The Alarm Configuration view lets you configure network alarms that provide status information for a particular problem or condition on a particular network device. Alarms are triggered when certain trap or event conditions (called a trigger event) occur on your network, and they are tracked until the problem or condition is removed.
The alarm source, which is the device, interface, or AP that is the source of the trigger event, is considered to have an alarm until the alarm is cleared. You can view alarms and alarm status and clear alarms in the Alarms view in Extreme Management Center (Alarms and Events > Alarms).
Using the Alarm Configuration view, you can add a new alarm definition, which includes configuring the conditions (criteria) that triggers the alarm, and defining the actions performed to notify a person or network component about the problem, when the alarm is triggered.
You can create an alarm definition that detects a problem or condition and raises an alarm, and create an alarm definition that detects when the problem or condition is removed and clears the alarm. For example, a Device Down alarm is triggered when contact with a device is lost. Then, when contact is established with the device, the Device Up alarm automatically clears the Device Down alarm.
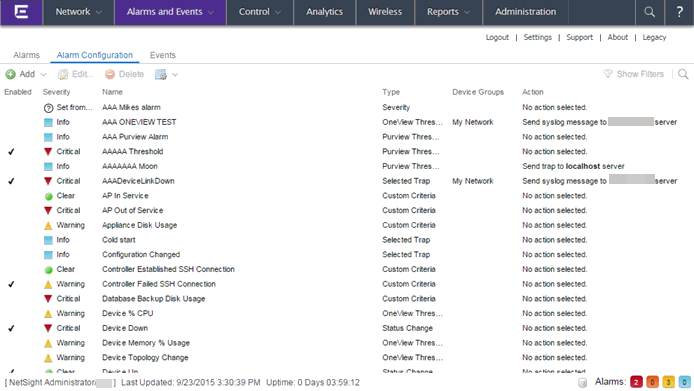
Management Center ships with a set of default alarm definitions, which you can see listed in the Alarms view. You can use these default alarms as is, or enable, disable, delete or modify them, as desired.
This Help topic includes instructions for:
- Defining an Alarm
- Disabling Alarms
- Deleting Alarms
- Configuring Email Settings
- Resetting Action Limits
- Enabling/Disabling All
- Restoring Default Alarms
- Viewing Alarms
- Clearing Alarms
Defining an Alarm
You can use the Alarm Configuration view to create new alarm definitions and define their criteria and actions, and to edit the criteria and actions for existing alarms.
There are six types of alarms, each using different criteria to establish the alarm definition.
- Selected Trap Alarm — Triggers an alarm when a specific trap occurs. You are able to select from all the Trap IDs available for the devices modeled in the Management Center database.
- Severity Alarm — Triggers an alarm when an event or trap occurs to which you assign a specific level of severity. Select an event severity level (Emergency, Alert, Critical, Error, Warning, Notice, or Info) and whether the alarm is triggered by traps, or events, or both.
- Status Change Alarm — Triggers an alarm when the operational status for a device changes: Contact Lost triggers the alarm when contact with a device is lost, Contact Established triggers the alarm when contact is restored, and Both triggers the alarm when contact is lost and when contact is restored.
- Flow Alarm — Flow alarms are used for reporting network traffic flow anomalies detected by the NetFlow flow collector. An alarm triggers when a flow matches criteria you configure.
- Custom Criteria Alarm — Triggers an alarm when very specific criteria you define is met.
- Threshold Alarm — Triggers the alarm when a specified value enters a defined range. For example, when CPU utilization exceeds 80% or when free disk space falls below 100 MB. There are two threshold alarm types: OneView and Application Analytics. This option is disabled if your Management Center license does not include Management Center features that support threshold alarms (such as device statistics collection) and you do not have an Application Analytics license.
To create a new alarm definition:
- Click the Add button and select the type of Alarm you are creating from the drop-down menu. The
Alarm Configuration window opens.
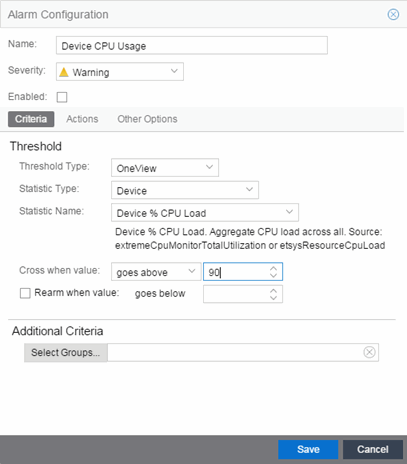
- Enter a name for your new alarm definition in the Name field.
- Select the appropriate severity level of the alarm definition in the Severity drop-down menu. The alarm can have its own specified severity regardless of the severity of the event or trap from which it is triggered.
-
 (question mark) Set from Source — the alarm uses the severity level of the trigger event, for example a warning event.
(question mark) Set from Source — the alarm uses the severity level of the trigger event, for example a warning event. -
 (Red) Critical — A problem with significant implications.
(Red) Critical — A problem with significant implications. -
 (Orange) Error — A problem with limited implications.
(Orange) Error — A problem with limited implications. -
 (Yellow) Warning — A condition that might lead to a problem.
(Yellow) Warning — A condition that might lead to a problem. -
 (Blue) Info — Information only; not a problem.
(Blue) Info — Information only; not a problem. -
 (Green) Clear — An alarm that clears another alarm (for example, Device Up).
(Green) Clear — An alarm that clears another alarm (for example, Device Up). - Select the Enabled checkbox to activate the alarm definition. You can disable an alarm definition to deactivate it without deleting the definition.
- Enter the criteria that triggers the alarm. Options in the Criteria tab vary depending on the type of alarm you are creating.
- Selected Trap Alarm
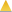
- Click the Select Traps button. The Select Traps window opens.
- Select the traps that trigger the alarm.
- Click Save.
- Click Select Groups if the alarm only applies to a specific group of devices. Select the groups of devices in the Alarm Group Selection window and click OK. Not selecting any device groups means the alarm applies to all devices.
- Click the Actions tab to configure the actions performed when the alarm is triggered. Proceed to Step 6 for information about configuring rule actions.
- Severity Alarm
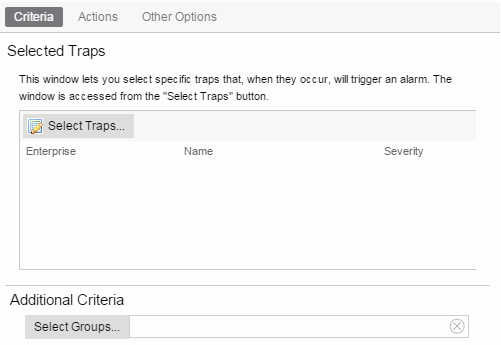
- Select the severity of the event or trap required to generate the alarm from the drop-down menu (Emergency, Alert, Critical, Error, Warning, Notice, or Info). Traps or Events that occur and match the severity in this drop-down menu trigger the alarm. For example, you can create a severity alarm with a Severity of Error that is triggered when a trap or event occurs with an Event/Alarm Severity of Alert.
- Select whether the alarm is triggered by traps, or events, or both.
- Click Select Groups if the alarm only applies to a specific group of devices. Select the groups of devices in the Alarm Group Selection window and click OK. Not selecting any device groups means the alarm applies to all devices.
- Click the Actions tab to configure the actions performed when the alarm is triggered. Proceed to Step 6 for information about configuring rule actions.
- Status Change Alarm
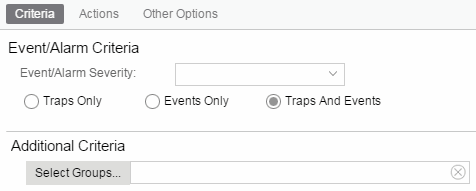
- Select whether the alarm triggers when contact with a device is lost (Contact Lost), restored (Contact Established), or when contact is lost and when contact is regained (Both).
- Click Select Groups if the alarm only applies to a specific group of devices. Select the groups of devices in the Alarm Group Selection window and click OK. Not selecting any device groups means the alarm applies to all devices.
- Click the Actions tab to configure the actions performed when the alarm is triggered. Proceed to Step 6 for information about configuring rule actions.
- Flow Alarm
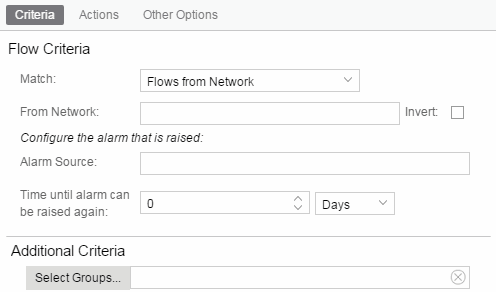
- Select how the flow is matched to trigger a flow alarm. Flow alarms are used for reporting network traffic flow anomalies detected by the NetFlow flow collector. NetFlow is a flow-based data collection protocol that provides information about the packet flows being sent over a network. K-Series, S-Series, and N-Series devices support NetFlow flow collection.
- Flows from Network — Match a flow's source IP address to the specified network.
- Flows to Network — Match a flow's destination IP address to the specified network.
- Flows from Network from Port — Match a flow's source IP address and port number to the specified network and port.
- Flows from Port to Network — Match a flow's source port number and destination IP address to the specified port and network.
- Flows from Network with low TTL — Match a flow's source IP address and TTL value to the specified network and the TTL at or below value.
- Enter the Network or Port monitored by the flow alarm
- From/To Network — A network is identified as a set of IP masks. The mask is used as a filter to define a range of IP addresses. Masks can be entered in CIDR or dotted-decimal format.
- CIDR — CIDR format uses a slash followed by a number
between 8 and 32, to define the number of contiguous, left-most "one" bits
that define the network mask. For example, /16 indicates a 16-bit mask. Here is an example of a From/To Network value using the CIDR format:
10.20.0.0/16,10.20.0.0/24 - Dotted-Decimal — Dotted decimal format represents network masks as
four octets separated by periods. For example, a 16-bit mask in dotted decimal
notation is 255.255.0.0. Here is an example of a From/To Network value using the dotted-decimal format:
10.20.0.0/255.255.0.0,10.20.88.0/255.255.255.0 - For example, if you entered either 10.20.0.0/16 (CIDR) or 10.20.0.0/255.255.0.0 (Dotted-Decimal) in the From/To Network field, then all incoming packets in the range 10.20.00.00 through 10.20.255.255 would result in an address match.
- CIDR — CIDR format uses a slash followed by a number
between 8 and 32, to define the number of contiguous, left-most "one" bits
that define the network mask. For example, /16 indicates a 16-bit mask. Here is an example of a From/To Network value using the CIDR format:
- From Port — Enter the port number to be matched.
- TTL at or below — Enter a value that triggers an alarm when the TTL value in the packet's TTL field is equal to or less than the value entered.
- Select the Invert checkbox if you want the flow criteria to trigger the alarm when it does not match the specified values.
- From/To Network — A network is identified as a set of IP masks. The mask is used as a filter to define a range of IP addresses. Masks can be entered in CIDR or dotted-decimal format.
- Enter a phrase in the Alarm Source field used as the source of the alarm.
- Enter the amount of time, in minutes, hours, or days that must pass until the alarm can trigger again in the Time until alarm can be raised again field. This prevents a large number of alarms being triggered, if many flows match the alarm criteria. If you select Never, the alarm only triggers one time. Once you manually clear the alarm, it can be triggered again.
- Click Select Groups if the alarm only applies to a specific group of devices. Select the groups of devices in the Alarm Group Selection window and click OK. Not selecting any device groups means the alarm applies to all devices.
- Click the Actions tab to configure the actions performed when the alarm is triggered. Proceed to Step 6 for information about configuring rule actions.
- Custom Criteria Alarm
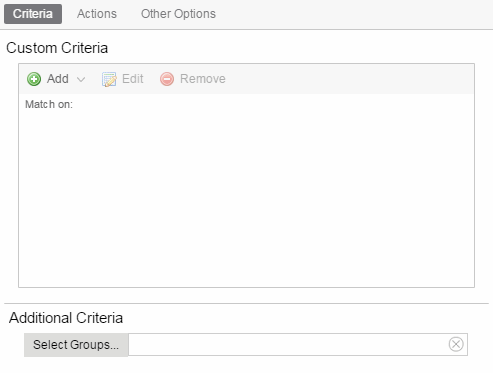
- Click the Add drop-down menu and select the criteria by which the alarm triggers.
- Severity Criteria — Select one or more severity levels against which to match.
- Match Selected — The reported Severity is matched against any of the Severity levels selected in the list.
- Exclude Selected — The reported Severity matches if it is not one of the Severity levels selected in the list.
- Category Criteria — Select one or more event categories to match against the Category column of the event. An event category is a way to group related events. For example, all events related to device discovery would be in the "Discover" category
- Match Selected — The reported Category is matched against any of the categories selected in the list.
- Exclude Selected — The reported Category matches if it is not one of the categories selected in the list.
- Type Criteria — Select one or more message types (Event, Inform, Trap) to match against the Type column of the event.
- Match Selected — The reported Type is matched against any of the types selected in the list.
- Exclude Selected — The reported Type matches if it is not one of the message types selected in the list.
- Event Criteria — Select one or more event types to match against the Event column of the event.
- Match Selected — The reported Event is matched against any of the event types selected in the list.
- Exclude Selected — The reported Event matches if it is not one of the event types selected in the list.
- Host or IP Criteria — Select one or more host names or IP/Subnet addresses to match against the value of the address appearing in the Source column of the event. The list of host names and IP/ Subnet addresses can be edited by clicking the Edit List button.
- Match Selected — The reported host name or IP/Subnet address is matched against any of the host or IP/Subnets selected in the list.
- Exclude Selected — The reported host name or IP/Subnet address matches if it is not one of the host or IP/Subnets selected in the list.
- Log Criteria — Select one or more Event Logs against which to match.
- Match Selected — The log where the event was received is matched against any of the logs selected in the list.
- Exclude Selected — The log where the event was received matches if it is not one of the logs selected in the list.
- Phrase Criteria — Select one or more text strings (phrases) to match against text in the Information column of the event or trap. The list of text phrases can be edited by clicking the Edit List button.
- Match Selected — The information text string is matched against one or more phrase selected from the list.
- Exclude Selected — The information text string matches if it is not one of the phrases selected from the list.
- Severity Criteria — Select one or more severity levels against which to match.
- Click Select Groups if the alarm only applies to a specific group of devices. Select the groups of devices in the Alarm Group Selection window and click OK. Not selecting any device groups means the alarm applies to all devices.
- Click the Actions tab to configure the actions performed when the alarm is triggered. Proceed to Step 6 for information about configuring rule actions.
- Click the Add drop-down menu and select the criteria by which the alarm triggers.
- Threshold Alarm
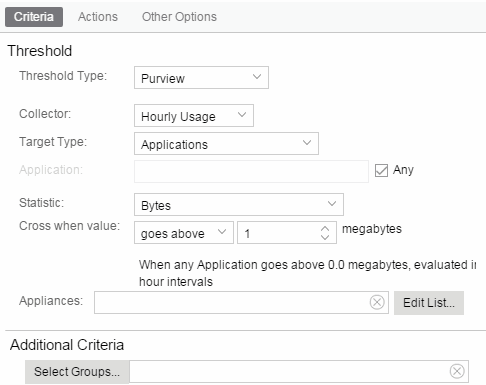
- Select a Threshold Type.
- OneView — The Management Center (formerly OneView) Collector gathers historical reporting data over time, which is then used in Management Center reports. Threshold alarms are raised when the reporting data matches a threshold alarm criteria.
- Application Analytics — The Application Analytics engine generates Application Analytics threshold alarms as part of the application usage collection process. Threshold alarms are raised when hourly or high-rate usage data matches a threshold alarm criteria. Each target record produced on the Application Analytics engine is evaluated at the end of each collection interval to see if it matches alarm criteria. If a statistic has crossed a configured threshold, an alarm in raised. Alarms can track single target types as well as target combinations. They can reference specific targets, for example a specific application such as Facebook, or they can reference all the targets in a target type, for example all applications. Only the target types and target combinations that are collected by Application Analytics can be used in alarms.
- Select the criteria against which the threshold is compared.
- Enter the threshold value. When the value crosses the established threshold for the criteria you select, the alarm triggers.
- Click Select Groups if the alarm only applies to a specific group of devices. Select the groups of devices in the Alarm Group Selection window and click OK. Not selecting any device groups means the alarm applies to all devices.
- Click the Actions tab to configure the actions performed when the alarm is triggered. Proceed to Step 6 for information about configuring rule actions.
- Select a Threshold Type.
- Click the Add drop-down menu to select the actions performed when the alarm is triggered.
- Add Email Action — Sends an email when the alarm is triggered. Use the Destination drop-down menu to select one of your pre-defined email lists. Management Center comes preloaded with a default email list called Helpdesk. You can rename this list, but it cannot be deleted. Click the Edit Email Lists button to define a new list. (You must have your SMTP E-Mail Server options configured.) There are default formats for the subject and body of the email you can override by selecting the Override Content checkbox. You can view a list of alarm keywords by clicking Show Keywords. Click the Save button to save the email action to the list of actions for the alarm definition.
- Add Syslog Action — Creates a syslog message when the alarm is triggered. Enter the IP address or hostname that identifies the syslog server where the message is sent. There is a default format for the syslog message sent to the server you can override by selecting the Override Content checkbox. You can view a list of alarm keywords by clicking Show Keywords. Click the Save button to save the syslog action to the list of actions for the alarm definition.
- Add Trap Action — Sends an SNMP trap when the alarm is triggered. Enter the IP address for a trap receiver where the trap is sent in the Trap Server field. Valid trap receivers are systems running an SNMP Trap Service. From the Credential drop-down menu, select the appropriate SNMP credential to use when sending the trap to the trap receiver. Credentials are defined in the Profiles/Credentials tab in the Authorization/Device Access window (Tools > Authorization/Device Access). There is a default format for the trap message you can override by selecting the Override Content checkbox. You can view a list of alarm keywords by clicking Show Keywords. Click the Save button to save the trap action to the list of actions for the alarm definition.
- Add Custom Action — Runs a custom program or script on the Management Center Server when the alarm is triggered. In the Program field, enter the name of the program. In the Working Directory field, enter the path to the directory from which the program is executed. Any path references within your program that are not absolute paths, are relative to the working directory. There is a default set of arguments passed to the program you can override by selecting the Override Content checkbox. You can view a list of alarm keywords by clicking Show Keywords. Click the Save button to save the email action to the list of actions for the alarm definition. For additional information, see How to Create Scripts.
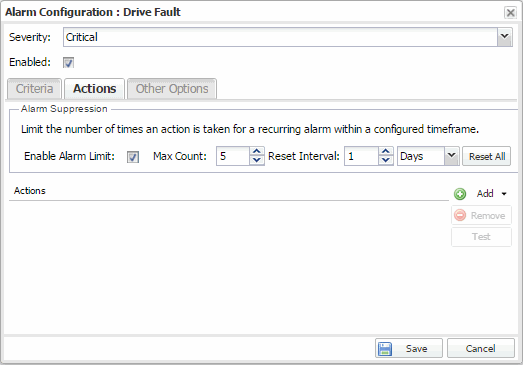
- If you want to set a limit on the number of times the system performs the alarm action for this alarm, check Enable Alarm Limit and type a number into the Max Count field. Once the limit is reached, the alarm is still recorded, but no further actions are performed. If you have configured multiple action types, the limit is for the number of times the set of configured actions is performed, not for each individual action. Each alarm source has its own action count for an alarm, so when the Max Count limit is reached for one alarm source, actions may still occur for other alarms from that alarm source as well as for other alarm sources. If Save is not checked, there is no limit placed on the number of times the action is performed.
- You can specify a Reset Interval which automatically resets the action count after the time limit specified, allowing actions to resume for that alarm source. If the reset interval is set to None, then once the alarm limit is reached, the alarm does not reset unless manually reset. You can reset the action counters for all alarm sources related to this alarm definition using the Reset All button. For example, if there is a Flow Limit Alarm on three devices, it resets the limits on those three alarms.
- You can test an alarm action by clicking the Test button. (You must save an alarm before you can test it.) You can also override the action.
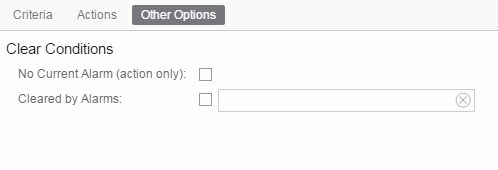
- In the Other Options subtab, select how you want to clear the alarm.
- No Current Alarm (action only) — When this option is selected, the trigger event causes the system to perform the configured actions, but does not raise an alarm that becomes associated with the alarm source. The alarm status of the alarm source does not change, and no alarm is added to the system.
- Cleared by Alarm — This option allows you to select the alarm(s) used to clear the alarm you are defining. You must first create the alarm definitions for the clearing alarms, which must have the alarm severity set to "Clear". The clearing alarms are triggered when the problem or condition is removed. Then, use the Select Alarms button to open a window to select one or more clearing alarms that clear the alarm you are defining.
- Click Save to create the alarm and close the Alarm Configuration window.
To modify an existing alarm:
- In the Alarm Configurations view, select the alarm definition you want to change.
- Double-click the Alarm Definition. You can also click the Edit button or right-click the alarm definition, and select Edit. The Alarm Configuration window opens.
- Edit the necessary fields. For additional information, see To create a new alarm definition.
- Click Save to edit the alarm definition and close the Alarm Configuration window.
Disabling Alarms
There may be times when you want to disable an alarm definition without deleting it. For example, you might want to temporarily disable a Device Down alarm definition while you are performing maintenance on that device.
To disable an alarm, open the Alarm Configuration view, right-click the alarm you want to disable, and select Disable.
Deleting Alarms
To completely remove an alarm definition you no longer use, you can delete the alarm definition from Management Center.
To delete an alarm, open the Alarm Configuration view, select the alarm definition you want to delete, and click the Delete button.
Configuring Email Settings
From the Alarm Configuration view, you can configure or edit the email address to which alarm information is sent for an alarm definition when the alarm is triggered.
To configure the email address to which alarm information is sent, open the Alarm Configuration view, select the alarm definition for which you want to configure or change the email settings, click the gear menu  or right-click the alarm definition and select Configure Email Settings.
or right-click the alarm definition and select Configure Email Settings.
Resetting Action Limits
Once an action limit is reached for an alarm, the action no longer occurs when an alarm is triggered. From the Alarm Configuration view, you can reset the action limits for your alarms so the actions occur when an alarm is triggered.
To reset the action limits, open the Alarm Configuration view, select the alarm definition for which you want to reset the action limits, click the gear menu  or right-click the alarm definition and select Reset Action Limits.
or right-click the alarm definition and select Reset Action Limits.
Enabling/Disabling All
From the Alarm Configuration view, you can enable or disable all of your alarms at once.
To enable or disable all of your alarms, open the Alarm Configuration view, click the gear menu  , and select Enable All or Disable All, respectively.
, and select Enable All or Disable All, respectively.
Restoring Default Alarms
From the Alarm Configuration view, you can restore the default alarms that you delete or modify.
To restore the default alarms, open the Alarm Configuration view, click the gear menu  , and select Restore Default Alarms.
, and select Restore Default Alarms.
| NOTE: | The time required to restore default alarms can vary. When the process is complete, you are notified by a confirmation window. |
Viewing Alarms
You can view device/alarm status in multiple places throughout Management Center.
Extreme Management Center
Every Management Center page includes a system-wide Alarm Summary in the lower right corner. This indicates the number of current alarms for each severity (Critical, Error, Warning, and Info) that is present in the entire system. If there are no current alarms, the status displays all zeroes. Click on an indicator to open the Alarms tab filtered to display the alarms of that severity.

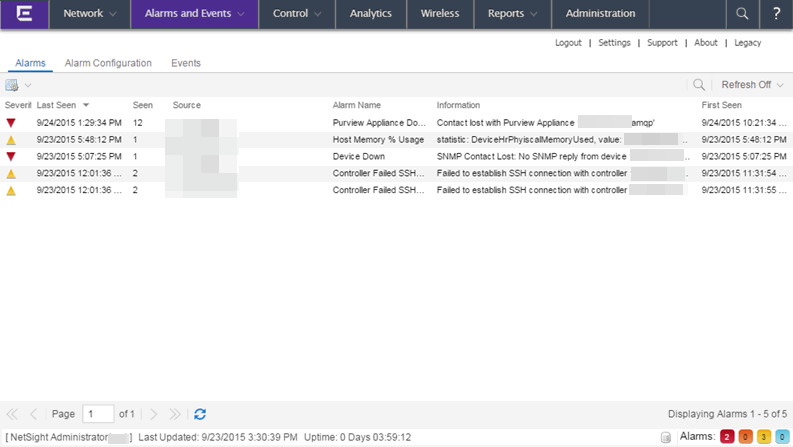
Alarms and Events Tab
You can view current alarm information in the Alarms view in the Alarms and Events tab. Use the configuration menu button or right-click on an alarm to clear the selected alarm or all alarms. If desired, you can supply a reason you cleared the alarm, which is recorded in the Alarm History.
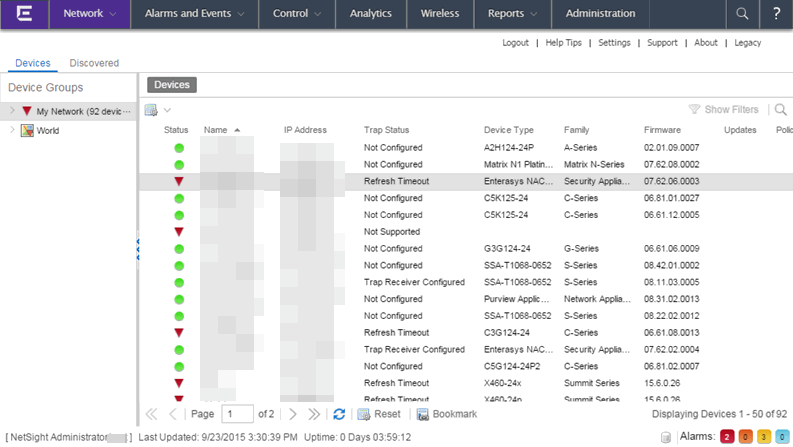
Network Tab
You can view the alarm status for a device in the Status column from within the My Network navigation tree on the Network tab. The colored circle indicates the severity of the most severe alarm on the device. A green icon indicates that there are no alarms and the device is up. A red icon indicates a critical alarm or the device is down. Double-click on the Status icon to open a new page with detailed information about the alarms for that device. For additional information, see Network tab help topic.
You can also view the alarm status for a device in device maps, found in the World map navigation tree. Topology and geographic maps show the status of devices in your network and floor plans show the status of wireless access points. As with devices in the My Network navigation tree, the colored circle associated with a device or access point in a map indicates the severity of the most severe alarm on the device. For additional information, see View and Search Maps.
Clearing Alarms
An alarm can be cleared manually or automatically.
In the Alarms view under the Alarms and Events tab, gear menu  in the upper left corner or right-click on an alarm to clear the selected alarm or all alarms. If desired, you can supply a reason that the alarm was cleared, which is recorded in the Alarm History.
in the upper left corner or right-click on an alarm to clear the selected alarm or all alarms. If desired, you can supply a reason that the alarm was cleared, which is recorded in the Alarm History.
To clear an alarm automatically:
An alarm is cleared automatically by another alarm called a "Clearing Alarm". For example, you can create a Device Up alarm so that when contact is established with a device, the alarm automatically clears a Device Down alarm.
Clearing Alarms are configured in the Alarm Configuration window with an Alarm Severity set to Clear. The alarm is defined so that when it is triggered, it removes an alarm rather than adds one.
In addition, a threshold alarm can be configured to "self-clear". For additional information, see How to Clear Threshold Alarms. This is called re-arming the alarm. Re-arming allows the threshold alarm to clear itself when the monitored statistic is restored to an acceptable range, without requiring a clearing alarm. When an alarm self-clears, no action is triggered.
For information on related concepts:
For information on related tasks: