The End-Systems tab presents end-system connection information for a single Extreme Access Control engine, all Access Control engines, or all the engines in an engine group, depending on what you select in the left-panel tree. You can also monitor end-system events and view the health results from an end-system's assessment.
To access this tab, select a single Access Control engine, the All NAC Appliances folder, or an engine group in the left-panel tree, then click the End-Systems tab in the right panel.
Use the table options and tools to find,
filter, sort, print, and export information in a table and customize table settings. You can access the Table
Tools through a right-mouse click on a column heading or anywhere in the table
body, or by clicking the Table Tools
 button in the
upper left corner of the table (if you have the row count column displayed). For more information, see
Table Tools.
button in the
upper left corner of the table (if you have the row count column displayed). For more information, see
Table Tools.
Click the graphic for more information.
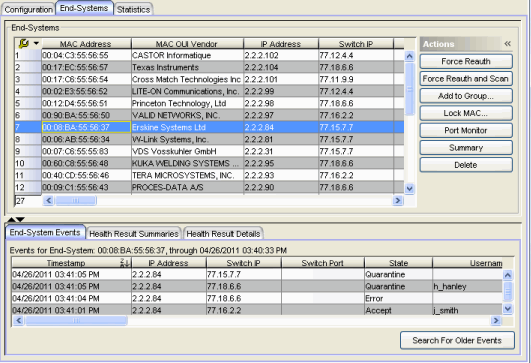
End-Systems
This table displays the last known connection state for each end-system attempting to connect.
- MAC Address
- The end-system's MAC address. MAC addresses can be displayed as a full MAC address or with a MAC OUI (Organizational Unique Identifier) prefix. You can specify how you want to display end-system MAC addresses in the Options window Display view (Tools > Options).
- Switch IP
- The IP address of the switch the end-system connected to. If the end-system is connected to an Access Control Controller engine, this is the Access Control Controller PEP (Policy Enforcement Point) IP address.
- Switch Port
- The port alias (if defined) followed by the switch port number the end-system connected to. If the
end-system is connected to a Layer 2 Access Control Controller engine, this is the Access Control Controller PEP (Policy Enforcement Point) port. However, for Layer 3 Access Control
Controller engines this column is blank.
If you add or update the port alias on the switch, you must enforce the Access Control engine in order for the new information to be displayed in the End-Systems table.
If you don't want the port alias displayed, remove the PORT_DESCRIPTION_FORMAT variable from the /opt/nac/server/config/config.properties file. If this variable is removed, only the switch port number displays.
- State
- The end-system's connection state:
- Scan — The end-system is currently being scanned.
- Accept — The end-system is granted access with either the Accept policy or the attributes returned from the RADIUS server.
- Quarantine — The end-system is quarantined because the assessment failed.
- Reject — The end-system was rejected because the assigned NAC profile was set to Reject, the MAC Locking test failed, or the RADIUS server was reachable but rejected the authentication request.
- Disconnected — All sessions for the end-system are disconnected. This state is only applicable for end-systems connected to switches that have RADIUS accounting enabled, or if the Session Deactivate Timeout option is enabled on the Reauthentication tab in Appliance Settings.
- Error — Indicates one of nine problems:
- the MAC to IP resolution failed, if assessment is enabled
- the MAC to IP resolution timed out, if assessment is enabled
- all RADIUS servers are unreachable
- the RADIUS request was non-compliant
- all assessment servers are unavailable
- the assessment server can't reach the end-system
- no assessment servers are configured
- the assessment server is not compatible with the current version of NAC Manager
- the username and password configured in the Assessment Server panel of the NAC Manager options (Tools > Options > Assessment Server) are incorrect for the assessment server
- Authentication Type
- Identifies the latest authentication method used by the end-system to connect to the network. (For Layer 3 Access Control Controller engines, this column lists "IP.") For a listing of all the authentication methods the end-system is using to authenticate, see the All Authentication Types column.
- Authorization
- The attributes returned by the RADIUS server for this end-system. If the end-system is connected to a switch that supports multi-authentication, then this column may not reflect the actual active policy for the authenticated user. For Layer 3 Access Control Controller engines, this column displays the policy assigned to the end-system for its authorization.
- Profile
- The name of the NAC profile that was assigned to the end-system when it connected to the network.
- Risk
- The overall risk level assigned to the end-system based on the health result of
the scan:
- Red — High Risk
- Orange — Medium Risk
- Yellow — Low Risk
- Green — No Risk
- Gray — Unknown
- Reason
- Provides additional information about the reasons why the end-system is in its particular connection state. It gives you an idea as to why a certain policy was applied to the end-system or why the end-system was rejected.
- Extended State
- Provides additional information about the end-system's connection state.
- Last Scan Result
- The last scan result assigned to the end-system: Scan, Accept, Quarantine, Reject, Error. This is the state that was assigned to the end-system as a result of the last completed scan. This typically matches the end-system State if scanning is currently enabled and was recently performed.
- Appliance Group
- This column only displays if you have multiple engine groups. It displays the engine group the Access Control engine was in when the end-system event was generated. For example, if the engine was in Appliance (Engine) Group A when an end-system connected, but then later the engine was moved to Appliance (Engine) Group B, this column still lists Appliance (Engine) Group A for that end-system's entry.
- Switch Location
- The physical location of the switch to which the end-system connected. If the end-system is connected to an Access Control Controller engine, this is the Access Control Controller PEP (Policy Enforcement Point) location.
- All Authentication Types
- This column displays all the authentication methods the end-system used to authenticate. The authentication types are listed in order of precedence from highest to lowest: Switch Quarantine, 802.1X, CHAP, PAP, Kerberos, MAC, CEP, RADIUS Snooping, Auto Tracking. View details about each authentication session (such as the NAC profile assigned to the end-system for each authentication type) in the End-System Events tab. You can also view authentication session information in the End-System Summary window.
- RFC3580 VLAN
- For end-systems connected to RFC 3580-enabled switches, this is the RFC3580 VLAN ID assigned to the end-system.
- Score
- The total sum of the scores for all the health details that were included as part of the quarantine decision.
- Actual Score
- The actual score is what the total score would be if all the health details including those marked Informational and Warning were included in the score.
- Custom 1
- Use this column to add additional information that you would like displayed. To add or edit custom information, right-click on the table entry and select Edit Custom Information. You can add information for up to four Custom columns. The columns for Custom 2, Custom 3, and Custom 4 are hidden by default. To display these columns, right-click in the table body and select Table Tools > Settings. In the Table Settings window, you can select to show these columns in the table. To clear the custom information, right-click on the table entry and select Clear Custom Information. You can change the text of the Custom column heading in the Options window Display view (Tools > Options).
Zone
Displays the end-system zone that the end-system is assigned to. For more information, see End-System Zones in the NAC Manager Concepts Help file.
Actions
| TIP: | These actions are also available from the right-click menu off an end-system entry in the table. |
|---|
- Force Reauth
- Forces the selected end-system to re-authenticate. End-systems authenticated to a VPN device are disconnected from the VPN.
- Force Reauth and Scan
- Forces the selected end-system to re-authenticate and undergo an assessment (scan). (End-systems authenticated to a VPN device are disconnected from the VPN.) The assessment only takes place if scanning is enabled in the NAC profile assigned to the end-system.
- Send Agent Message
- Opens the Send Message to End System Agents window, from which you can send a message to one or more systems running an assessment agent.
- Add to Group
- Lets you add the selected end-system to a specific end-system or user group. If the end-system is a registered device, it can be added to a registration group. After adding an end-system to a group, any rules created that involved that group apply to the end-system as well. Changes to end-system group membership do not require an enforce and are synchronized with engines immediately. Changes do not affect the end-system until the next authentication or assessment occurs.
- Lock MAC
- Opens the Add MAC Lock window where you can lock the MAC address of the selected end-system to a switch or switch and port.
- Port Monitor
- Opens the Port Monitor window where you can view detailed status information and statistics for the selected port.
- Summary
- Opens the End-System Summary window where you can view summary information for the end-system selected in the table.
- Delete
- Deletes the selected end-system entries from the table and also deletes the associated end-system events. You are given the option to delete any custom
information, group assignment, MAC locks, and registration and web
authentication associated with the end-systems.
The Force Delete of End-System option completely deletes the end-system from NAC Manager, regardless of whether the end-system reauthentication is successful when the delete is executed. The option is deselected by default. When deselected, it prevents possible synchronization conditions where the authentication session remains active on the switch even though the end-system is deleted from NAC Manager. These conditions can occur when there are underlying issues that prevent the end-system reauthentication from completing properly.
| NOTES: | The Delete operation does not remove an end-system from the Blacklist group. Blacklist is a special group that requires end-systems to be manually removed using the Edit End-System Group window. Deleting an end-system from the table also deletes the user's current authentication. If the user is connected to the network at the time of the delete, they are forced to re-authenticate. |
End-System Events Tab
This tab displays historical connection information for the end-system selected in the table above. End-system events are stored daily in the database. In addition, the end-system event cache stores in memory the most recent end-system events and displays them here in this tab. This cache allows NAC Manager to quickly retrieve and display end-system events without having to search through the database. You can configure parameters for the event cache (such as the number of events to display) using the End-System Event Cache options in the NAC Manager Options view (Tools > Options).
| NOTE: | The End-System Events tab displays events up to the most recent delete event for the end-system, if one exists. If you want to see events that happened prior to the most recent delete event, use the Search for Older Events button. |
Click the graphic for more information.
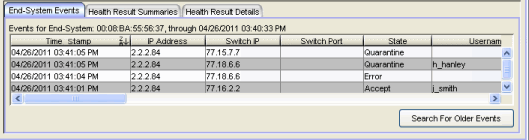
- Switch IP
- The IP address of the switch the end-system connected to. If the end-system is connected to an Access Control Controller engine, this is the Access Control Controller PEP (Policy Enforcement Point) IP address.
- Switch Port
- The switch port number to which the end-system is connected. If the end-system is connected to a Layer 2 Access Control Controller engine, this is the Access Control Controller PEP (Policy Enforcement Point) port. However, for Layer 3 Access Control Controller engines this column is blank.
- State
- The end-system's connection state:
- Scan — The end-system was scanned.
- Accept — The end-system was granted access with either the Accept policy or the attributes returned from the RADIUS server.
- Quarantine —The end-system was quarantined because the assessment failed.
- Reject — The end-system was rejected because the assigned NAC profile was set to Reject, the MAC Locking test failed, or the RADIUS server was reachable but rejected the authentication request.
- Disconnected — This end-system session was disconnected, however other sessions for the end-system may still be active. For example, the end-system may have a disconnected session with an authentication type of 802.1X, but still have an active MAC authentication session. This state is only applicable for end-systems connected to switches that have RADIUS accounting enabled, or if the Session Deactivate Timeout option is enabled on the Reauthentication tab in Appliance Settings.
- Error — Indicates one of nine problems:
- the MAC to IP resolution failed
- the MAC to IP resolution timed out
- all RADIUS servers are unreachable
- the RADIUS request was non-compliant
- all assessment servers are unavailable
- the assessment server can't reach the end-system
- no assessment servers are configured
- the assessment server is not compatible with the current version of NAC Manager
- the username and password configured in the Assessment Server panel of the NAC Manager options (Tools > Options > Assessment Server) are incorrect for the assessment server
- Authentication Type
- Identifies the authentication method used by the end-system to connect to the network. For Layer 3 Access Control Controller engines, this column lists "IP."
- Authorization
- The attributes returned by the RADIUS server. If the end-system is connected to a switch that supports multi-authentication, then this column may not reflect the actual active policy for the authenticated user. For Layer 3 Access Control Controller engines, this column displays the policy assigned to the end-system for its authorization.
- Reason
- Provides additional information about the reasons why the end-system is in its particular connection state. It gives you an idea as to why a certain policy was applied to the end-system or why the end-system was rejected.
- Extended State
- Provides additional information about the end-system's connection state.
- State Description
- This column provides more details about the end-system state. For example, if the end-system's connection state is Reject, this column might list the RADIUS server (primary or secondary) that rejected the authentication request.
- Switch Location
- The physical location of the switch to which the end-system is connected. If the end-system is connected to an Access Control Controller engine, this is the Access Control Controller PEP (Policy Enforcement Point) location.
- Appliance Group
- This column is only displayed if you have multiple engine groups. It displays what engine group the Access Control engine was in when the end-system event was generated. For example, if the engine was in Appliance (Engine) Group A when an end-system connected, but then later the engine was moved to Appliance (Engine) Group B, this column would still list Appliance (Engine) Group A for that end-system's entry.
Zone
Displays the end-system zone that the end-system is assigned to. For more information, see End-System Zones in the NAC Manager Concepts Help file.
- Search for Older Events
- This button lets you search for older events stored in the database
outside of the end-system events cache. The maximum search parameters
for this extended search are configured in the
End-System Event Cache options
in the NAC Manager Options view (Tools > Options). The search is ended when any one of the parameters is
reached.
- Maximum number of results to return from search
- Maximum time to spend searching for events (in seconds)
- Maximum number of days to go back when searching
Health Result Summaries Tab
This tab provides summary information on health results (assessment results) obtained for the end-system selected in the table above. You can specify the number of health result summaries displayed using the Health Result Persistence options in the Data Persistence Option view.
Click the graphic for more information.
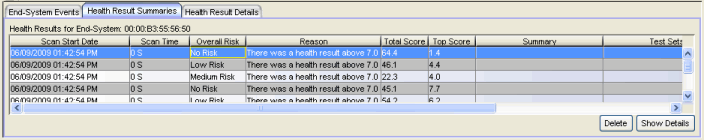
- Overall Risk
- The overall risk level assigned to the end-system based on the health result of the scan: High Risk, Medium Risk, Low Risk, or No Risk.
- Reason
- The reason the health result was placed into the specified risk level. This is based on the risk level configuration that was used for the assessment, for example, if there was one or more health result detail with a score greater than 7. If the end-system is NAP capable, then this is based on the values returned from NAP.
- Total Score
- The total sum of the scores for all the health details that were included as part of the quarantine decision, followed by the actual score in parenthesis. The actual score is what the total score would be if all the health details were included as part of the quarantine decision. It includes all scores, including those marked Informational and Warning. If the total score and the actual score are the same, only one score is shown.
- Top Score
- The highest score received for a health detail that was included as part of the quarantine decision. Scores that are marked as Informational or Warning are not considered.
- Summary
- A list of all the test cases that were run against the device during assessment. The test case name is listed, or if that is not available, the test case ID is listed.
- Test Sets
- The list of test sets that were run during assessment, for example, Default Nessus, Default Agent-less, and Default Agent-based. Test sets are defined as part of the assessment configuration. If the end-system is NAP capable, then this column displays Microsoft NAP indicating that NAP performed the assessment.
- Total Details
- The total number of health result details (vulnerabilities) detected during the assessment.
- Show Details Button
- Opens the Health Results Details tab where you can view detailed information on the security risks found on the end-system during this particular assessment.
Health Result Details Tab
This tab lets you view health result details (assessment result details) for the end-system selected in the table above. The drop-down list at the top of the tab displays all the end-system's scan results listed by start date. Select the date for the particular scan result you wish to view. The tab presents detailed information on the security risks found on the end-system during that particular assessment (scan). You can specify the number of health result details displayed using the Health Result Persistence options in the Data Persistence Option view.
| TIP: | Double-click on an individual entry in the table to view a description, result, and solution for the health result displayed in a separate window. |
Click the graphic for more information.
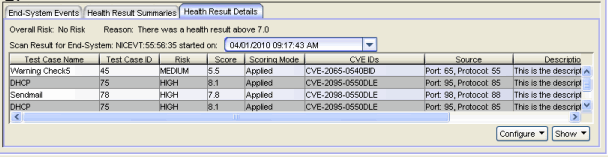
- Risk
- The risk level assigned to the problem found on the port:
- High (corresponds to a Hole)
- Medium (corresponds to a Warning)
- Low (corresponds to a Note)
- Score
- The score assigned to the test case. The score is a value between 0.0 and 10.0. In the case of agent-based test cases, the score is either 0.0 for a passed test, or 10.0 for a failed test, unless specifically overwritten by the scoring override configuration.
- Scoring Mode
- The scoring mode that was used at the time the test was performed.
- Applied — The score returned by this test was included as part of the quarantine decision.
- Informational — The score returned by this test was reported, but did not apply toward a quarantine decision.
- Warning — The score returned by this test was only used to provide end user assessment warnings via the Notification portal web page.
- CVE IDs
- The CVE (Common Vulnerability and Exposures) ID assigned to the security vulnerability or exposure. For more information on CVE IDs, refer to the following URL: http://www.cve.mitre.org/.
- Source
- The port on the end-system that the security risk was detected on followed by the well-known number (ID) assigned to the IP Protocol Type.
- Description
- This column lists information about the health result detail. Double-click on the entry in the table to open a Health Result Detail Description that displays a description, result, and solution for the health result. In addition, the Description window includes operating system information such as version and product type (when available). With this information, you have the flexibility to add scoring overrides for OS specific issues for any given Test Case, using the Regular expression functionality of the scoring override. (For more information, see the Add/Edit Scoring Override Configuration window.)
- Remediation
- For agent-based assessment, this column lists the results of remediation attempts: Success, Failed, or Not Attempted.
- Type
- A "type" is assigned to each security risk found on a port
during an assessment, and is used to determine whether to Quarantine an end-system.
Types are configurable on the assessment agent.
There are three types:
- Hole — The port is vulnerable to attack.
- Warning — The port may be vulnerable to attack.
- Note — There may be a security risk on the port.
- Configure Button
- Use the Configure drop-down list to:
- Add Scoring Override — Create a scoring override for the selected test case.
- Manage Scoring Override Configurations — Open the Manage Scoring Override Configurations window where you can view and define the scoring override configurations used in your assessment configurations.
- Edit Agent-based Test Case — Open the Test Editor window for the selected agent-based test case.
- Manage Risk Level Configurations — Open the Manage Risk Level Configurations window where you can view and define the risk level configurations used in your assessment configurations.
TIP: The Configure and Show button menu options can also be accessed by right-clicking on a health result detail in the table.
- Show Button
- Use the Show drop-down list to:
- Show All End-Systems With Test Case ID — Open the End Systems tab as a separate window listing only those
end-systems with the selected test case ID in their latest scan.
NOTE: If you select a vulnerability that does not list a CVE-ID (the column is empty), clicking this button launches a window that lists all end-systems that have any vulnerability without a CVE-ID. - Show Description — Open a Health Result Detail Description window that displays information about the vulnerability. This window can also be displayed by double-clicking on any entry in the Health Result Details table.
- Show All End-Systems With Test Case ID — Open the End Systems tab as a separate window listing only those
end-systems with the selected test case ID in their latest scan.
For information on related windows: