custom 1-4 fields by clicking on a column heading and using the Columns menu to enable the Custom columns.
- Lock MAC
- Opens the Add MAC Lock window where you can lock the MAC address of the selected end-system to a switch or switch and port.
- Delete
- Deletes the selected end-system entries from the table. You are given the option to delete any custom information, group assignment, MAC locks, and registration and web authentication associated with the end-systems.
| NOTES: | The Delete operation does not remove an end-system from the Blacklist group. Blacklist is a special group that requires end-systems to be manually removed using the Edit End-System Group window. Deleting an end-system from the table also deletes the user's current authentication. If the user is connected to the network at the time of the delete, they will be forced to re-authenticate. |
- PortView
- Opens the PortView sub-tab where you can view port troubleshooting information, including NetFlow data and end-system details.
- Group Editor
- Opens the Group Editor sub-tab where you can add, edit, or delete End-System, Location, and User groups. The Group Editor also includes a Find in Group function that lets you search your groups for any entry, for example: MAC address, MAC OUI, MAC Mask, IP address, Username, or Hostname.
- Search Maps
- If the end-system is connected to a switch added to a map, the Maps sub-tab opens with the end-system highlighted and centered on the map.
-
NOTE: If the switch to which the end-system is connected is part of an MLAG, both switches in the MLAG are highlighted on the map.
- Guest Access and Registration
- Opens the Registration Administration web page, where you can view registered devices and users, and manually add, delete, and modify users.
- Device Type Detection and Profiling Information
- Opens a report that includes:
-
- Device Types by DHCP - displays information related to the device types that can be determined via DHCP snooping method of device type detection. Filters can be applied to narrow down the rows related to the common device type categories.
- Other Device Types - displays information related to known device types that can be determined using methods other than DHCP snooping.
- Device Type Selectors - displays the available rule components that can be used for device type profiling. The report shows all the device type name patterns that will match each device type selector.
Column Definitions
- State
- The end-system's connection state:
 Scan - The end-system is currently being scanned.
Scan - The end-system is currently being scanned.
 Accept - The
end-system is granted access with either the Accept policy or the
attributes
returned from the RADIUS server.
Accept - The
end-system is granted access with either the Accept policy or the
attributes
returned from the RADIUS server.
 Quarantine - The
end-system is quarantined because the assessment failed.
Quarantine - The
end-system is quarantined because the assessment failed.
 Reject - The end-system was rejected because
the assigned NAC profile was set to Reject, the MAC Locking test failed, or the RADIUS server was
reachable but rejected the authentication request.
Reject - The end-system was rejected because
the assigned NAC profile was set to Reject, the MAC Locking test failed, or the RADIUS server was
reachable but rejected the authentication request.
 Disconnected - All
sessions for the end-system are disconnected. This state is only
applicable for end-systems connected to switches that have RADIUS
accounting enabled, or if the Session Deactivate Timeout option is
enabled on the Reauthentication tab in Appliance Settings.
Disconnected - All
sessions for the end-system are disconnected. This state is only
applicable for end-systems connected to switches that have RADIUS
accounting enabled, or if the Session Deactivate Timeout option is
enabled on the Reauthentication tab in Appliance Settings.
 Error - Indicates one of
nine problems:
Error - Indicates one of
nine problems:
- the MAC to IP resolution failed, if assessment is enabled
- the MAC to IP resolution timed out, if assessment is enabled
- all RADIUS servers are unreachable
- the RADIUS request was non-compliant
- all assessment servers are unavailable
- the assessment server can't reach the end-system
- no assessment servers are configured
- the assessment server is not compatible with the current version of NAC
- the username and password configured in the Assessment Server panel of the NAC Manager options (Tools > Options > Assessment Server) are incorrect for the assessment server
- MAC Address
- The end-system's MAC address. MAC addresses can be displayed as a full MAC address or with a MAC OUI (Organizational Unique Identifier) prefix. You can specify how you want to display MAC addresses in the Console options for OneView (Tools > Options).
- Switch IP
- The IP address of the switch the end-system connected to. If the end-system is connected to a NAC Controller appliance, this is the NAC Controller PEP (Policy Enforcement Point) IP address.
- Switch Port
- The port alias (if defined) followed by the switch port number the end-system connected to. If the end-system is connected to a Layer 2 NAC Controller appliance, this is the NAC Controller PEP (Policy Enforcement Point) port. However, for Layer 3 NAC Controller appliances this column will be blank.
- Risk
- The overall risk level assigned to the end-system based on the health result of
the scan:
- Red - High Risk
- Orange - Medium Risk
- Yellow - Low Risk
- Green - No Risk
- Gray - Unknown
- Reason
- Provides additional information about the reasons why the end-system is in its particular connection state. It gives you an idea as to why a certain policy was applied to the end-system or why the end-system was rejected.
- Auth Type
- Identifies the latest authentication method used by the end-system to connect to the network. (For Layer 3 NAC Controller appliances, this column lists "IP.") For a listing of all the authentication methods the end-system has used to authenticate, see the All Authentication Types column.
- State Description
- This column provides more details about the end-system state. For example, if the end-system's connection state is Reject, this column may list the RADIUS server that rejected the authentication request.
- Extended State
- Provides additional information about the end-system's connection state.
- Appliance Group
- Displays what appliance group the NAC appliance was in when the end-system event was generated. For example, if the appliance was in appliance group A when an end-system connected, but then later the appliance was moved to appliance group B, this column still list appliance group A for that end-system's entry.
- RFC3580 VLAN
- For end-systems connected to RFC 3580-enabled switches, this is the RFC3580 VLAN ID assigned to the end-system.
- Score
- The total sum of the scores for all the health details that were included as part of the quarantine decision.
- Actual Score
- The actual score is what the total score would be if all the health details including those marked Informational and Warning were included in the score.
- Switch Port Index
- The switch port index the end-system connected to. If the end-system is connected to a Layer 2 NAC Controller appliance, this is the NAC Controller PEP (Policy Enforcement Point) port index. However, for Layer 3 NAC Controller appliances this column will be blank.
- Switch Location
- The physical location of the switch the end-system connected to. If the end-system is connected to a NAC Controller appliance, this is the NAC Controller PEP (Policy Enforcement Point) location.
- All Auth Types
- This column displays all the authentication methods the end-system has used to authenticate. The authentication types are listed in order of precedence from highest to lowest: Switch Quarantine, 802.1X, CHAP, PAP, Kerberos, MAC, CEP, RADIUS Snooping, Auto Tracking. View details about each authentication session (such as the NAC profile that was assigned to the end-system for each authentication type) in the End-System Events tab. You can also view authentication session information in the End-System Summary window.
- Last Scan Result
- The last scan result assigned to the end-system: Scan, Accept, Quarantine, Reject, Error. This is the state that was assigned to the end-system as a result of the last completed scan. This will typically match the end-system State if scanning is currently enabled and has been performed recently.
- NAP Capable
- Indicates whether the end-system is Microsoft NAP (Network Access Protection) capable: Yes or No.
- Zone
Displays the end-system zone that the end-system is assigned to. For more information, see End-System Zones in the NAC Manager Concepts Help file.
- Source
-
- NAC Appliance — A NAC appliance.
- Wireless Manager — An Extreme ExtremeWireless Wireless Controller or AP.
- ExtremeXOS ID Manager — An Extreme switch running ExtremeXOS with the Identify Manager feature configured to send events to NetSight.
- OneFabric Connect — A custom project (e.g. Solutions Architecture and Innovation (SAI) integration)
- One Controller — The Extreme SDN Controller.
Displays the origin of the event:
Sorting and Filtering
Add or remove a column by clicking the down arrow at the right of a column header and selecting a checkbox associated with a column from the Columns menu. Click on the column headings to perform an ascending or descending sort on the column data.
The End-Systems table provides different types of filters that help you narrow down the data shown in the table. Filters can be performed on multiple columns and are specific to the type of data presented in the column. When a column has a filter applied, the column heading will be displayed in italic. To apply a filter, click on a column heading and use the Filters menu option to specify the filter. The type of filter available depends on the data displayed in the column.
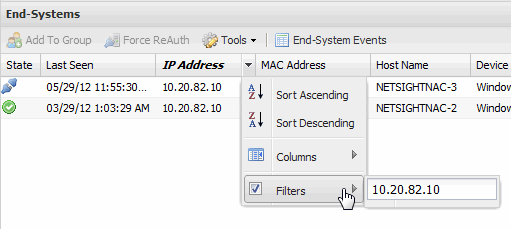
- Filter by String
- Allows you to filter by an exact match of a full or partial string in the column. For example, you can filter for a specific IP or MAC address, or for a specific device type.
-
Sample Filter by IP Address String
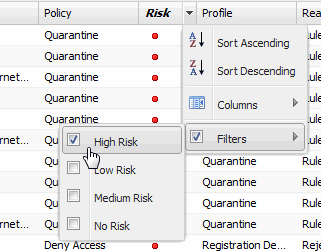
- Filter by List Choices
- Allows you to filter according to items selected on a list. For example, you can filter for a specific risk such as High Risk or a specific state such as Quarantine.
-
Sample Filter by Risk List
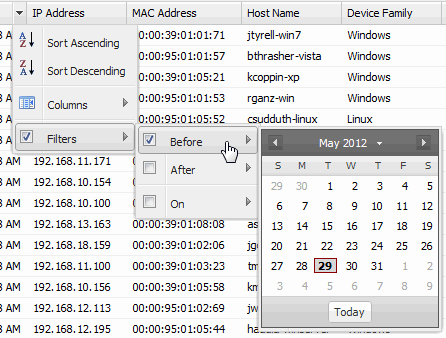
- Filter by Date
- Allows you to filter by a specific date or date range. For example, you can filter for end-systems last seen before or after a certain date.
-
Sample Filter by Last Seen by Date
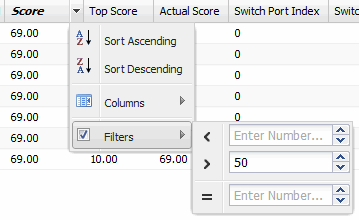
- Filter by Number
- Allows you to filter by a specific number or number range. For example, you can filter for end-systems whose assessment scores are greater than a certain number.
-
Sample Filter by Score Number
- Filter by Yes or No Value
- Allows you to filter for a Yes or No value. For example, you can filter for end-systems that are not Microsoft NAP (Network Access Protection) capable.
-
Sample Filter by a Yes or No Value
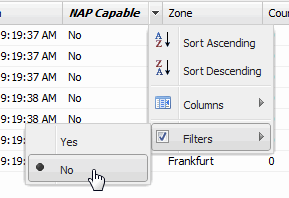
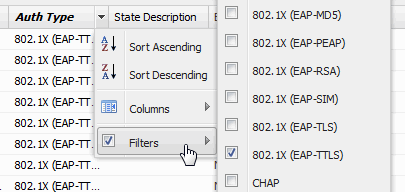
- Filter by Auth Type
- Allows you to filter by the authentication method used by end-systems to connect to the network.
-
Sample Filter by Auth Type
- Filter by Device Type
- Allows you to filter by the authentication method used by end-systems to connect to the network.
Buttons, Search Field, and Paging Toolbar

- Opens a window where you can add the selected end-system to a specific end-system or user group. After adding an end-system to a group, any rules that have been created that involved that group will now apply to the end-system as well. Changes to end-system group membership do not require an enforce and will be synchronized with appliances immediately. Changes will not affect the end-systems until the next authentication or assessment occurs.

- Forces the selected end-systems to re-authenticate. End-systems that are authenticated to a VPN device will be disconnected from the VPN.
-

- The Tools button provides access to a variety of options. See Tools Menu for more information.
-

- Launches a separate Events tab that displays up to 1,000 end-system events. Click the Search for Older Events button to search for older events in the end-system event cache.
-

- The Show Filters button becomes active when any filters are applied. It opens a window that shows all active filters.
- Devices/Authentication Drop-down Menus
- Allow you to filter the table by device type and authentication type.
-

- The Search function allows you to search for full or partial matches
on IP addresses, MAC addresses, user names, host names, switch IP, and
Custom/Registration/Group information.
Enter the full
or partial value you are searching for and click the Search button.
Matching items are displayed in the table. Press the Reset button to
clear the Search results and refresh the table.
Open Services Search
You can also perform a search for open services (ports) across all your end-systems. For example, you can use the open services search to:- Determine who is running an http server on their end-system.
- Determine who is running an FTP server on their end-system.
- Verify that no one is using a specific port before you deploy a software product.
To perform the search, enter the port number(s) you are searching for in the following format: "service=X,Y..." where X can be a port number or a well-known service name. For example, the following two searches are the same since "http" is well-known port 80 and "alternate" port 8080:service=http
service=80,8080
In addition, you can use a mix of service names and port numbers, for example:service=ftp,80
The search looks at data from the End-System Reachability test obtained from the last health result (scan). In your test sets, you must have the TCP Ping checkbox selected in the End-System Reachability test (this checkbox is not selected by default), and the port you are looking for must be listed in the list of ports. (Click the Modify button in the End-System Reachability Test field in your test sets to access the TCP Ping checkbox.) The End-System Reachability test is available in agent-less, Nessus, and Other test sets. It is not available for agent-based test sets.
-

- The End-Systems table is presented in pages. The paging toolbar provides four buttons that let you easily page through the table: first, previous, next, and last page. It also displays an indicator of the current and total number of pages. Enter a page number in the Page field and press Enter to quickly move to that page.
-

- Use the bookmark button to save the search, sort, and filtering options you have currently set. It opens a new window for the current report with a link that can be bookmarked in your browser. You can then use the bookmark whenever you want the same search, sort, and filtering options.
For information on related topics:

