If your network is implementing registration or assessment/remediation, you define the branding and behavior of the portal website used by the end user during the registration or assessment/remediation process using a Portal Configuration. Extreme Access Control engines ship with a default Portal Configuration. You can use this default configuration as is, or make changes to the default configuration using this window, if desired.
This Help topic provides the following information for accessing and configuring the Portal Configuration:
- Accessing the Portal Configuration
- Network Settings
- Administration
- Website Configuration
- Look and Feel
- Guest Web Access
- Guest Registration
- Secure Guest Access
- Authenticated Registration
- Authenticated Web Access
- Assessment/Remediation
- Portal Web Page URLs
Accessing the Portal Configuration
Use the following steps to access the Portal Configuration:
- Open the Control > Access Control tab.
- In the left-panel tree, expand the Portal tree.
- Expand a Portal Configuration.
Network Settings
Use this panel to configure common network web page settings that are shared by both the Assessment/Remediation and the Registration portal web pages.
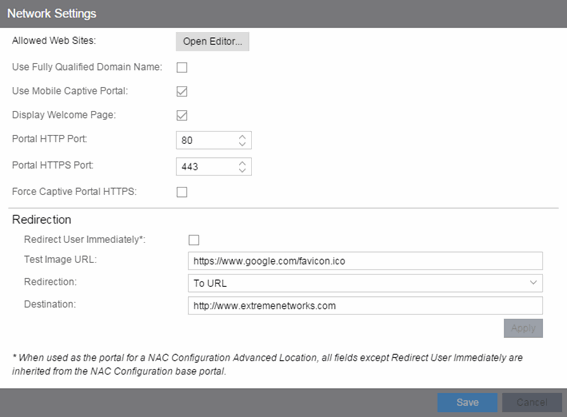
- Allowed Web Sites
- Click on the Open Editor button to open the Allowed Web Sites window, where you can configure the web sites to which end users are allowed access during the assessment/remediation and registration process.
- Use Fully Qualified Domain Name
- Select this checkbox if you would like the URLs in the portal web pages to display the engine's hostname instead of IP address. When this is enabled, the user's browser does a DNS lookup to find the IP address for the fully qualified hostname of the Extreme Access Control engine. Enable this option only if all Access Control engines have their hostname defined in DNS.
- Use Mobile Captive Portal
- Select this checkbox to allow end users using mobile devices to access the network via captive portal registration and remediation. In addition, it allows Helpdesk and IT administrators to track the status of registered end-systems, as well as add, modify, and delete registered end-systems on the network using a mobile device. This feature is supported on the following mobile devices: IPod Touch, IPad, IPhone, Android Phone/Tablet/NetBook, and Windows phones.
- Display Welcome Page
- Select this checkbox to display the welcome page. If the checkbox is not selected, users bypass the welcome page and access the portal directly.
- Portal HTTP Port
- Specify which port the Extreme Management Center server and Access Control engine use for HTTP web server traffic. Any change does not take effect on the Access Control engine until an Enforce is performed.
- Portal HTTPS Port
- Specify which port the Management Center server and Access Control engine use for HTTPS web server traffic. Any change does not take effect on the Access Control engine until an Enforce is performed.
- Force Captive Portal HTTPS
- Select this checkbox to force captive portal web pages to be served securely over HTTPS (instead of HTTP) to end users on the network. It is recommended this checkbox is enabled if Authenticated Registration is configured for the registration process. The default setting is unchecked, specifying to serve the captive portal web pages over HTTP.
This option redirects end users to the specified test image URL as soon as they have network access. The redirect happens regardless of where the end user is in the connection process. If the end-system's browser can reach the test image URL, then it assumes the end user has network access and redirects the end user out of the captive portal. The test image URL should be an internal image on your own website that end users don't have access to until they're accepted. It is recommended that the test image URL is a link to an SSL site because if the Access Control captive portal is configured for Force Captive Portal HTTPS, the browser does not allow the attempt to an HTTP test image site. It is also recommended that the captive portal policies, (typically the Unregistered, Assessing, and Quarantine policies), are configured to deny HTTPS traffic. This prevents the test image connection attempt from successfully completing and moving the end-system out of the captive portal prematurely. In the event access to the test image is available, the user may experience the captive portal reverting to the "click here to access the network page", and then upon selecting the link, returning to the previous page based on their state. This behavior continues until the user is finally accepted on the network.
| NOTE: | If using the portal for an Access Control Advanced Location, all portal configurations are inherited from the Access Control base portal. |
|---|
- Redirection
- There are three Redirection options that specify where the end user is
redirected following
successful registration or remediation, when the end user is allowed on the
network:
- To URL — This option lets you specify the URL for the web page where the end user is redirected. When selected, the Destination field displays, allowing you to indicate the URL of the web page.
- Disabled — This option disables redirection. The end user stays on the same web page where they were accepted onto the network.
- To User's Requested URL — This option redirects the end user to the web page they originally requested when they connected to the network.
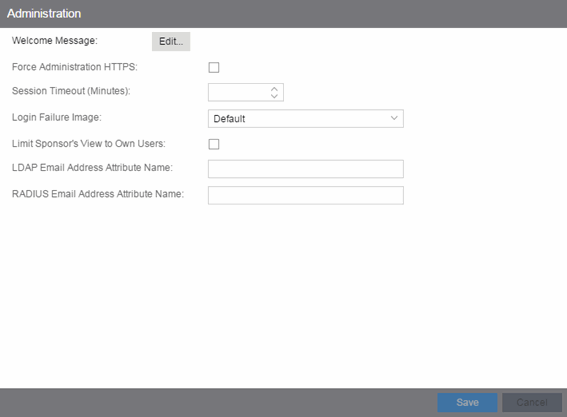
Administration
Use this panel to configure settings for the Registration Administration web page and grant access to the page for administrators and sponsors.
The Registration Administration web page allows Helpdesk and IT administrators to track the status of registered end-systems, as well as add, modify, and delete registered end-systems on the network.
Administration Web Page Settings
- Welcome Message
- Click on the Edit button to open a window where you can modify the message displayed to users when they log into the administration or sponsor portal. The default welcome message is Registration System Administration.
- Force Administration HTTPS
- Select this checkbox to force the administration web page to be served securely over HTTPS (instead of HTTP) to administrators and sponsors on the network. It is recommended this is enabled for additional security.
- Session Timeout (Minutes)
- This field specifies the length of time an administrator can be inactive on the administration web page before automatically being logged out. The default value is 10 minutes.
- Login Failure Image
- Select an image to display when the end user fails to correctly log in to the web page. The drop-down selection menu displays all the images defined in the Images window for your selection. To add a new image, access the Look & Feel panel.
- Limit Sponsor's View to Own Users
- Select this checkbox if you want to limit a sponsor's view to only the users they have sponsored. This option is valid only if you configure LDAP or RADIUS authentication of your sponsors. If you select this checkbox, you must enter the LDAP Email Address Attribute Name or RADIUS Email Address Attribute Name so a sponsor's login name can be matched to their email address, and only the registered users for that sponsor are displayed.
Website Configuration
Use this tab to configure the common settings used by the different registration web pages, including selecting guest access, authentication settings, and whether assessment and remediation is supported. The options selected in this panel change the panels displayed in the left-panel Website Configuration tree.
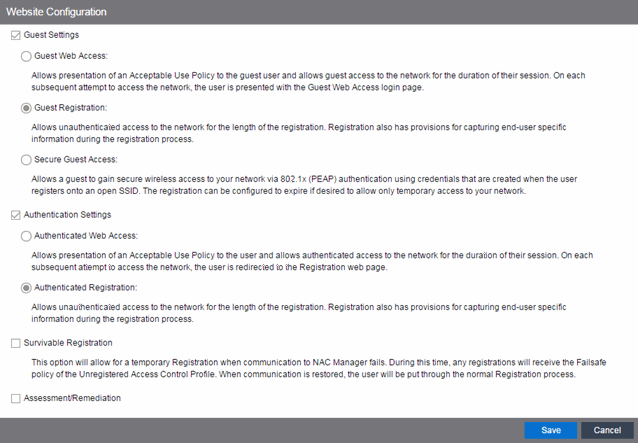
- Guest Settings
- Select the behavior of the web site for users with guest access and the level of access to your network. For additional information, see the Guest Web Access, Guest Registration, and Secure Guest Access sections.
- Authentication Settings
- Select the behavior of the web site for users with authentication credentials and their level of access to your network. For additional information, see the Authenticated Web Access and Authenticated Registration sections.
- Enable Survivable Registration
- This feature provides temporary Registration for unregistered end-systems when the Extreme Management Center server is unreachable. If you select this checkbox, unregistered users that try to register while the Management Center server is unreachable are redirected to the Registration web page. After entering the required information, users are assigned the Failsafe policy and allowed on the network. Once the connection to the Management Center server is reestablished, the users are reassigned the Unregistered policy and forced to re-register. If you enable Survivable Registration, make sure that the Failsafe policy provides the appropriate network services for unregistered users.
- Assessment/Remediation
- Allows you to configure the behavior of the Assessment/Remediation web portal. For additional information, see the Assessment/Remediation section.
Look and Feel
Use this panel to configure common web page settings shared by both the Assessment/Remediation and the Registration portal web pages.
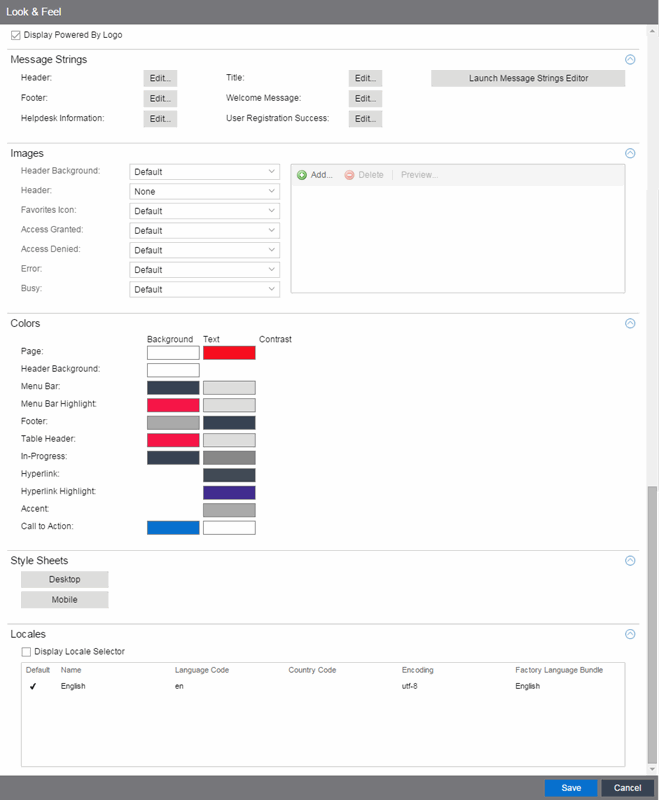
- Display Powered by Logo
- Select this checkbox to display the Extreme Networks logo at the bottom of all of your portal web pages.
- Header
- Click on the Edit button to open a window where you can configure the link for the header image displayed at the top of all portal web pages. By default, the header image is configured as the Extreme Networks logo acting as a link to the Extreme Networks website. Text entered in this window can be formatted in HTML.
- Footer
- Click on the Edit button to open a window where you can configure the footer displayed at the bottom of all portal web pages. By default, the footer is configured with generalized information concerning an organization. Change the example text in this section to customize the footer to your own organization. Text entered in this window can be formatted in HTML.
- Helpdesk Information
- Click on the Edit button to open a window where you can configure the Helpdesk contact information provided to end users in various scenarios during the assessment/remediation and registration process (e.g. an end-system exceeded the maximum number of remediation attempts). By default, this section is configured with generalized Helpdesk information, such as contact URL, email address, and phone number. Change the example text to customize the Helpdesk information for your own organization. Text entered in this window can be formatted in HTML. In addition, the entire contents of the Helpdesk Information section are stored in the variable "HELPDESK_INFO". By entering "HELPDESK_INFO" (without the quotation marks) in any section that accepts HTML in the Common Page Settings (or any other settings), all information configured in this section will be displayed in place of "HELPDESK_INFO".
- Title
- Click on the Edit button to open a window where you can modify the text that appears in the title bar of the registration and web access page browser tabs. The default page title is "Enterprise Registration."
- Welcome Message
- Click on the Edit button to open a window where you can modify the message displayed to users on the menu bar of any registration or web access page. The default welcome message is "Welcome to the Enterprise Network's Registration Center."
- User Registration Success
- Click the Edit button to open a window where you can edit the message displayed to the end user after successfully registering their end-system to the network.
- Images
- Using the dropdown menus, you can specify the image files used in the
portal web pages. All
image files used for Assessment/Remediation and Registration portal web pages must be
defined in this list. The image
files defined here are sent to the Extreme Access Control engine along with the
web page configuration. Use the Add button to select an image file to add to the list. You can select an image
in the list and use the Preview button to preview the image.
Once an image file is defined here, it is available for selection from the configuration drop-down lists (for example, when you configure the Access Granted Image), and may be referenced in the sections supporting HTML. Available drop-down lists include:- Header Background Image
- Select the background image displayed behind the header image at the top of all portal web pages. The drop-down menu displays all the images defined in the Images window for your selection. To add a new image, select Add to open the Images window.
- Header Image
- Select the image displayed
at the top of all portal web pages. The drop-down menu displays all
the images defined in the Images window for
your selection. To add a new image, select Add to open the Images window.
- Favorites Icon
- Select the image displayed as the Favorites icon in the web browser tabs. The drop-down menu displays all the images defined in the Images window for your selection. To add a new image, select Add to open the Images window.
- Access Granted Image
- Select the image displayed when the end user is granted access to the network either based on compliance with the network security policy or upon successful registration to the network. The drop-down menu displays all the images defined in the Images window for your selection. To add a new image, select Add to open the Images window.
- Access Denied Image
- Select the image you would like displayed when the end user has been denied access to the network. The drop-down selection list displays all the images defined in the Images window for your selection. To add a new image, select Manage Images to open the Images window.
- Error Image
- Select the image displayed when there is a communication error with the Extreme Management Center Server. The drop-down menu displays all the images defined in the Images window for your selection. To add a new image, select Add to open the Images window.
- Busy Image
- Select the progress bar image displayed to the end user when the web page is busy processing a request. The drop-down menu displays all the images defined in the Images window for your selection. To add a new image, select Add to open the Images window.
- Colors
- Click on the Background or Text color box corresponding to each item to open the Choose Color window, displayed below, where you can
define the colors used in the portal web pages:
- Page — Define the background color and the color of all primary text on the web pages.
- Header Background Color — Define the background color displayed behind the header image.
- Menu Bar — Define the background color and text color for the menu bar.
- Menu Bar Highlight — Define the background color and text color used for the menu bar highlights in the Administration pages.
- Footer — Define the background color and text color for the footer.
- Table Header — Define the background color and text color for the table column headers in the Administrative web pages.
- In-Progress — Define the background color and text color for task in-progress images.
- Hyperlink — Define the color used for hyperlinks on the web pages.
- Hyperlink Highlight — Define the color of a hyperlink when it is highlighted.
- Accent — Define the color used for accents on various parts of the web pages.
Click OK to save the changes.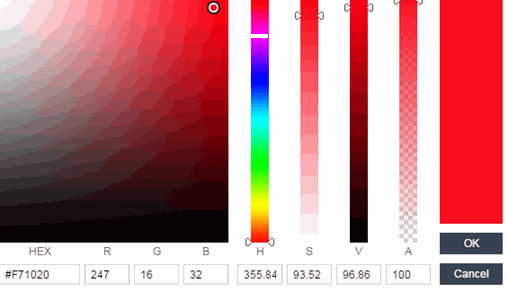
- Style Sheets
- Click on the Desktop or Mobile buttons to open the Edit Style Sheet window where you can create a style sheet that adds to or overwrites the formatting styles for the portal, or mobile version of the portal web pages, respectively.
- Locales
- This field lists the locales (languages) presented as options to the user in the captive portal, in addition to the default locale.
You can also define the default locale (language), displayed to any captive portal user unless the client locale detected from their browser matches one of the defined supplemental locales. The list of available locales includes the current default locale and any supplemental defined locales.
- Display Locale Selector
- Select this checkbox if you want a locale (language) selector to display as a drop-down menu in the menu bar on the captive portal welcome and login pages. This is useful for a shared machine where the users of the machine may speak different languages. (On the mobile captive portal, the selector is displayed as a list of links at the bottom of the welcome screen.)
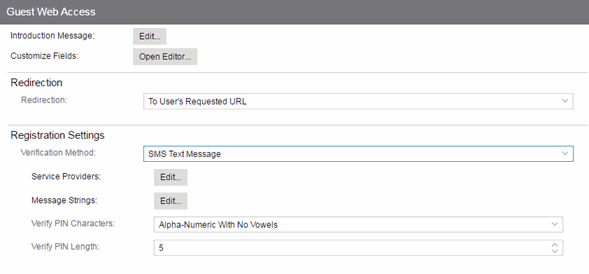
Guest Web Access
Guest Web Access provides a way for you to inform guests that they are connecting to your network and lets you display an Acceptable Use Policy (AUP).
End users are initially redirected to the captive portal when they first connect to the network. After the user enters the required information on the Guest Web Access login page (typically, their name and email address), they are allowed access on the network according to the assessment and authorization defined in the Guest Access profile.
Guest web access provides a single session, and no permanent end user records are stored. This provides increased network security, and also allows you to minimize the number of registration records stored in the Extreme Management Center database.
Implementing guest web access requires web redirection or DNS proxy.
- Introduction Message
- Click the Edit button to open a window where you can edit the introductory message displayed to end users when gaining web access as guests. It may include an introduction to the network and information stating that the end user is agreeing to the Acceptable Use Policy (AUP) for the network upon registering their device. A link to the URL that contains the full terms and conditions of the network's AUP can be provided from this introductory message. Note that the URL for this link must be added as an Allowed URL in the Allowed Web Sites window accessed from the Network Settings. By configuring the introductory message with this information, end users can be held accountable for their actions on the network in accordance with the terms and conditions set forth by the network's AUP. This message is shared by Guest Web Access and Guest Registration. Changing it for one access type also changes it for the other.
- Customize Fields
- Click the Open Editor button to open the Manage Custom Fields window where you can manage the fields displayed in the Guest Web Access login page. These settings are shared by Guest Web Access, Guest Registration, and Secure Guest Access. Changing them for one access type also changes them for the others.
- Redirection (Shared)
- There are four Redirection options that specify where the end user is
redirected following successful access, when the end user
is allowed on the network. The option selected here overrides the Redirection option specified on the Network Settings. This setting is shared by Guest Web Access, Guest Registration, and Secure Guest Access.
Changing it for one access type also changes it for the others.
- Use Network Settings Redirection — Use the Redirection option specified on the Network Settings.
- Disabled — This option disables redirection. The end user stays on the same web page where they were accepted onto the network.
- To User's Requested URL — This option redirects the end user to the web page they originally requested when they connected to the network.
- To URL — This option lets you specify the URL for the web page where the end user will be redirected. This would most likely be the home page for the enterprise website, for example, "http://www.ExtremeNetworks.com."
Registration Settings
- Verification Method
- User verification requires that guest end users registering to the network enter a verification code that is sent to their email address or mobile phone (via SMS text) before gaining network access. This ensures that network administrators have at least one way to contact the end user. For more information and complete instructions, see How to Configure Verification for Guest Registration.
- Select from the following verification methods:
-
- Email — The end user must enter an email address in the Guest Web Access login page. The Email Address field must be set to Required in the Manage Custom Fields window.
- SMS Gateway — The end user must enter a mobile phone number in the Guest Web Access login page. The Phone Number field must be set to Required in the Manage Custom Fields window.
- SMS Gateway or Email — The end user must enter a mobile phone number or email address in the Guest Web Access login page. The Phone Number and Email Address fields must be set to Visible in the Manage Custom Fields window.
- SMS Text Message — The end user must enter a mobile phone number in the Guest Web Access login page. The Phone Number field must be set to Required in the Manage Custom Fields window.
- SMS Text or Email — The end user must enter either a mobile phone number or email address in the Guest Web Access login page. The Phone Number and Email Address fields must be set to Visible in the Manage Custom Fields window.
- If you have selected the "SMS Text Message" or the "SMS Text or Email" Verification method: click the Service Providers Edit button (below the verification method) to configure the list of mobile service providers from which end users can select on the Registration web page. This setting allows Extreme Access Control to correctly format the email address to which to send an email. This email is then received by the service provider and converted to an SMS text which is sent the user. The default configuration provides lists of the major US cellular service providers.
NOTE: Not all cellular service providers provide a way to send SMS text messages via email.
If you have selected the "SMS Gateway" or "SMS Gateway or Email" method: enter the SMS Gateway Email address provided by the SMS Gateway provider.
For all methods: use the Message Strings Edit button (below the verification method) to open the Message Strings Editor and modify the registration verification messages displayed to the user during the verification process. For example, if you have selected Email, you need to modify the "registrationVerificationEmailSentFromAddress" message string to be the appropriate email address for your company.
For all methods: set the Verify Pin Characters and Verify Pin Length options to define the characteristics and length of the verification code that is sent to the guest end user. This setting is shared by Guest Registration and Guest Web Access. Changing it for one access type also changes it for the other.
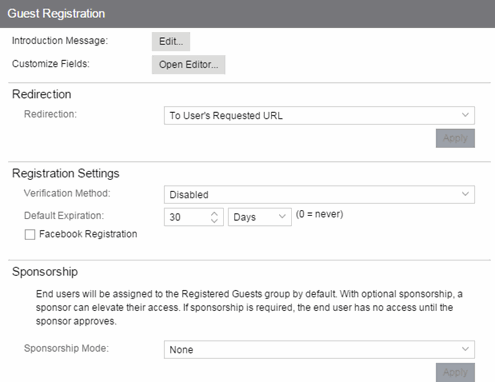
Guest Registration
Guest registration forces any new end-system connecting on the network to provide the user's identity in the registration web page before being allowed access to the network. Guests are initially redirected to a web page for registering their end-system when it is first connected to the network. After successful registration, the end-system is permitted access until the registration expires or is administratively revoked.
The end user's level of network access is determined by the settings specified here, and whether they are required to have a sponsor. With sponsored registration, end users are only allowed to register to the network when approved by a "sponsor," an internal trusted user to the organization. Sponsorship can provide the end user with a higher level of access than just guest registration and allows the sponsor to fine-tune the level of access for individual end users. The end user registers and declares a sponsor's email address. The sponsor is notified and approves the registration, and can assign an elevated level of access, if desired.
| NOTE: | If you configure both Guest Registration and Authenticated Registration for an area on your network, the end user is presented with a choice on the registration web page whether or not to authenticate. |
- Introduction Message
- Click the Edit button to open a window where you can edit the introductory message displayed to end users when registering as guests. It may include an introduction to the network and information stating that the end user is agreeing to the Acceptable Use Policy (AUP) for the network upon registering their device. A link to the URL that contains the full terms and conditions of the network's AUP can be provided from this introductory message. Note that the URL for this link must be added as an Allowed URL in the Allowed Web Sites window accessed from the Network Settings. By configuring the introductory message with this information, end users can be held accountable for their actions on the network in accordance with the terms and conditions set forth by the network's AUP. This message is shared by Guest Web Access and Guest Registration. Changing it for one access type also changes it for the other.
- Customize Fields
- Click the Open Editor button to open the Manage Custom Fields window where you can manage the fields displayed in the Registration web page. These settings are shared by Guest Web Access, Guest Registration, and Secure Guest Access. Changing them for one access type also changes them for the others.
- Redirection
- There are four Redirection options that specify where the end user is
redirected following successful registration, when the end user
is allowed on the network. The option selected here overrides the Redirection option specified on the Network Settings. This setting is shared by Guest Web Access, Guest Registration, and Secure Guest Access.
Changing it for one access type also changes it for the others.
- Use Network Settings Redirection — Use the Redirection option specified on the Network Settings.
- Disabled — This option disables redirection. The end user stays on the same web page where they were accepted onto the network.
- To User's Requested URL — This option redirects the end user to the web page they originally requested when they connected to the network.
- To URL — This option lets you specify the URL for the web page where the end user is redirected. This would most likely be the home page for the enterprise website, for example, "http://www.ExtremeNetworks.com."
Registration Settings
- Verification Method
- User Verification requires that guest end users registering to the network enter a verification code sent to their email address or mobile phone (via SMS text) before gaining network access. This ensures that network administrators have at least one way to contact the end user.
-
Select from the following verification methods: -
- Email — The end user must enter an email address in the Registration web page. The Email Address field must be set to Required in the Manage Custom Fields window.
- SMS Gateway — The end user must enter a mobile phone number in the Registration web page. The Phone Number field must be set to Required in the Manage Custom Fields window.
- SMS Gateway or Email — The end user must enter a mobile phone number or email address in the Registration web page. The Phone Number and Email Address fields must be set to Visible in the Manage Custom Fields window.
- SMS Text Message — The end user must enter a mobile phone number in the Registration web page. The Phone Number field must be set to Required in the Manage Custom Fields window.
- SMS Text or Email — The end user must enter either a mobile phone number or email address in the Registration web page. The Phone Number and Email Address fields must be set to Visible in the Manage Custom Fields window.
- If you have selected the "SMS Text Message" or the "SMS Text or Email" Verification method: click the Service Providers link (below the verification method) to configure the list of mobile service providers from which end users can select on the Registration web page. This setting allows Extreme Management Center to correctly format the email address to which to send an email. This email is then received by the service provider and converted to an SMS text which is sent the user. The default configuration provides lists of the major US cellular service providers. NOTE: Not all cellular service providers provide a way to send SMS text messages via email.
If you have selected the "SMS Gateway" or "SMS Gateway or Email" method: enter the SMS Gateway Email address provided by the SMS Gateway provider.
For all methods: use the Message Strings link (below the verification method) to open the Message Strings Editor and modify the registration verification messages displayed to the user during the verification process. For example, if you have selected Email, you need to modify the "registrationVerificationEmailSentFromAddress" message string to be the appropriate email address for your company.
For all methods: set the Verify Pin Characters and Verify Pin Length options to define the characteristics and length of the verification code sent to the guest end user. This setting is shared by Guest Registration and Guest Web Access. Changing it for one access type also changes it for the other.
- Default Expiration
- Enter a value and select a unit of time to configure the amount of time before an end user's registration automatically expires. When the registration expires, the end user is either suspended (registration must be manually approved by administrator/sponsor) or permanently deleted from the guest registration list. If a registration is deleted, the end-user must re-enter all their personal information the next time they attempt to access the network. Individual expiration time can also be set by a sponsor.
Facebook Registration
Select the Facebook Registration checkbox if you are implementing guest registration using Facebook as a way to obtain end user information. In this scenario, the Guest Registration portal provides the end user with an option to log into Facebook in order to complete the registration process. For more information, see How to Implement Facebook Registration for steps on how to create a Facebook application. When you create an application you are given a Facebook App ID and Facebook App Secret to enter here.
Sponsorship
Use this section to configure sponsorship for Guest Registration. Select the Sponsorship Mode required. Additional settings display if you select optional or required sponsorship. For information on each option, see How to Configure Sponsorship for Guest Registration.
With sponsored registration, end users are only allowed to register to the network when approved by a "sponsor," an internal trusted user to the organization. Sponsorship can provide the end user with a higher level of access than just guest registration and allows the sponsor to fine-tune the level of access for individual end users. The end user registers and declares a sponsor's email address. The sponsor is notified and approves the registration, and can assign an elevated level of access, if desired.
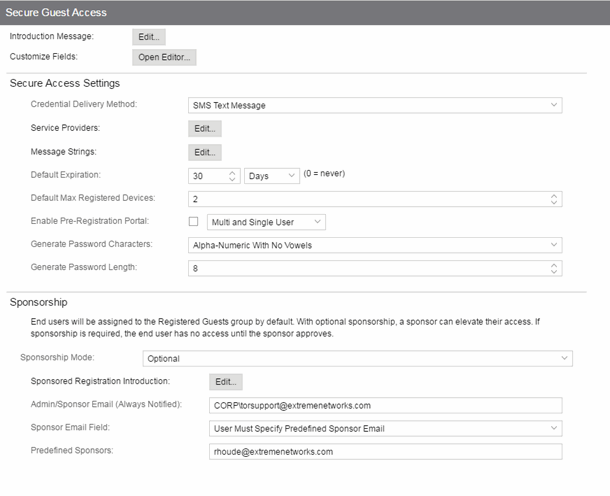
Secure Guest Access
Secure Guest Access provides secure network access for wireless guests via 802.1x PEAP by sending a unique username, password, and access instructions for the secure SSID to guests via an email address or mobile phone (via SMS text). Secure Guest Access supports both pre-registered guests and guests self-registering through the captive portal. No agent is required.
Here are three scenarios where Secure Guest Access provides increased network security:
- An enterprise provides secure guest access for visitors. Guests self-register through the captive portal and receive connection credentials and instructions for the secure SSID via a text message on their mobile phone.
- A hospitality company provides guests with secure Internet access using pre-registration. A receptionist generates a voucher using the Extreme Access Control pre-registration portal. The voucher is handed to the guest, providing them with instructions and credentials for connecting directly to the secure SSID.
- An enterprise provides secure guest access with the option of elevated access through employee sponsors. Guests self-register through the captive portal and receive connection credentials and instructions via a text message. Sponsors approve guests for secure guest access. Later, sponsors can elevate guest access using the sponsorship portal.
- Introduction Message
- Click the Edit button to open a window where you can edit the introductory message displayed to end users when registering as guests. It may include an introduction to the network and information stating that the end user is agreeing to the Acceptable Use Policy (AUP) for the network upon registering their device. A link to the URL that contains the full terms and conditions of the network's AUP can be provided from this introductory message. Note that the URL for this link must be added as an Allowed URL in the Allowed Web Sites window accessed from the Network Settings. By configuring the introductory message with this information, end users can be held accountable for their actions on the network in accordance with the terms and conditions set forth by the network's AUP. This message is shared by Guest Web Access and Guest Registration. Changing it for one access type also changes it for the other.
- Customize Fields
- Click the Open Editor button to open the Manage Custom Fields window where you can manage the fields displayed in the Registration web page. These settings are shared by Guest Web Access, Guest Registration, and Secure Guest Access. Changing them for one access type also changes them for the others.
Secure Access Settings
- Credential Delivery Method
- Select the method that will be used to send guests their credentials and access instructions for the secure SSID. For more information and complete instructions, see How to Configure Credential Delivery for Secure Guest Access.
-
- Captive Portal — The credential information displays on the Registration web page.
- Email — The end user must enter an email address in the Registration web page. The Email Address field must be set to Required in the Manage Custom Fields window.
- SMS Gateway — The end user must enter a mobile phone number in the Registration web page. The Phone Number field must be set to Required in the Manage Custom Fields window.
- SMS Gateway or Email — The end user must enter a mobile phone number or email address in the Registration web page. The Phone Number and Email Address fields must be set to Visible in the Manage Custom Fields window.
- SMS Text Message — The end user must enter a mobile phone number in the Registration web page. The Phone Number field must be set to Required in the Manage Custom Fields window.
- SMS Text or Email — The end user must enter either a mobile phone number or email address in the Registration web page. The Phone Number and Email Address fields must be set to Visible in the Manage Custom Fields window.
- If you have selected the "SMS Text Message" or the "SMS Text or Email" Verification method: click the Service Providers Edit button (below the verification method) to configure the list of mobile service providers from which end users can select on the Registration web page. This setting allows Extreme Access Control to correctly format the email address to which to send an email. This email is then received by the service provider and converted to an SMS text which is sent the user. The default configuration provides lists of the major US cellular service providers.
NOTE: Not all cellular service providers provide a way to send SMS text messages via email.
If you have selected the "SMS Gateway" or "SMS Gateway or Email" method: enter the SMS Gateway Email address provided by the SMS Gateway provider. - For all methods: use the Message Strings Edit button (below the verification method) to open the Message Strings Editor and modify the registration verification messages displayed to the user during the verification process. For example, if you have selected "Email", you need to modify the "secureGuestAccessEmailSentFromAddress" message string to be the appropriate email address for your company.
- Default Expiration
- Enter a value and select a unit of time to configure the amount of time before an end user's registration automatically expires. When the registration expires, the end user is either suspended (registration must be manually approved by administrator/sponsor) or permanently deleted from the guest registration list. If a registration is deleted, the end-user must re-enter all their personal information the next time they attempt to access the network. Individual expiration time can also be set by the sponsor.
- Default Max Registered Devices
- Specify the maximum number of MAC addresses each authenticated end user is allowed to register on the network. If a user attempts to register an additional MAC address that exceeds this count, an error message is displayed in the Registration web page stating that the maximum number of MAC addresses has already been registered to the network and to call the Helpdesk for further assistance. The default value for this field is 2.
- Enable Pre-Registration Portal
- Use this checkbox to enable Pre-Registration functionality. With pre-registration, guest users can be registered in advance, allowing for a more streamlined and simple registration process when the guest user connects to the network. This can be particularly useful in scenarios where guest users will be attending a company presentation, sales seminar, or a training session. From the drop-down menu, select whether you want to pre-register a single user (when you want to pre-register one user at time) or multiple users (when you have a larger group of users to pre-register) or both. For more information, see How to Configure Pre-Registration.
- Generate Password Characters (Shared)
- Extreme Access Control uses this option when generating passwords for guest users who are either self-registering or are pre-registered, to use when connecting to the network. This setting is shared by Authenticated Registration and Secure Guest Access. Changing it for one access type also changes it for the other.
- Generate Password Length (Shared)
- NAC Manager will use this option when generating passwords for guest users who are either self-registering or are pre-registered, to use when connecting to the network. The password length is generated according to the number of characters specified here. This setting is shared by Authenticated Registration and Secure Guest Access. Changing it for one access type also changes it for the other.
Sponsorship
Use this section to configure sponsorship for Secure Guest Access registration. Select the Sponsorship Mode required. Additional settings are displayed if you select optional or required sponsorship. For information on each option, see How to Configure Sponsorship for Guest Registration.
With sponsored registration, end users are only allowed to register to the network when approved by a "sponsor," an internal trusted user to the organization. Sponsorship can provide the end user with a higher level of access than just guest access and allows the sponsor to fine-tune the level of access for individual end users. The end user registers and declares a sponsor's email address. The sponsor is notified and approves the registration, and can assign an elevated level of access, if desired.
Authenticated Web Access
Authenticated web access provides a way to inform end users that they are connecting to your network and lets you display an Acceptable Use Policy.
End users are required to authenticate to the network using the Authenticated Web Access login page. However, end users are only granted one-time network access for a single session, and no permanent end user registration records are stored. Authentication is required each time a user logs into the network, which can be particularly useful for shared computers located in labs and libraries.
Implementing authenticated web access requires web redirection or DNS proxy.
This functionality is not yet available.
Authenticated Registration
Authenticated registration provides a way for existing corporate end users to access the network on end-systems that don't run 802.1X (such as Linux systems) by requiring them to authenticate to the network using the registration web page. After successful registration, the end-system is permitted access until the registration expires or is administratively revoked.
It is recommended that the Force Captive Portal HTTPS option is enabled if authenticated registration is required for security reasons.
| NOTE: | If you configure both guest registration and authenticated registration for an area on your network, the end user is presented with a choice on the registration web page whether or not to authenticate. |
|---|
These settings are shared by the Authenticated Web Access and Authenticated Registration access types. Changing them for one type also changes them for the other.
- Login or Register Message
- Click the Edit button to open a window where you can edit the message displayed to the end user when they are registering. By default, the message states that the end user is required to register before being allowed on the network.
- Introduction Message
- Click the Edit button to open a window where you can edit the introductory message displayed to the end user when they are registering. By default, the message states that the end user is agreeing to the terms and conditions in the Acceptable Use Policy.
- Failed Authentication Message
- Click the Edit button to open a window where you can edit the message displayed to the end user if the end user fails authentication. By default, this message advises the end user to contact their network administrator for assistance. Note that the default configuration of the message references the "HELPDESK_INFO" variable which represents the Helpdesk Information that is defined in the Look and Feel Settings.
- Customize Fields (Shared)
- Click the Open Editor button to open the Manage Custom Fields window where you can manage the fields displayed in the Registration web page.
Authentication
These settings are shared by the Authenticated Web Access and Authenticated Registration access types. Changing them for one type also changes them for the other.
- AAA Configuration
- This section displays the name of the AAA configuration being used by the Access Control configuration and provides a link to open the AAA Configuration window where you can make changes to the AAA Configuration, if desired. If the portal configuration is shared between multiple Access Control Configurations using different AAA configurations, the different AAA configurations are listed here (maximum of 3), allowing you to open the appropriate AAA configuration.
- The section also displays the method(s) utilized for validating the credentials entered during registration (LDAP, RADIUS, and/or a Local Password Repository) as specified in the AAA configuration(s).
-
- Authentication to End-System Group — Click the Change button to open the User Group to End-System Group Map window where you can map the LDAP/RADIUS/Local User Group to the appropriate end-system group to specify end user access levels. Once an end-system group has been mapped to a user group, the icon for the end-system group changes to display a key indicating that it is no longer available for general use. You can use the Move Up/Move Down arrows to set the precedence order for the mappings, allowing you to change the authentication order that takes place during the user authenticated registration.
- Local Password Repository — If you are using a local repository, authenticated end users are assigned to the Web Authenticated Users group. Click the Default button to open a window where you can edit the Local Password Repository. Multiple links may be listed if there are different repositories associated with different AAA configurations.
- Max Failed Logins
- Select this checkbox to specify the maximum consecutive number of times an end user can attempt to authenticate on an end-system and fail. You can specify a lockout period that must elapse before the user can attempt to log in again on that end-system.
Redirection
These settings are shared by the Authenticated Web Access and Authenticated Registration access types. Changing them for one type also changes them for the other.
- Redirection
- There are four Redirection options that specify where the end user is
redirected following successful registration, when the end user
is allowed on the network. The option selected here overrides the Redirection option specified on the Network Settings.
- Use Network Settings Redirection — Use the Redirection option specified on the Network Settings.
- Disabled — This option disables redirection. The end user stays on the same web page where they were accepted onto the network.
- To User's Requested URL — This option redirects the end user to the web page they originally requested when they connected to the network.
- To URL — This option lets you specify the URL of the web page to which the end user is redirected. This is typically the home page for the enterprise website, for example, "http://www.ExtremeNetworks.com."
Registration Settings
The Generate Password Character and Generate Password Length settings are shared by Authenticated Registration and Secure Guest Access.
- Default Maximum Registered Devices
- Specify the maximum number of MAC addresses each authenticated end user is allowed to register on the network. If a user attempts to register an additional MAC address that exceeds this count, an error message is displayed in the Registration web page stating that the maximum number of MAC addresses is registered to the network and to call the Helpdesk for further assistance. The default value for this field is 2.
- Default Expiration
- Enter a value and select a unit of time to configure the amount of time before an end user's registration automatically expires. When the registration expires, the end user is either suspended (registration must be manually approved by administrator/sponsor) or permanently deleted from the registration list. If a registration is deleted, the end-user must re-enter all their required personal information the next time they attempt to access the network. Individual registration expiration time can also be set by the administrator/sponsor through the Registration Administration web page.
- Delete Expired Users
- Select this checkbox to delete a user from the Registered users list in the Registration Administration web page when their registration expires. If a registration is deleted, the end-user must re-enter all their required personal information the next time they attempt to access the network.
- Delete Local Password Repository Users
- If you select Delete Expired Users, then selecting this checkbox also deletes the expired user from the local password repository.
- Enable Self-Registration Portal
-
This checkbox allows an authenticated and registered user to be directed
to a URL (provided by an administrator) to self-register additional
devices that may not support authentication (such as Linux machines) or may not have a web browser
(such as game systems). For example, a student may register to the network
using their PC. Then, using a self-registration URL provided by the system
administrator, they can register their additional devices. Once the additional
devices have been registered, the student can access the network using those
devices. The URL for the Self Registration web page is
https://<Access ControlEngineIP>/self_registration. You can change the instructions displayed on this web page using the Message Strings Editor on the Look and Feel Settings; select the selfRegIntro message string.
- Enable Pre-Registration Portal
- Select this checkbox to enable pre-registration functionality. With pre-registration, guest users can be registered in advance, allowing for a more streamlined and simple registration process when the guest user connects to the network. This is useful in scenarios where guest users are attending a company presentation, sales seminar, or a training session. From the drop-down menu, select whether you want to pre-register a single user (when you want to pre-register one user at time) or multiple users (when you have a larger group of users to pre-register) or both. For more information, see How to Configure Pre-Registration.
- Pre-Registration Expiration at First Login
- Select this checkbox to set the Default Expiration of a pre-registered user to begin when the user first registers a device, instead of setting it the moment the pre-registered user is created (added via the pre-registration administration process). Select Enable Pre-Registration Portal to enable this option. For more information, see
How to Configure Pre-Registration.
NOTE: This option is only valid when importing a CSV file to pre-register multiple users in the Pre-Registration Portal and not when entering information for a single user.
- Generate Password Characters
- This option is available if you select Enable Pre-Registration Portal. During the pre-registration process, Management Center can automatically generate the password that the guest user uses when connecting to the network. The password is generated according to the specification selected here. This setting is shared by Authenticated Registration and Secure Guest Access. Changing it for one access type also changes it for the other.
- Generate Password Length
- This option is available if you select Enable Pre-Registration Portal. During the pre-registration process, Management Center can automatically generate the password that the guest user uses when connecting to the network. The password length is generated according to the number of characters specified here. This setting is shared by Authenticated Registration and Secure Guest Access. Changing it for one access type also changes it for the other.
Assessment/Remediation
Use this panel to configure settings for the Assessment/Remediation portal web page.
Web Page Settings
- Title
- Click the Edit button to open a window where you can modify the message displayed in the title bar of the Assessment/Remediation web pages. The default page title is "Enterprise Remediation."
- Welcome Message
- Click the Edit button to open a window where you can modify the message displayed in the banner at the top of the Assessment/Remediation web page. The default welcome message is "Welcome to the Enterprise Remediation Center."
- Display Violations
- Use the checkboxes to select the assessment
violation
information that displays to the end user:
- None — No violations are displayed to the web page. This option might be used for an Access Controlengine that is serving web pages to guest users, when you do not want the guest users to attempt to remediate their end-system.
- Description — Only the description is displayed for violations. This provides the end user with information concerning what violation was found, but no information concerning how it can be fixed. This configuration may be appropriate for scenarios where the user population of the network does not possess technical IT knowledge and is not expected to self-remediate. It provides the Helpdesk personnel with technical information about the violation when the end user places a call to the Helpdesk.
- Solution — Only the solution is displayed for violations, allowing the end user to perform self-service remediation without knowing what the violation is. This configuration may be appropriate for scenarios where the user population on the network does not possess technical IT knowledge but is expected to self-remediate.
- Description and Solution — Both the description and solution are displayed for violations. This provides the end user with information concerning what violation was found and how to fix it. Providing complete information concerning the violation gives the end user the best chance of self-remediation, however, the technical details of the violation may result in end user confusion. Therefore, this configuration may be appropriate for scenarios where the user population of the network possesses more technical IT knowledge.
- Do Not Allow Rescan
- Select this checkbox if you do not want the end-user to have the ability to initiate a rescan of their end-system when quarantined. When selected, the Reattempt Network Access button is removed from the Assessment/Remediation web page, and the user is not provided with any way to initiate a rescan on-demand for network access. The end user is forced to contact the Help Desk for assistance. You can edit the "Permanently Removed Message" which, by default, advises the end user to contact the Helpdesk to obtain access to the network. Note that the default configuration of the "Permanently Removed Message" references the "HELPDESK_INFO" variable which represents the Helpdesk Information that is defined in the Look and Feel Settings.
- Allow Blacklist Remediation
- Select this checkbox if you want black-listed end users to have the ability to remediate their problem and attempt to reconnect to the network. When selected, a "Reattempt Network Access" button is added to the Blacklist web page, allowing end users to remove themselves from the blacklist and reauthenticate to the network.
- Permanently Removed Message
- Click the Edit button to open a window where you can modify the message displayed when users can no longer self-remediate and must contact the Help Desk for assistance. Note that the default message references the "HELPDESK_INFO" variable which represents the Helpdesk Information that is defined in the Look and Feel Settings.
- Custom Agent Install Message
- Click the Edit button to open a window where you can create a message containing additional agent install information to add to the default text on the Install Agent portal web page.
- Access Denied Image
- Select the image you want displayed when the end user is quarantined and denied access to the network. The drop-down menu displays all the images defined in the Images window for your selection.
- Image During Reattempt
- Select the image you want displayed when the end-user is reattempting network access after they repair their system. The drop-down menu displays all the images defined in the Images window for your selection.
- Agent Scan in Progress Image
- Select the progress bar image you want displayed while the end-user is being scanned. The drop-down menu displays all the images defined in the Images window for your selection.
- Redirection
- There are four Redirection options that specify where the end-user is
redirected following successful remediation, when the end-user
is allowed on the network. The option selected here overrides the Redirection option specified in the Network Settings
for Remediation only.
- Use Network Settings Redirection — Use the Redirection option specified in the Network Settings.
- Disabled — This option disables redirection. The end-user stays on the same web page where they were accepted onto the network.
- To User's Requested URL — This option redirects the end user to the web page they originally requested when they connected to the network.
- To URL — This option lets you specify the URL of the web page to which the end-user is redirected. This is typically the home page for the enterprise website, for example, "http://www.ExtremeNetworks.com."
Remediation Attempt Limits
- Limit Remediation Attempts
- Select this checkbox to limit the maximum number of times an end-user is allowed to initiate a rescan of their end-system after initially being quarantined, in an attempt to remediate their violations. If selected, enter the number of attempts allowed.
- Limit Time for Remediation
- Select this checkbox to limit the total interval of time an end user is allowed to initiate a rescan of their end-system after initially being quarantined, in an attempt to remediate their violations. If selected, enter the amount of time in minutes.
Remediation Links
This table lists the links displayed on the Assessment/Remediation web page for the end users to use to remediate their end-system violations. There are two default remediation links: Microsoft Support and MAC OS Support. Use this tab to add additional links such as an internal website for patches. Links must contain a valid protocol prefix (http://, https://, ftp://).
Click Add to open a window where you can define a new link's name and URL. Select a link and click Edit to edit the link's information. Click Delete to remove a URL from the table.
Custom Remediation Actions
Use this table to create your own custom remediation action for a particular violation to use in place of the remediation action provided by the assessment server.
Use the following steps to add a custom remediation action:
- Click the Add button to open the Add Custom Remediation Action window.
- Enter the Test Case ID for the particular violation being remediated by the custom action. Test Case ID is found in the Health Results Details subtab in the End-Systems tab.
- Add a custom description of the violation (required) and an optional custom solution.
- If you have multiple portal configurations and you want to use this custom remediation action in all of your configurations, select the Add to All Portal Configurations option. This option overwrites any existing custom actions defined for the test case ID.
- Click OK. Whenever the test case ID is listed as a violation on the web page, the custom violation description and solution you define is displayed instead of the remediation actions provided by the assessment server.
Select the Define Default Custom Action checkbox to advise end-users to contact the Helpdesk regarding additional security violations not explicitly listed with custom remediation actions. If this checkbox is selected, only the violations and associated custom remediation actions listed in the table would be presented to the user, along with a message advising them to contact the Helpdesk for any other security violations not explicitly configured with a custom remediation action. Click the Edit button to edit this message.
To copy a custom action to another portal configuration, select the action in the table and click the Copy To button. A window opens where you can select the portal configurations where you want to copy the action, and whether you want it to overwrite any existing custom remediation actions already defined for that test case ID.
Portal Web Page URLs
The following table provides a list of URLs for accessing commonly used portal web pages. You can also access these web pages using the Engine Portal Pages button at the bottom of the Portal Configuration window.
| Web Page | URL |
|---|---|
| Preview Web Page
Allows you to preview the web pages that may be accessed by the end user during the assessment/remediation and registration process. |
https://Access ControlengineIP/screen_preview |
| Registration Administration Page
Lets administrators view registered devices and users, and manually add, delete, and modify users. |
https://Access ControlengineIP/administration |
| Registration Sponsor Page
Lets sponsors view registered devices and users, and manually add, delete, and modify users. |
https://Access ControlengineIP/sponsor |
| Pre-Registration Page
The pre-registration web page lets selected personnel easily register guest users in advance of an event, and print out a registration voucher that provides the guest user with their appropriate registration credentials. |
https://Access ControlengineIP/pre_registration |
| Self-Registration Page
Allows an authenticated and registered user to self-register additional devices that may not have a web browser (for example, game systems). |
https://Access ControlengineIP/self_registration |
For information on related help topics: