The Alarms and Events tab displays alarm and event details for all managed devices in the network, with sorting and filtering of relevant information for network troubleshooting and forensics. Additionally, the menu at the top of the screen provides links to additional information about your version of Extreme Management Center (formerly NetSight).
This Help topic provides information on the following topics:
Access Requirements
To view the information in the Alarms and Event logs, you must be a member of an authorization group assigned the appropriate Management Center capabilities:
- NetSight OneView > Access OneView
- NetSight OneView > Events and Alarms > OneView Event Log Access
- NetSight OneView > Events and Alarms > OneView Alarms Read Access or Read/Write Access
For additional information, see How to Configure User Access to Extreme Management Center Applications and Extreme Management Center Access Requirements.
Alarms
Use the Alarms and Events tab to access an Alarms tab that displays the current alarms for the network.
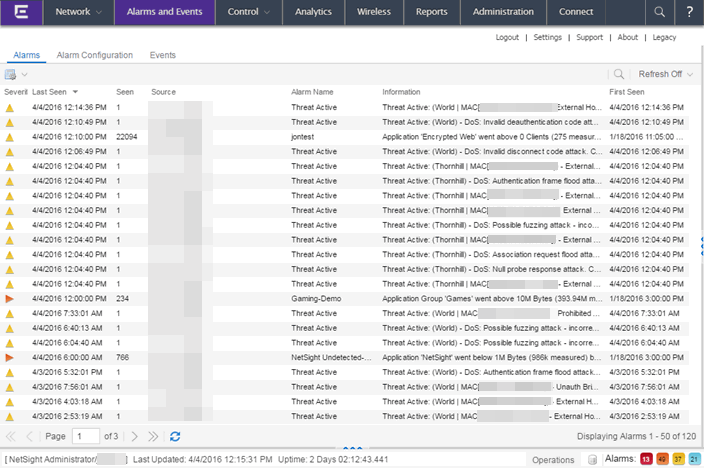
In the Alarms tab:
- Right-click on the Source or Alarm Name column or click the Gear icon (
 ) and select Alarm History > By Source to view an Alarm History for that device. If the Source includes a subcomponent (such as an interface on the device), then the alarm history is specific to that subcomponent.
) and select Alarm History > By Source to view an Alarm History for that device. If the Source includes a subcomponent (such as an interface on the device), then the alarm history is specific to that subcomponent. - Right-click on the Source or Alarm Name column or click the Gear icon (
 ) and select Alarm History > By Alarm Name to view an Alarm History for a specific alarm.
) and select Alarm History > By Alarm Name to view an Alarm History for a specific alarm. -
Right-click on the Source or Alarm Name column or click the Gear icon (
 ) and select Alarm History > All to view the Alarm History for all devices.
) and select Alarm History > All to view the Alarm History for all devices.
- Right-click on an alarm to clear the selected alarm or to clear all alarms. Supply a reason the alarm cleared, if necessary. which is recorded in the Alarm History.
- Right-click on an alarm or select an alarm and click the Gear icon (
 ) and select Edit Alarm Definition to open the alarm in the Alarm Configuration window, from which you can edit the criteria which triggers the alarm.
) and select Edit Alarm Definition to open the alarm in the Alarm Configuration window, from which you can edit the criteria which triggers the alarm. - Double-click on any row in the table to open a window that displays Alarm Details.
Extreme Management Center
Every Management Center page includes a system-wide Alarm Summary in the lower right corner. This indicates the number of current alarms for each severity (Critical, Error, Warning, and Info) present in the entire system. If there are no current alarms, the status displays all zeroes. Click on an indicator to open the Alarms tab filtered to display the alarms of that severity.

Alarm Configuration
The Alarm Configuration tab in the Alarms and Events tab allows you to configure the network alarms that provide status information for a particular problem or condition on a particular network component. Alarms are triggered when event conditions (called a trigger event) occur on your network, and they are tracked until the problem or condition is removed. From the Alarm Configuration tab you can also create an alarm definition that detects when the problem or condition is removed and clears the alarm. For example, a Link Down alarm is triggered when a device emits a linkDown trap. Then, when the device emits a linkUp trap, the Link Up alarm automatically clears the Link Down alarm.
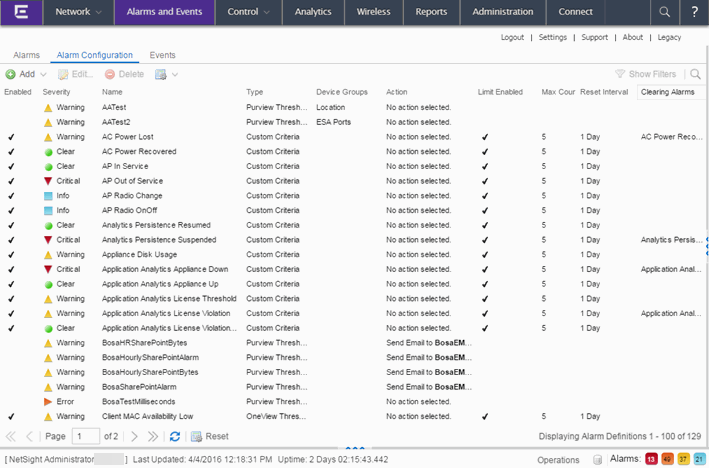
Via the Add menu, you can:
- Add a new alarm definition, which includes configuring the conditions (criteria) that trigger the alarm, and defining the actions that occur automatically to notify a person or network component about the problem, when the alarm triggers.
- Edit and delete alarm definitions as well as configure email settings for alerts.
Management Center ships with a set of default alarm definitions, which you can use as is, or delete or modify them as desired.
For additional information, see How to Configure Alarms in Extreme Management Center.
Alarm Configuration Column Definitions
Enabled — A checkmark in the Enabled column indicates the alarm definition is active. Disable an alarm definition to deactivate it without deleting the definition.
Severity — This column indicates the seriousness of an alarm definition, which posses its own specified severity regardless of the severity of the event or trap that triggered it.
-
 (question mark) Set from Source — the alarm definition uses the severity level of the trigger event, for example a warning event.
(question mark) Set from Source — the alarm definition uses the severity level of the trigger event, for example a warning event. -
 (Red) Critical — A problem with significant implications.
(Red) Critical — A problem with significant implications. -
 (Orange) Error — A problem with limited implications.
(Orange) Error — A problem with limited implications. -
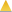 (Yellow) Warning — A condition that might lead to a problem.
(Yellow) Warning — A condition that might lead to a problem. -
 (Blue) Info — Information only; not a problem.
(Blue) Info — Information only; not a problem. -
 (Green) Clear — An alarm that clears another alarm (for example, LinkUp).
(Green) Clear — An alarm that clears another alarm (for example, LinkUp).
Name — The name of the alarm definition.
Type — Identifies the type of alarm definition for this row (threshold, trap, or custom criteria).
Device Groups — If desired, you can restrict the alarm definition to devices and port elements in one or more device groups. This column indicates the device group to which the alarm definition is assigned. The alarm definition is only raised on the devices and interfaces in the selected device groups. This allows you to filter alarms to specific devices or important ports.
Action — The actions that occur when an alert is triggered, if any.
Limit Enabled — A checkbox indicates that there is a rate-limit on the alarm's actions.
Max Count — If Limit Enabled is checked, this column indicates the number of times an action is performed for this alarm. Once the limit is reached, the alarm is still recorded, but no further actions are performed until the Reset Interval expires. If you configure multiple action types, the limit is for the number of times the set of configured actions is performed, not for each individual action. If Limit Enabled is not checked, there is no limit placed on the number of times the action is performed.
Reset Interval — If Limit Enabled is checked, this column displays the length of time from when the first action is triggered until the count is reset. Once the count is reset, actions are executed until the Max Count is reached again. If the reset interval is set to "None", then once the alarm limit is reached, the alarm does not reset unless manually reset. You can reset the action counters for all current alarms related to this alarm definition using the Reset All button. For example, if there is a Flow Limit Alarm on three devices, it resets the limits on those three alarms.
Clearing Alarms — This column displays the Name of the alarm that acts to clear the current alarm.
Events
Open the Events tab in the Alarms and Events tab to access the event log, as well as the event logs for Management Center, legacy applications, and Extreme Access Control Audit events and Wireless Audit events. In addition, you can access an event log for Management Center Scheduler events.
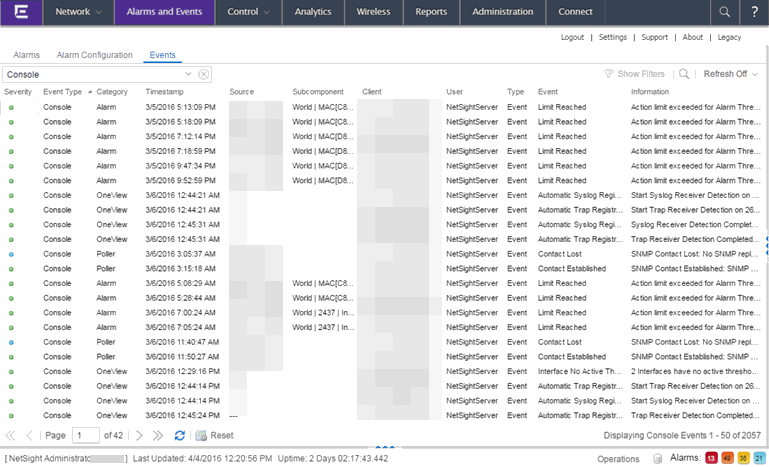
Use the drop-down menu at the top of the table to filter events based on application.
The Management Center event logs for Management Center and legacy components (Console, Automated Security, Inventory, Policy Control Console, Policy, NAC Manager, and Wireless) present the same data as the event logs in the actual applications.
The Access Control Audit event log provides information on Access Control Registration events such as when a device or user is added during the registration process, or an end-system is added/removed/updated via the registration administration web page.
The Access Control Engine event log displays engine events.
| NOTE: | Installed certificates using an MD5 RSA signature algorithm now generate an event in Management Center version 7. |
|---|
The Wireless Audit event log allows you to view the configuration activity on Wireless Manager.
The Application Analytics event log displays Application Analytics engine events as well and Application Analytics configuration activity.
The Scheduler event log displays events for the scheduled tasks configured via the Administration tab. The event log includes task execution events and errors.
The Admin event log displays Management Center server and database administrative events, and Management Center user authentication and connection events. (In the legacy Console application, these events are included in the Console event log.)
You can manipulate the table data in several ways to customize the view for your own needs:
- Click the drop-down arrow to open the drop-down menu and select an application to include in the Events table.
- Click on the column headings to sort column data in ascending or descending order.
- Hide or display different columns by clicking on a column heading drop-down arrow and selecting the column options from the menu.
- Double-click on any row in the table to open a window that displays Event Details.
Event Log Column Definitions
Following are definitions of the Event Log table columns:
Severity — Indicates the potential impact of the event or trap. Hold the
mouse pointer over a Severity icon to display a tool tip that
provides the severity: Alert, Critical, Debug, Emergency, Error,
Info, Notice, Warning. For traps, this column shows the Severity as
defined in the trapd.conf file.
Event Type — Displays the application to which the event or trap is associated.
Category — Shows the category defined in the trapd.conf
file for traps. For other events, it indicates the source of the information, either a Console Poller, local log,
syslog, trap log, Error (java exceptions), etc.
Timestamp — Shows the date and time when an event or trap occurred.
Source — Shows the IP address of the host that was the source of the event or trap. If you want to display the source as a hostname (if available) you can set that option in the Suite-wide Alarm/Event Logs and Tables options.
Subcomponent — If the event or trap can identify a specific subcomponent of a device (or other source) which pinpoints the location of the problem, it is displayed here. One example of a subcomponent is an interface on a device.
Client — Displays the hostname of the source of the event.
User — The user that performed the action that triggered the event.
Type — Identifies the type of information for this row (event or trap).
Event — Shows the type of event or trap. For traps, this column shows the name of the event as
defined in the trapd.conf file.
Information — Shows an summary explanation of the event or trap.
Buttons, Search Field, and Paging Toolbar
 — The Show Filters button becomes active when any filters are applied. It opens a window
that shows all active filters.
— The Show Filters button becomes active when any filters are applied. It opens a window
that shows all active filters.
 — The Search function allows you to search for full or partial matches
on all fields. Enter the full
or partial value you are searching for and click the Search button.
Matching items are displayed in the table. Click the Reset button to
clear the Search results and refresh the table.
— The Search function allows you to search for full or partial matches
on all fields. Enter the full
or partial value you are searching for and click the Search button.
Matching items are displayed in the table. Click the Reset button to
clear the Search results and refresh the table.
 — The paging
toolbar provides four buttons that let you easily page through the table: first, previous, next, and last page. It also displays an indicator of the current and total number of pages.
Enter a page number in the Page field and press Enter to quickly move to
that page.
— The paging
toolbar provides four buttons that let you easily page through the table: first, previous, next, and last page. It also displays an indicator of the current and total number of pages.
Enter a page number in the Page field and press Enter to quickly move to
that page.
 — Clears the search field and search results, clears all filters, and refreshes the table.
— Clears the search field and search results, clears all filters, and refreshes the table.
For information on related topics:
 — Refreshes the page.
— Refreshes the page.