The Port Properties Authentication Configuration tab allows you to configure and change the authentication settings for a port. Authentication must be configured and enabled on the device in order for individual port authentication settings to take effect. Only those areas of the tab that relate to the authentication type configured on the device are available for editing.
There are two ways to access the Authentication Configuration tab:
- Select a device in the left-panel Network Elements tab. In the right-panel Ports tab, select a port and click the Port Properties button. In the Port Properties window, select the Authentication Configuration tab (in the top row of tabs).
- Select a port in the left-panel Port Groups tab, then select the Authentication Configuration tab in the right panel.
The Authentication Configuration tab has six sub-tabs:
- General Tab
- RFC3580 VLAN Authorization Tab
- Login Settings Tab
- Automatic Re-Authentication Tab
- Authenticated User Counts Tab
- CEP Access Tab
General Tab
This tab displays general authentication and port mode information about the port.
Click the graphic for more information.
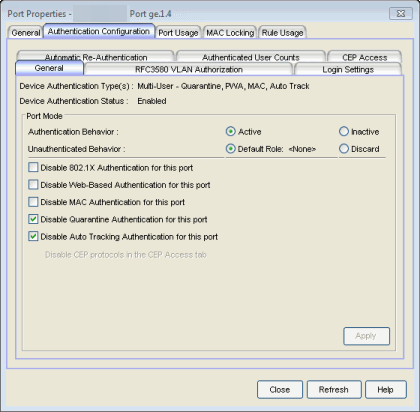
- Device Authentication Type(s)
- Authentication type(s) configured on the device (Quarantine, 802.1X, Web-Based, MAC, Auto Track, or None). Some devices support multiple authentication types and multiple users (Multi-User authentication) per port, while others are restricted to only one or two authentication types and single users per port (Single User authentication). If the value is None, all types of authentication are disabled at the device level, and port authentication settings cannot be configured and will not take effect.
- Device Authentication Status
- Indicates whether or not the authentication type(s) configured on the device are enabled or not. If multiple authentication types are configured on the device, this status applies to all authentication types. If authentication is disabled at the device level, port authentication settings will not take effect.
Port Mode
This area displays the current port mode for the port, and allows you to change the settings if desired. Port mode defines whether or not a user is required to authenticate on a port, and how unauthenticated traffic will be handled. It is a combination of Authentication Behavior (whether or not authentication is enabled on the port), and Unauthenticated Behavior (whether unauthenticated traffic will be assigned to the port's default role or discarded). See Port Mode for a complete description of each port mode.
In addition, this section provides checkboxes that allow you to disable a specific authentication type at the port level.
- Authentication Behavior
- Select an option to specify whether or not authentication is enabled on
the port. (See Port Mode for more information.) If
you set the port's Authentication Behavior to Active (i.e., you enable
authentication for the port), it is recommended that you enable the Drop
VLAN Tagged Frames feature.
NOTE: Authentication Behavior must be set to Active for authentication to be allowed using CEP Protocols.
- Unauthenticated Behavior
- Select an option to specify whether unauthenticated traffic will be assigned to the port's default role or discarded. The current default role for the port is shown. For additional information, see Port Mode.
-
NOTE: For Single User 802.1X and 802.1X+MAC authentication types:
-- Active/Default Role mode requires that a default role be set on the port.
-- Active/Discard mode requires that any default role set on the port is cleared.
For Multi-User Web-based authentication:
-- Active/Discard mode is not supported.
- Disable 802.1X Authentication for this port
- Select this checkbox to disable 802.1X authentication at the port level. If the device is only configured with 802.1X
authentication, selecting this checkbox will result in the port
Authentication Behavior being set to Inactive.
NOTE: For Single User 802.1X+MAC authentication with Active/Default Role as the selected port mode: Disabling 802.1X authentication also disables MAC authentication on the port. An end user connecting to the port will not be able to authenticate via 802.1X or MAC. The port will behave as if Inactive/Default Role is the selected port mode.
- Disable Web-Based Authentication for this port
- Select this checkbox to disable web-based authentication at the port level. If the device is only configured with web-based authentication, selecting this checkbox will result in the port Authentication Behavior being set to Inactive.
-
NOTE: For Multi-User Web-Based authentication with Active/Discard as the selected port mode: This checkbox is automatically selected because multi-user web-based authentication does not support the Active/Discard port mode.
- Disable MAC Authentication for this port
- Select this checkbox to disable MAC authentication at the port level. If the device is only configured with MAC authentication, selecting this checkbox will result in the port Authentication Behavior being set to Inactive.
- Disable CEP protocols in the CEP Access tab
- Use the CEP Access tab to disable CEP protocols at the port level.
- Disable Quarantine Authentication for this port
- Select this checkbox to disable Quarantine authentication at the port level. If the device is only configured with Quarantine authentication, selecting this checkbox will result in the port Authentication Behavior being set to Inactive.
- Disable Auto Tracking Authentication for this port
- Select this checkbox to disable MAC authentication at the port level. If the device is only configured with Auto Tracking authentication, selecting this checkbox will result in the port Authentication Behavior being set to Inactive.
RFC3580 VLAN Authorization Tab
This tab lets you enable or disable RFC 3580 VLAN Authorization on the port and specify an egress state. RFC 3580 VLAN Authorization must be enabled in networks where the RADIUS server has been configured to return a VLAN ID when a user authenticates. When RFC 3580 VLAN Authorization is enabled:
- ports on devices that do not support policy, will tag packets with the VLAN ID.
- ports on devices that do support policy and also support Authentication-Based VLAN to Role Mapping, will classify packets according to the role that the VLAN ID maps to.
You can also enable and disable VLAN Authorization at the device level using the device Authentication tab. If the device does not support RFC 3580, this tab will be grayed out.
Click the graphic for more information.
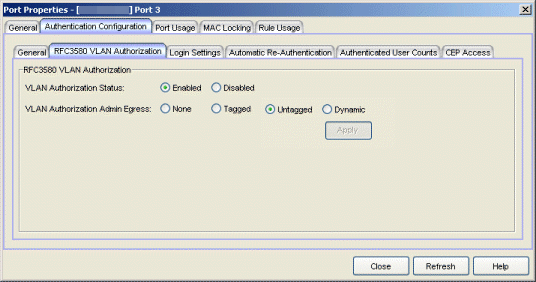
- VLAN Authorization Status
- Allows you to enable and disable RFC 3580 VLAN Authorization for the selected port. This option is grayed out if not supported by the device.
- VLAN Authorization Admin Egress
- Allows you to modify the VLAN egress list for the VLAN ID returned
by the RADIUS server when a user authenticates on the port:
- None - No modification to the VLAN egress list will be made.
- Tagged - The port will be added to the list with the egress state set to Tagged (frames will be forwarded as tagged).
- Untagged - The port will be added to the list with the egress state set to Untagged (frames will be forwarded as untagged).
- Dynamic - The port will use information returned in the RADIUS response to modify the VLAN egress list. This value is supported only if the device supports a mechanism through which the egress state may be returned in the RADIUS response.
- The current egress settings for the port are displayed in the VLAN Oper Egress column in the End User Sessions table on the Port Usage tabs. These options are grayed out if not supported by the device.
Login Settings Tab
This tab displays the current login settings for the port and allows you to change the settings if desired. The options available depend on what type(s) of authentication are enabled on the device.
Click the graphic for more information.
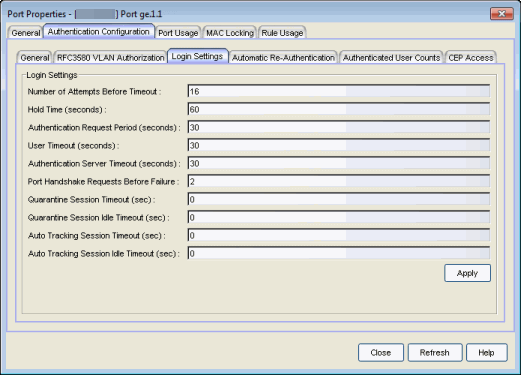
- Number of Attempts Before Timeout
- Number of times a user can attempt to log in before authentication fails and login attempts are not allowed. For web-based authentication, valid values are 1-2147483647, zero is not allowed, and the default is 2. For 802.1X and MAC authentication, this value is permanently set to 1.
- Hold Time (seconds)
- Amount of time (in seconds) authentication will remain timed out after the specified Number of Attempts Before Timeout has been reached. Valid values are 0-65535. The default is 60. (Hold Time is also known as Quiet Period in web-based and MAC authentication.)
- Authentication Request Period
- For 802.1X authentication, how often (in seconds) the device queries the port to see if there is a new user on it. If a user is found, the device then attempts to authenticate the user. Valid values are 1-65535. The default is 30.
- User Timeout
- For 802.1X authentication, the amount of time (in seconds) the device waits for an answer when querying the port for the existence of a user. Valid values are 1-300. The default is 30.
- Authentication Server Timeout
- For 802.1X authentication, if a user is found on the port, the amount of time (in seconds) the device waits for a response from the authentication server before timing out. Valid values are 1-300. The default is 30.
- Port Handshake Requests Before Failure
- For 802.1X authentication, the number of times the device tries to finalize the authentication process with the user, before the authentication request is considered invalid and authentication fails. Valid values are 1-10. The default is 2.
Quarantine Session Timeout (sec)
For Quarantine authentication, the maximum number of seconds an authenticated session may last before automatic termination of the session. A value of zero indicates that no session timeout will be applied.
Quarantine Session Idle Timeout (sec)
For Quarantine authentication, the maximum number of consecutive seconds an authenticated session may be idle before automatic termination of the session. A value of zero indicates that the device level setting is used.
Auto Tracking Session Timeout (sec)
For Auto Tracking sessions, the maximum number of seconds a session may last before automatic termination of the session. A value of zero indicates that the device level setting is used.
Auto Tracking Session Idle Timeout (sec)
For Auto Tracking sessions, the maximum number of consecutive seconds a session may be idle before automatic termination of the session. A value of zero indicates that the device level setting is used.
Automatic Re-Authentication Tab
This tab is grayed-out if only web-based authentication is enabled on the device. For 802.1X and MAC authentication, the Automatic Re-Authentication tab lets you set up the periodic automatic re-authentication of logged-in users on this port. Without disrupting the user's session, the device repeats the authentication process using the most recently obtained user login information, to see if the same user is still logged in. Authenticated logged-in users are not required to log in again for re-authentication, as this occurs "behind the scenes."
Click the graphic for more information.
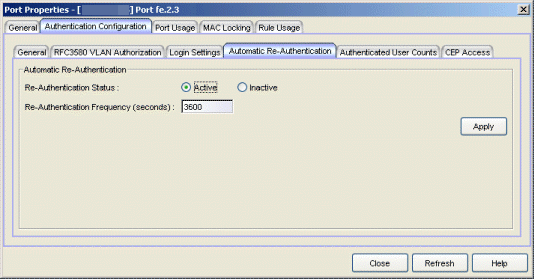
- Re-Authentication Status
- If Active is selected, the re-authentication feature is enabled. If Inactive is selected, the re-authentication feature is disabled.
- Re-Authentication Frequency
- How often (in seconds) the device checks the port to re-authenticate the logged in user. Valid values are 1-2147483647. The default is 3600.
Authenticated User Counts Tab
This tab provides authenticated user count information for devices with Multi-User as their configured authentication type. See the device Authentication tab for information on setting the device authentication type.
Click the graphic for more information.
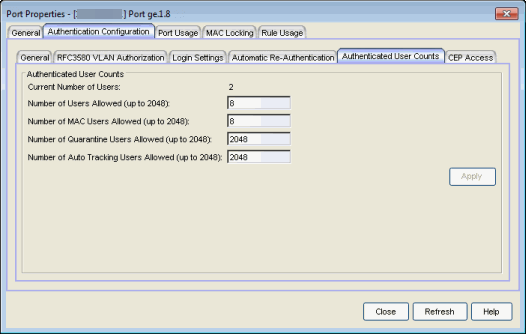
- Current Number of Users
- The current number of users that are actively authenticated or have authentications in progress on this interface. If multi-user authentication is disabled, this number will be 0 (zero). Any unauthenticated traffic on the port is not included in this count.
- Number of Users Allowed (up to 2048)
- The number of users that can be actively authenticated or have authentications
in progress at one time on this interface. If you set this value below the current number of users,
end user sessions exceeding that number will be terminated.
NOTE: B2/C2 Devices. If you are configuring a single user and an IP phone per port, set this value to 2.
- Number of MAC Users Allowed (up to 2048)
- The number of users that can be actively authenticated via MAC authentication, or have MAC authentications in progress at one time on this interface. The number of MAC users allowed cannot exceed the number of users allowed. If you set this value below the current number of users, end user sessions exceeding that number will be terminated. If MAC is not selected as a Multi-User authentication type on the device Authentication tab, this field will be grayed out.
Number of Quarantine Users Allowed (up to 2048)
The number of users that can be actively authenticated via Quarantine authentication, or have Quarantine authentications in progress at one time on this interface. The number of Quarantine users allowed cannot exceed the number of users allowed. If you set this value below the current number of users, end user sessions exceeding that number will be terminated. If Quarantine Auth is not enabled on the device Authentication tab, this field will be grayed out.
Number of Auto Tracking Users Allowed (up to 2048)
The number of Auto Tracking users that can be actively authenticated or have authentications in progress at one time on this interface. The number of Auto Tracking users allowed cannot exceed the number of users allowed. If you set this value below the current number of users, end user sessions exceeding that number will be terminated. If Auto Tracking is not enabled on the device Authentication tab, this field will be grayed out.
CEP Access Tab
This tab lists all the CEP (Convergence End Point) protocols supported by the device that the port resides on, and lets you enable or disable them for that port. For devices that do not support CEP, the tab will be blank.
| NOTE: | Port Mode Authentication Behavior must be set to Active (on the General sub-tab) for authentication to be allowed using these CEP Protocols. |
|---|
You can enable CEP protocols for multiple ports using the Port Configuration Wizard. In addition to enabling protocols on the port, you must also configure CEP for the device the port resides on. You can configure CEP for a single device using the device Authentication tab (CEP sub-tab) or for multiple devices using the Device Configuration Wizard.
Click the graphic for more information.
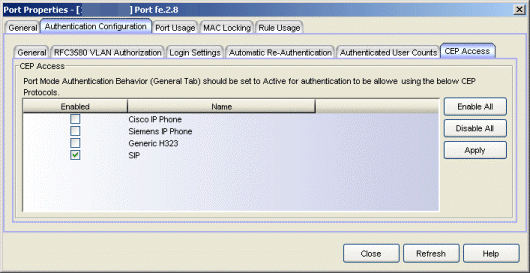
- CEP Access
- Lists all the CEP protocols supported by the device that the port resides on. Use the checkboxes to enable or disable CEP protocols on this port. If the device does not support the CEP feature, this area is blank.
For information on related tasks:
For information on related tabs: