The Port Properties Anti-Spoofing tab lets you enable or disable the anti-spoofing feature on the selected port, if the device supports it.
There are two ways to access the Anti-Spoofing tab:
- Select a device in the left-panel Network Elements tab. In the right-panel Ports tab, select a port and click the Port Properties button. In the Port Properties window, select the Anti-Spoofing tab (in the top row of tabs).
- Select a port in the left-panel Port Groups tab, then select the Anti-Spoofing tab in the right panel.
In order for Anti-Spoofing to take effect on a port, it must be enabled at the device level. You can do this using the device Anti-Spoofing tab.
The Port Properties Anti-Spoofing tab provides two sub-tabs:
Configuration Tab
This tab lets you enable/disable the different anti-spoofing methods on the port as well as view the anti-spoofing status on the device. If the device does not support anti-spoofing, these options are grayed out.
Click the graphic for more information.
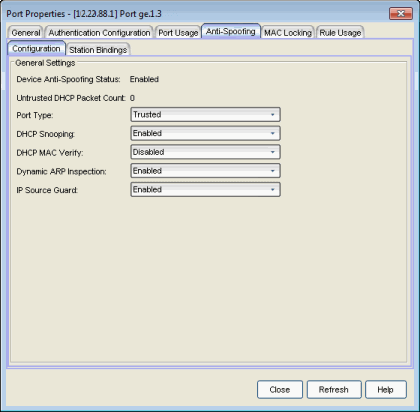
Shows whether the anti-spoofing feature is enabled or disabled the device. In order for anti-spoofing to take effect on a port, it must be enabled at the device level. You can do this using the device Anti-Spoofing tab.
The number of DHCP server packets received on this port. This counter will only increment when the Port Type is set to untrusted.
The DHCP snooping port type determine anti-spoofing behavior:
Trusted – DHCP server traffic is accepted and used to create bindings in the MAC-to-IP address binding table. Typically, only a port that is connected to a DHCP server would be set to trusted.
Bypass – Snooping of DHCP server traffic does not take place on the port. Typically, uplink ports out to the network would be set to bypass, as traffic would not be originating from that port.
Untrusted – The untrusted server counter is incremented when DHCP server traffic (DHCP ACK) is detected on the port, and the packets are dropped. DHCP RELEASE and DECLINE messages, sent by a client to free its IP address for use by another, are dropped if they are for a MAC address in the binding table that is on another port. If DHCP MAC Verify is enabled and the source MAC address does not match the Client Host Address in the DHCP payload (CHADDR), the packets are dropped. Typically, all edge ports with users would be set to untrusted.
Whether DHCP Snooping is enabled or disabled on the port.
Whether DHCP MAC Verify is enabled or disabled on the port.
Whether Dynamic ARP Inspection is enabled or disabled on the port. When set to inspection only, Dynamic ARP inspection will occur, but will not be used to create bindings.
Whether IP Source Guard is enabled or disabled on the port. When set to inspection only, IP Source Guard will occur, but will not be used to create bindings.
Station Bindings Tab
This tab presents a table that displays the current active bindings for the port set up through anti-spoofing. These bindings are the valid MAC/IP/Port associations detected on trusted ports from the various anti-spoofing methods such as DHCP snooping. This tab also provides the ability to reset violation counters and clear bindings from the table. You must click the Retrieve button to display the bindings information.
Click the graphic for more information.
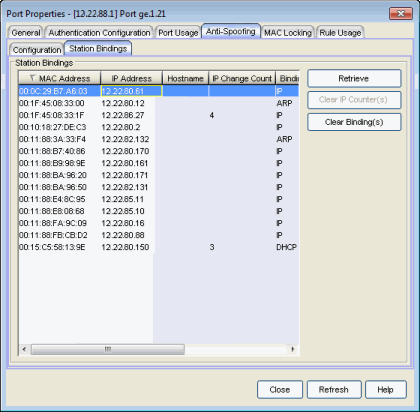
The MAC address of the binding.
The IP address of the binding.
An administratively-assigned hostname for the device.
The number of times the IP address has changed for this binding.
Indicates which binding type (DHCP, ARP, or IP inspection) was used to create the entry.
Duration (sec)
The amount of time, in seconds, that this binding has been operational for.
Lease Time (sec)
The amount of time, in seconds, that this binding will be operational before being destroyed. A value of zero (0) indicates that this binding will not expire.
Retrieves the bindings for the device.
Resets the IP Change Count to zero for the binding.
Removes the binding from the table.
For information on related tasks: