How to Configure PEAP Authentication via OpenLDAP
This Help topic provides instructions for configuring NAC to authenticate PEAP, MsCHAP, and MsCHAPv2 requests by checking the username and password using an OpenLDAP server.
In NAC Manager, create an LDAP configuration that defines access to OpenLDAP.
- In the Advanced Configuration window, right-click on the LDAP Configurations folder and select Add LDAP Configuration. The Add LDAP Configuration Window opens.
- In the OU Object Classes field, use the configuration menu to select the Populate OpenLDAP Defaults option.
- Configure the LDAP configuration to do a password lookup. There are three ways to do this:
- Have the password encryption on the OpenLDAP server set to use clear text passwords. Then, in your LDAP configuration, set the User Authentication Type field to Plain Text Password Lookup and the User Password Attribute to userPassword (which is the default).
- Use an NT Hashed password. These encryption types are not supported by OpenLDAP for user passwords, so you must modify your user password update script or web page to set the password for the user, create the desired hash of the password, and set a newly defined attribute to have that value. With this method, the LDAP configuration must use the User Authentication Type of NTHash Password Lookup. You will also need to configure the User Password Attribute to be the attribute you selected for storing the NT Hash or LM Hash of the password.
- If your NAC deployment only requires authentication via captive portal Registration, then the User Authentication Type should be set to LDAP Bind for ease of deployment.
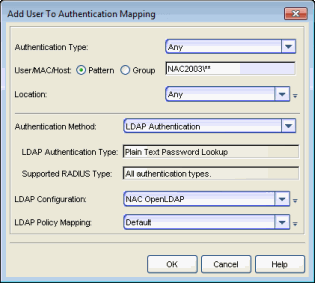
- In your Advanced AAA Configuration, add an entry that uses this LDAP configuration (see the example screen shot below). The configuration will allow NAC to verify the user's password from the PEAP/MsCHAP/MsCHAPv2 request.