The Port Properties General tab provides general information about the selected port, and also lets you view and change various port configuration settings.
There are two ways to access the General tab:
- Select a device in the left-panel Network Elements tab. In the right-panel Ports tab, select a port and click the Port Properties button. In the Port Properties window, select the General tab (in the top row of tabs).
- Select a port in the left-panel Port Groups tab, then select the General tab in the right panel.
The General tab has four sub-tabs:
General Tab
This tab displays general information about the port and indicates whether it is a frozen port or if TCI Overwrite is enabled on the port.
Click the graphic for more information.

General
- Name
- Name of the port, constructed of the name or IP address of the device and either the port index number or the port interface name.
- Port Type
- Type of port. Possible values include: Access, Interswitch Backplane, Backplane, Interswitch, and Logical.
- Port Speed
- Speed of the port. Possible values include: 10/100, speed in megabits per second (for example, 800.0 Mbps), Unknown (displayed for logical ports).
- Frozen (Prevents Port Modifications)
- Enables you to freeze (check) the port or clear (uncheck) the frozen status on the port. Freezing a port "locks" it so that no one can accidentally reconfigure sensitive attributes such as port authentication or default role settings, or terminate sessions that are authenticated on the port. See How to Freeze/Unfreeze a Port for more information.
- Egress Policy
- Enable or disable Egress Policy for the port. (This option will be grayed out if the device on which the port is located does not support egress policy.) Egress policy can be used in scenarios where policy may not be in force at the user edge throughout the entire network. For example, a policy can be created that prevents users from running unauthorized Apache web servers. If an end user has an Apache server running on their end-system (where policy is in use), an egress policy could prevent another end-system (where policy is not in use) from accessing that end-system as an HTTP server, by dropping HTTP queries destined to that end user. Egress policy works in conjunction with the ingress policy configured for the port, in that the same ingress policy rules will be applied to the traffic egressing the port, with the exception of rules that specify a source or destination address. In this case, the ingress rules will still be used, but the direction of the rule will be inverted on egress. For example, an ingress MAC Address Source rule will match the destination MAC address of the frame on egress. If you enable egress policy, you must also enable TCI Overwrite.
- TCI Overwrite
- Enable or disable TCI Overwrite functionality for the port. (This option will be grayed out if the device on which the port is located does not support TCI Overwrite.) Enabling TCI Overwrite causes the VLAN or class of service tag in a received packet to be overwritten by the VLAN (access control) and class of service characteristics defined in the port's current or default role. If there is no role assigned to the port, the port uses any static classification rules which exist. If there are no static rules, the port uses the PVID and default class of service for the port. TCI Overwrite is required for some devices for Tagged Packet VLAN to Role Mapping, and can be enabled either here on a per-port basis, or for an individual role in the role's General tab, as well as on a per-rule basis in the Rule General Tab.
- Description
- Use the Edit button to add or change a description of the port. For example, you could use the description field to explain why a port is frozen. This description can then be viewed as a tooltip when you hover over the port nodes in the tree (when under a port group) as well as in the right-panel Ports and Details View tabs.
Role Config
This section displays the default role on the port, and lets you select a new default role, as well as a RADIUS Timeout role and RADIUS Reject role for the port. These options allow you to specify a different policy role for each possible outcome of the authentication process.
Click on the gear icon ![]() to open a window where you can select the role.
to open a window where you can select the role.
| NOTE: |
The RADIUS Timeout Role and RADIUS Reject Role features require that auto-tracking authentication be enabled at the device and port level in order to be operational. |
- Default Role
- Select a role to assign as the port's default role. The default role is the role assigned to the port if no other role has been authenticated on it. If the port was not assigned a role when the end user logged in (authenticated), or if authentication is disabled on a port, then the port's default role will take effect. If you set a default role for the port, it is recommended that you enable the Drop VLAN Tagged Frames feature. See Default Role in the Concepts topic for information on default roles. For additional information, see Port Mode.
- RADIUS Timeout Role
- Select the role to assign to the port if it encounters a RADIUS timeout. This allows you to assign a different role to end-systems that have not been provisioned on the network or that try to authenticate during a RADIUS outage. It also allows a different role to be assigned when RADIUS timeouts occur during re-authentication of multi-authentication sessions. This would allow user sessions to remain authenticated and provisioned when all RADIUS servers become unreachable due to an unexpected network outage.
- RADIUS Reject Role
- Select the role to assign to the port if it encounters a RADIUS reject. This can be used in scenarios where the Default role for a port provides lenient access privileges. If the port receives a RADIUS reject, then a RADIUS Reject role with limited or no access privileges would be assigned to the port to restrict the end user.
Mappings Tab
This tab allows you to create port-level MAC or IP to Role mappings and Tagged Packet VLAN to Role mappings. A mapping does not have to exist at the device level to be created at the port level, and port-level mappings will override any device-level mappings. Any additions or changes you make to this tab must be enforced in order to take effect.
| NOTES: | You must have the Port Level Role Mappings feature enabled in Policy Manager
for the mappings to take effect. (From the menu bar, select the Edit > Port
Level Role Mappings checkbox.) If the feature is not enabled, the mappings will
be ignored and any mappings listed here will be grayed out.
Port-level mappings cannot be added or removed to or from frozen ports |
|---|
| WARNING: | Enforcing port-level MAC or IP to Role mappings could potentially remove rules
created by NetSight Automated Security Manager (ASM) as an intrusion detection response. |
|---|
Click the graphic for more information.

MAC/IP to Role Mapping
MAC or IP to Role mapping provides a way to assign a role to an end station based on its MAC or IP address. In this section, you can create a list of MAC or IP addresses and map each of them to a specific role. If the listed mappings are grayed out, it means that the Port Level Role Mappings feature is not enabled (Edit > Port Level Role Mappings).
- MAC/IP Address
- The MAC or IP addresses that are mapped to a role. Click Add to add a mapping to the list.
- Remove Button
- Select a MAC or IP address and click Remove to remove the address from the mapping list.
Tagged Packet VLAN to Role Mapping
Tagged Packet VLAN to Role Mapping provides a way to assign a role to network traffic, based on a VLAN ID. In this section, you can create a list of VLANs and map each of them to a specific role. If the listed mappings are grayed out, it means that the Port Level Role Mappings feature is not enabled (Edit > Port Level Role Mappings). For more information, see VLAN to Role Mapping in the Concepts Help topic.
| NOTES: | TCI Overwrite Requirement
Tagged Packet VLAN to Role Mapping will apply the Role definition to incoming packets using a mapped VLAN. This definition will apply a CoS and determine if the packet is discarded or permitted, and if TCI Overwrite is enabled will re-specify the VLAN ID defined by the Rule / Role Default. If TCI Overwrite is disabled, the packet will egress (if permitted by the Rule Hit) with the original VLAN ID it ingressed with. If supported by the device, you can enable TCI Overwrite on a per-port basis in the Port Properties window General tab, or for an individual role in the role's General tab. The stackable devices support rewriting the CoS values but not the VLAN ID. |
|---|
- VLAN
- The VLANs (VLAN ID and name) that are mapped to a role. Click Add to add a mapping to the list.
- Add Button
- Opens the VLAN to Role Mapping Selection View, where you can select a VLAN and map it to a role.
Drop VLAN Tagged Frames Tab
This tab lets you enable or disable the Drop VLAN Tagged Frames feature on this port. When the Drop VLAN Tagged Frames feature is enabled, any packet already tagged with a VLAN coming into the port will be dropped. This provides extra security in that it prevents users from, for example, coming in with a card capable of VLAN tagging and attempting to access the network. In most cases, you would enable this feature on user ports because you don't want users to be tagging their own traffic, and you would disable it on interswitch link ports, where you want tagged packets to be accepted.
It is recommended that you enable the Drop VLAN Tagged Frames feature when you set a default role on a port or when you enable authentication on a port, because these things indicate that the port is a user port that should not be transmitting tagged packets. You can enable Drop VLAN Tagged Frames for a single port here, or on multiple ports simultaneously using the Port Configuration Wizard. If the device does not support Drop VLAN Tagged Frames, this tab is grayed out.
| WARNING: | Enabling this feature on an Interswitch or Backplane
port is likely to result in loss of contact with devices connected through the port. |
|---|

Disabled Traffic Classification Types Tab
Use this tab to specify rule types that will be disabled on the port. You can disable specific classification rule types on an individual port as a way to disable policy-assignment rules used in VLAN to Role Mapping, IP to Role Mapping, MAC to Role Mapping, and Role Override. For example, you can disable the VLAN ID traffic classification type to disable Tagged Packet VLAN to Role Mapping on the port. You can also disable all traffic classification types, which effectively turns off policy on the port.
Click the graphic for more information.
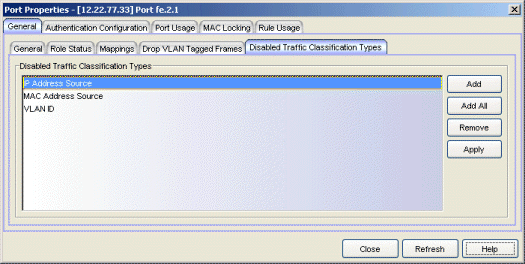
Use the Add or Add All button to create a list of rule types that will be disabled on the port.
- Add Button
- Opens the Traffic Classification Type wizard where you can select the traffic classification type you want to disable on the port and add it to the list.
- Add All Button
- Adds all traffic classification types to the list. This would disable all traffic classification on the port, and the role's default class of service and/or default access control would take effect.
For information on related concepts:
For information on related tasks:
For information on related windows: