Traffic Classification rules allow you to assign VLAN membership and/or class of service to your network traffic based on the traffic's classification type. Classification types are derived from Layers 2, 3, 4, and 7 of the OSI model, and all network traffic can be classified according to specific layer 2/3/4/7 information contained in each frame. In Policy Manager, rules are used to provide four key policy features: traffic containment, traffic filtering, traffic security, and traffic prioritization. Examples of how to design rules for each of these features are given below.
A Traffic Classification rule has two main parts: Traffic Description and Actions. The Traffic Description identifies the traffic classification type for the rule. The Actions specify whether traffic matching that classification type will be assigned VLAN membership, class of service, or both. When a frame arrives on a port, the switch checks to see if the frame's classification type matches the type specified in a rule. If it does, then the actions defined in that rule will apply to the frame. Use the Policy Manager's Rule Wizard to quickly and easily create a rule and define its traffic description and actions.
In Policy Manager, rules are created and then grouped together into Services, which are then used to define roles. A role is assigned to each port either through end user authentication or as the port's default role. This means that there can be multiple rules active on a port. When a frame is received on a port, if the frame's classification type matches more than one rule, classification precedence rules are used to determine which rule to use.
The following information is discussed in this file:
- Traffic Descriptions
- Actions
- Classification Types and their Parameters
- Layer 2 Data Link Classification Types
- Layer 3 Network Classification Types
- Layer 4 Application Transport Classification Types
- Layer 7 Application Classification Type
- Examples of How Rules are Used
- Classification Rules Precedence
Traffic Descriptions
When you create a Traffic Classification rule in Policy Manager, you must define the rule's traffic description. The traffic description identifies the traffic classification type for that rule. You must select a classification type, and then select or enter certain parameters or values for each type.
Classification types are grouped according to Layers 2, 3, 4, and 7 of the OSI model and there are multiple classification types for each layer.
| OSI Model |
|---|
| Layer 7 - Application |
| Layer 6 - Presentation |
| Layer 5 - Session |
| Layer 4 - Transport |
| Layer 3 - Network |
| Layer 2 - Data Link |
| Layer 1 - Physical |
Specific Layer 2/3/4/7 information contained in each frame is used to identify the frame's classification type. Each layer uses different information to classify frames.
- Layer 2 Data Link -- classifies frames based on an exact match of the MAC address or specific protocol type of each frame.
- Layer 3 Network -- classifies IP or IPX frames based on specific information contained within the Layer 3 header.
- Layer 4 Transport -- classifies IP frames based on specific Layer 4 TCP or UDP port numbers contained in the header.
- Layer 7 Application -- classifies frames based on specific Layer 7 application types.
For a complete description of Layer 2, 3, 4, and 7 classifications, refer to Classification Types and Their Parameters.
Actions
When you create a Traffic Classification rule in Policy Manager, you must define the actions that the rule will perform. When a frame arrives on a port, the switch checks to see if the frame's classification type matches the type specified in a rule. If it does, then the actions defined in that rule will apply to the frame. Actions specify whether the frame will be assigned VLAN membership (access control) and/or priority (class of service).
VLAN Membership (Access Control)
In your network domains, you can create VLANs (Virtual Local Area Networks) that allow end-systems connected to separate ports to send and receive traffic as though they were all connected to the same network segment. Using traffic classification rules, you can classify a frame based on the frame's classification type to have membership in a specific VLAN, providing important traffic containment, filtering, and security for your network.
For example, a network administrator could use rules to separate end user traffic into VLANs according to protocol, subnet, or application. Rules could also be used to group geographically separate end-systems into job-specific workgroups.
Priority (Class of Service)
Traffic Classification rules allow you to assign a transmission priority to frames received on a port based on the frame's classification type. For example, a network administrator could use rules to assign priority to one network application over another.
Priority is a value between 0 and 7 assigned to each frame as it is received on a port, with 7 being the highest priority. Frames assigned a higher priority will be transmitted before frames with a lower priority. Each of the priorities is mapped into a specific transmit queue by the switch or router. The insertion of the priority value (0-7) allows all 802.1Q devices in the network to make intelligent forwarding decisions based on its own level of support for prioritization.
Policy Manager enables you to utilize priority by creating classes of service that each include an 802.1p priority, and optionally an IP type of service (ToS/DSCP) value, rate limits, and transmit queue configuration. You can then assign the class of service as a classification rule action, as part of the definition of an automated service, or as a role default. See Getting Started with Class of Service for more information.
Classification Types and their Parameters
When you define a rule's traffic description, you select a classification type, and then select or enter certain parameters or values for each type. Classification types are grouped according to Layers 2, 3, 4, or 7 of the OSI model.
Layer 2 -- Data Link Classification Types
Layer 2 classification types allow you to define classification rules based on an exact match of the MAC address or specific protocol type of each frame.
- MAC Address Source, MAC Address Destination, MAC Address Bilateral
- These classification types are based on an exact match of the source, destination, or bilateral (either source or destination) MAC address contained in an Ethernet frame. Enter a valid MAC address or click Select to open a window where you can select a MAC address read from your network devices. You can specify a mask, however masking a MAC address is not supported on legacy devices.
- Ethertype
- This classification type is based on the specific protocol type of each frame defined in the
two-byte Ethertype field. Select an Ethertype from the list of
well-known values, or select Other and manually enter a
single value in hexadecimal form. You can enter a range of values,
however range rules are not supported on legacy devices or N-Series Gold.
| Well-known Ethertypes | Values |
|---|---|
| IP | 0x0800 |
| ARP | 0x0806 |
| Reverse ARP | 0x8035 |
| Novell IPX 1 | 0x8137 |
| Novell IPX 2 | 0x8138 |
| Banyan | 0x0bad |
| AppleTalk | 0x809b |
| AppleTalk ARP | 0x80f3 |
| IPv6 | 0x86dd |
| Decnet Phase 4 | 0x6003 |
- DSAP/SSAP
- This classification type is based on the specific protocol type of each frame defined in the
DSAP and SSAP fields. Select a protocol from the list of well-known
values, or select Other and manually
enter a custom two-byte value in hexadecimal format (0xFFFF). The LSB
of the DSAP address specifies Individual(0) or Group(1), while the
LSB of the SSAP address specifies Command(0) or Response(1). For the SNAP frame type, you may enter Advanced DSAP/SSAP configurations. The advanced fields are not supported on legacy devices and are ignored.
| Well-known DSAP/SSAP Types | Values |
|---|---|
| IP | 0x0606 |
| IPX | 0xe0e0 |
| NetBIOS | 0xf0f0 |
| Banyan Vines | 0xbcbc |
| SNA | 0x0404 |
| SNAP | 0xAAAA |
| Other | a two-byte value |
- VLAN ID
- This classification type is based on an exact match of the VLAN tag contained within a frame. Select a VLAN ID (VID) from the list of VLANs defined in Policy Manager. If you select Other, you must enter a single VID or specify a range of VIDs in decimal form. Range rules are not supported on legacy devices.
- Priority
- This classification type is based on an exact match of the Priority tag contained within a frame. Select a Priority value 0 - 7 from the list of well-known values, or select Other and enter a value in decimal form.
Layer 3 -- Network Classification Types
Layer 3 Network classification types allow you to define classification rules based on specific information contained within the Layer 3 header of an IP or IPX frame.
- IP Time to Live (TTL)
- This classification type is based on an exact match of the TTL field contained in the IP header of a frame. The TTL field indicates the maximum number of router hops the packet can make before being discarded. The TTL field is set by the packet sender and reduced by every router on the route to its destination. If the TTL field reaches zero before the packet arrives at its destination, then the packet is discarded. IP Time to Live rules are only supported on K-Series and S-Series devices.
- IPX Network Source, IPX Network Destination, IPX Network Bilateral
- These classification types are based on specific information contained within the Layer 3 header of an IPX frame. It is a four-byte user-defined value that represents the IPX source, destination, or bilateral (either source or destination) network number. This value must be a valid IPX network address in hexadecimal form. You can enter a range of values, however range rules are not supported on legacy devices or N-Series Gold.
- IPX Socket Source, IPX Socket Destination, IPX Socket Bilateral
- These classification types are based on specific information contained within the
Layer 3 header of an IPX frame. It is a two-byte, user-defined value
that represents the IPX source, destination, or bilateral (either
source or destination) socket numbers. This value is used by higher
layer protocols to target specific applications running among hosts.
Select an IPX Socket type from the list of well-known values, or select Other
and manually enter the value in decimal form. You can enter a range
of values, however range rules are not supported on legacy devices or N-Series Gold.
| Well-known IPX Socket Types | Values |
|---|---|
| NCP | 1105 |
| SAP | 1106 |
| RIP | 1107 |
| NetBIOS | 1109 |
| Diagnostics | 1110 |
| NSLP | 36865 |
| IPX Wan | 56868 |
| Other | 0-65535 |
- IPX Class of Service
- This classification type is based on specific information contained within the Layer 3 header of an IPX frame. This is a one-byte field used for transmission control (hop count) by IPX routers. Enter a valid IPX Class of Service in decimal form, 0-255. You can enter a range of values, however range rules are not supported on legacy devices or N-Series Gold.
- IPX Packet Type
- This classification type is based on specific information contained within the Layer 3 header of an IPX
frame. Select an IPX Packet type from the list of well-known values
or select Other and manually enter the value in decimal form.
You can enter a range of values, however range rules are not supported on legacy devices or N-Series Gold.
| Well-known IPX Packet Types | Values |
|---|---|
| Hello/SAP | 0 |
| RIP | 1 |
| Echo Packet | 2 |
| Error Packet | 3 |
| NetWare 386 | 4 |
| SeqPackProt | 5 |
| NetWare 286 | 17 |
| Other | 0-31 |
- IPv6 Address Source, IPv6 Address Destination, IPv6 Address Bilateral
- These classification types are based on an exact match of the source, destination, or bilateral (either source or destination) IPv6 address information contained within the IPv6 header of each frame. Enter a valid IPv6 address and optional mask ("/n") in the Value field.
- IPv6 Socket Source, IPv6 Socket Destination, IPv6 Socket Bilateral
-
These classification types are based on an exact match of a specific
source, destination, or bilateral (either source or destination) IPv6
address and a UDP/TCP port number (type) contained within the IPv6
header of each frame. Enter an IPv6 address in the Value field.
Then, select a UDP/TCP type from the list
of well-known values, or select Other and manually enter the value in
form. (UDP/TCP port numbers are defined in RFC 1700.) If you select Other, you can enter a range of values.
| TIP: | You can define a new value for a UDP or TCP port number using the Pre-Defined Well-Known IDs window. Once defined, it is available for selection from the list of well-known values when defining the rule's traffic classification type. |
| Well-known UDP/TCP Types | Values |
|---|---|
| FTP Data | 20 |
| FTP | 21 |
| SSH | 22 |
| Telnet | 23 |
| SMTP | 25 |
| TACACS | 49 |
| DNS | 53 |
| BootP Server | 67 |
| BootP Client | 68 |
| TFTP | 69 |
| Finger | 79 |
| HTTP | 80 |
| POP3 | 110 |
| Portmapper | 111 |
| NNTP | 119 |
| NTP | 123 |
| NetBIOS Name Service | 137 |
| NetBIOS Datagram Service | 138 |
| NetBIOS Session Service | 139 |
| IMAP2/IMAP4 | 143 |
| SNMP | 161 |
| IMAP3 | 220 |
| LDAP | 389 |
| HTTPS | 443 |
| R-Exec | 512 |
| R-Login | 513 |
| R-Shell | 514 |
| LPR | 515 |
| RIP | 520 |
| SOCKS | 1080 |
| Citrix ICA | 1494 |
| RADIUS | 1812 |
| RADIUS Accounting | 1813 |
| NFS | 2049 |
| X11 (Range Start) | 6000 |
| X11 (Range End) | 6063 |
| Other | 0-65535 |
- IPv6 Flow Label
- These classification types are based on the exact match of the value in the 20-bit Flow Label field in the IPv6 header. This field is used to identify packets belonging to particular traffic flow that needs special traffic handling. Enter a flow label value and sigbits mask.
- IP Address Source, IP Address Destination, IP Address Bilateral
- These classification types are based on an exact match of the source, destination, or bilateral (either source or destination) IP address information contained within the IP header of each frame. Enter a valid IP address and optional mask ("/n") in the Value field.
- IP Socket Source, IP Socket Destination, IP Socket Bilateral
-
These classification types are based on an exact match of a specific
source, destination, or bilateral (either source or destination) IP
address and a UDP/TCP port number (type) contained within the IP
header of each frame. Enter an IP address in the Value field.
Then, select a UDP/TCP type from the list
of well-known values, or select Other and manually enter the value in decimal form.
(UDP/TCP port numbers are defined in RFC
1700.) If you select Other, you can enter a range of values,
however range rules are not supported on legacy devices or N-Series Gold.
| TIP: | You can define a new value for a UDP or TCP port number using the Pre-Defined Well-Known IDs window. Once defined, it is available for selection from the list of well-known values when defining the rule's traffic classification type. |
| Well-known UDP/TCP Types | Values |
|---|---|
| FTP Data | 20 |
| FTP | 21 |
| SSH | 22 |
| Telnet | 23 |
| SMTP | 25 |
| TACACS | 49 |
| DNS | 53 |
| BootP Server | 67 |
| BootP Client | 68 |
| TFTP | 69 |
| Finger | 79 |
| HTTP | 80 |
| POP3 | 110 |
| Portmapper | 111 |
| NNTP | 119 |
| NTP | 123 |
| NetBIOS Name Service | 137 |
| NetBIOS Datagram Service | 138 |
| NetBIOS Session Service | 139 |
| IMAP2/IMAP4 | 143 |
| SNMP | 161 |
| IMAP3 | 220 |
| LDAP | 389 |
| HTTPS | 443 |
| R-Exec | 512 |
| R-Login | 513 |
| R-Shell | 514 |
| LPR | 515 |
| RIP | 520 |
| SOCKS | 1080 |
| Citrix ICA | 1494 |
| RADIUS | 1812 |
| RADIUS Accounting | 1813 |
| NFS | 2049 |
| X11 (Range Start) | 6000 |
| X11 (Range End) | 6063 |
| Other | 0-65535 |
- IP Fragment
- This classification type is based on Layer 4 information in fragmented frames. IP supports frame fragmentation, where large frames are divided into smaller fragments and sent wrapped in the original Layer 3 (IP) header. When a frame is fragmented, information that is Layer 4 and above is only present in the first fragment. For example, the first fragment may be classified to Layer 4, while subsequent fragments will be classified only to Layer 3. The product line does not support Layer 4 classification for IP frames that have been fragmented, as the Layer 4 information is not present in these frames. Using the IP Fragment classification rule, any frame which is a fragment of a larger frame, is classified according to the information in the original frame. If the first fragment is classified to Layer 4, subsequent fragments will also be classified to Layer 4.
- ICMP and ICMPv6
- These classification types are based on an exact match of the ICMP (Internet Control Message Protocol) message contained in the ICMP tag within a frame. Select an ICMP well-known value type from the list of well-known values (some well-known value types also let you select a code), or select Other and manually enter the value in hexadecimal form. The format of the value is 0xXXYY, where "XX" is the ICMP type, and "YY" is the associated code, if applicable. You can enter a range of values, however range rules are not supported on legacy devices or N-Series Gold.
- IP Type of Service
- This classification type is based on an exact
match of the one-byte ToS/DSCP field contained in the IP header of a frame.
The ToS (Type of Service) or DSCP (Diffserve Codepoint) value is defined by an 8-bit hexadecimal number
between 0 and FF. Enter a value or click Select to open a window where
you can generate a hex value.
For information on how to generate a ToS or DSCP value, see the
ToS/DSCP Configuration window or the ToS/DSCP Value Definition Chart.
Type of Service can be used by applications to indicate priority and Quality of Service for each frame. The level of service is determined by a set of service parameters which provide a three way trade-off between low-delay, high-reliability, and high-throughput. The use of service parameters may increase the cost of service. In many networks, better performance for one of these parameters is coupled with worse performance on another. Except for very unusual cases, at most, two of the parameters should be set.
For a ToS value, the 8-bit hexadecimal number breaks down as follows:
Bits 0-2: Precedence
Bit 3: 0=Normal Delay, 1=Low Delay
Bit 4: 0=Normal Throughput, 1=High Throughput
Bit 5: 0=Normal Reliability, 1=High Reliability
Bits 6-7: Explicit Congestion NotificationThe precedence bits (bits 0-2) break down as follows:
111 - Network Control
110 - Internetwork Control
101 - CRITIC/ECP
100 - Flash Override
011 - Flash
010 - Immediate
001 - Priority
000 - RoutineThe Network Control precedence designation is intended to be used within a network only. The actual use and control of that designation is up to each network. The Internetwork Control designation is intended for use by gateway originators only.
For a DSCP value, the value represents codepoints for two Differentiated Services (DS) Per-Hop-Behavior (PHB) groups called Expedited Forwarding (EF) and Assured Forwarding (AF). For more information on these PHB groups, refer to RFC 2597 and RFC 2598.
- IP Protocol Type
- This classification type is based on the specific protocol type
defined in a field contained in the IP header of each frame. Select
a protocol from the list of well-known values, or select Other
and manually enter the value in decimal form. You can enter a range
of values, however range rules are not supported on legacy devices or N-Series Gold.
| TIP: | You can define a new value for a UDP or TCP port number using the Pre-Defined Well-Known IDs window. Once defined, it is available for selection from the list of well-known values when defining the rule's traffic classification type. |
| Well-known IP Protocol Types | Values |
|---|---|
| ICMP | 1 |
| IGMP | 2 |
| TCP | 6 |
| EGP | 8 |
| UDP | 17 |
| IPv6 (encapsulated in IPv4 packets) | 41 |
| RSVP | 46 |
| GRE | 47 |
| ESP | 50 |
| AH | 51 |
| ICMPv6 | 58 |
| EIGRP | 88 |
| OSPF | 89 |
| PIM | 103 |
| VRRP | 112 |
| L2TP | 115 |
| Other | 0-255 |
Layer 4 -- Application Transport Classification Types
Layer 4 IP classification types allow you to define classification rules based on specific Layer 4 TCP or UDP port numbers contained in the header of an IP frame. You can specify a specific port number or a range of port numbers.
Note: Certain devices do not support Layer 4 classification for IP frames that have been fragmented, as the Layer 4 information is not present in these frames. If a device has an FDDI HSIM installed, Layer 4 classification will not be supported for any frames larger than 1500 bytes. Frames larger than 1500 bytes are fragmented internally in the switch. When creating classification rules based on specific Layer 4 information, using the IP Fragment classification rule will allow fragmented frames to be classified according to the Layer 4 information contained in the original frame.
- IP UDP Port Source, IP UDP Port Destination, IP UDP Port Bilateral
- These classification types are based on specific Layer 4 UDP port
numbers contained within the header of an IP frame. Select a UDP
type from the list of well-known values, or select Other and
manually enter the value in decimal form. (UDP port numbers are defined in RFC
1700.) You can enter a range of values, however range rules are not
supported on legacy devices or N-Series Gold. Enter a valid IPv4 or IPv6 address and
optional mask ("/n"), if desired. The IP
address is an optional field and does not have to be specified. It
is only valid for non-range port values.
| TIP: | You can define a new value for a UDP or TCP port number using the Pre-Defined Well-Known IDs window. Once defined, it is available for selection from the list of well-known values when defining the rule's traffic classification type. |
| Well-known UDP Types | Values |
|---|---|
| FTP Data | 20 |
| FTP | 21 |
| SSH | 22 |
| Telnet | 23 |
| SMTP | 25 |
| TACACS | 49 |
| DNS | 53 |
| BootP Server | 67 |
| BootP Client | 68 |
| TFTP | 69 |
| Finger | 79 |
| HTTP | 80 |
| POP3 | 110 |
| Portmapper | 111 |
| NNTP | 119 |
| NTP | 123 |
| NetBIOS Name Service | 137 |
| NetBIOS Datagram Service | 138 |
| NetBIOS Session Service | 139 |
| IMAP2/IMAP4 | 143 |
| SNMP | 161 |
| IMAP3 | 220 |
| LDAP | 389 |
| HTTPS | 443 |
| R-Exec | 512 |
| R-Login | 513 |
| R-Shell | 514 |
| LPR | 515 |
| RIP | 520 |
| SOCKS | 1080 |
| Citrix ICA | 1494 |
| RADIUS | 1812 |
| RADIUS Accounting | 1813 |
| NFS | 2049 |
| X11 (Range Start) | 6000 |
| X11 (Range End) | 6063 |
| Other | 0-65535 |
- IP TCP Port Source, IP TCP Port Destination, IP TCP Port Bilateral
- These classification types are based on specific Layer 4 TCP port
numbers contained within the header of an IP frame. Select a TCP
type from the list of well-known values, or select Other and
manually enter the value in decimal form. (TCP port numbers are
defined in RFC 1700.) You can enter a range of values, however range
rules are not supported on legacy devices or N-Series Gold. Enter a valid IPv4 or
IPv6 address and optional mask ("/n"), if
desired. The IP address is an optional field and does not have to be
specified. It is only valid for non-range port values.
| TIP: | You can define a new value for a UDP or TCP port number using the Pre-Defined Well-Known IDs window. Once defined, it is available for selection from the list of well-known values when defining the rule's traffic classification type. |
| Well-known TCP Types | Values |
|---|---|
| FTP Data | 20 |
| FTP | 21 |
| SSH | 22 |
| Telnet | 23 |
| SMTP | 25 |
| TACACS | 49 |
| DNS | 53 |
| BootP Server | 67 |
| BootP Client | 68 |
| TFTP | 69 |
| Finger | 79 |
| HTTP | 80 |
| POP3 | 110 |
| Portmapper | 111 |
| NNTP | 119 |
| NTP | 123 |
| NetBIOS Name Service | 137 |
| NetBIOS Datagram Service | 138 |
| NetBIOS Session Service | 139 |
| IMAP2/IMAP4 | 143 |
| SNMP | 161 |
| IMAP3 | 220 |
| LDAP | 389 |
| HTTPS | 443 |
| R-Exec | 512 |
| R-Login | 513 |
| R-Shell | 514 |
| LPR | 515 |
| RIP | 520 |
| SOCKS | 1080 |
| Citrix ICA | 1494 |
| RADIUS | 1812 |
| RADIUS Accounting | 1813 |
| NFS | 2049 |
| X11 (Range Start) | 6000 |
| X11 (Range End) | 6063 |
| Other | 0-65535 |
- IP UDP Port Source Range, IP UDP Port Destination Range, IP UDP Port Bilateral Range
- These classification types are based on Layer 4 UDP port numbers contained within the header of an IP frame. When you select this type, you enter a range of UDP port numbers that the port number in the header will be matched against. Enter the start and end range values in decimal form. UDP port numbers are defined in RFC 1700.
- IP TCP Port Source Range, IP TCP Port Destination Range, IP TCP Port Bilateral Range
- These classification types are based on Layer 4 TCP port numbers contained within the header of an IP frame. When you select this type, you enter a range of TCP port numbers that the port number in the header will be matched against. Enter the start and end range values in decimal form. TCP port numbers are defined in RFC 1700.
Layer 7 -- Application Classification Types
Layer 7 IP classification types allow you to define classification rules based on specific Layer 7 application types.
- Application
- This rule type allows management of traffic for a specific application type, for example Apple traffic (Bonjour) using mDNS-SD. The following application types are supported:
-
- LLMNR - (Link Local Multicast Name Resolution) Query/Response
This protocol is based on the Domain Name System (DNS) packet format. It allows hosts to perform name resolution for hosts on the same local link. - SSDP - (Simple Service Discovery Protocol) Query/Response
SSDP is a Universal Plug-and-Play (UPnP) based protocol. SSDP uses the NOTIFY and MSEARCH HTTP methods to discover and advertise services on the network. - mDNS-SD - (Multicast Domain Name System – Service Discovery) Query/Response
DNS-SD is a service discovery protocol that utilizes the Domain Name System. Multicast DNS is a protocol that is mostly compatible with normal DNS but uses link local multicast addressing, allowing for zero configuration networking (zeroconf) functionality.
- LLMNR - (Link Local Multicast Name Resolution) Query/Response
Examples of How Rules are Used
Traffic Classification rules are used to provide four key policy features: Traffic Containment, Traffic Filtering, Traffic Security, and Traffic Priority.
Traffic Containment
Using classification rules, network administrators can group together users of a given protocol, subnet, or application, and control where their traffic can logically go on the network.
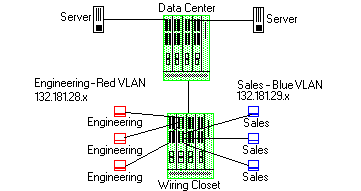
The figure above shows a configuration where the network administrator wants to separate end-user traffic into VLANs based on the assigned IP subnet of each department. This can easily be accomplished by creating two Layer 3 classification rules based on the IP subnet range of the respective departments.
Rule 1 - Engineering, which uses the 132.181.28.x subnet, will be assigned to the Red VLAN.
Rule 2 - Sales, which uses the 132.181.29.x subnet, will be assigned to the Blue VLAN.
Based on these two Layer 3 classification rules, the traffic from the Engineering VLAN will be isolated from the Sales VLAN. Since these rules are based on Layer 3 information, an Engineering user could enter the network from a connection in the Sales department, and that user would still be contained in the Engineering VLAN.
Traffic Filtering
Classification rules can also be used to filter out (discard) specific unwanted traffic. Filter criteria can include things such as broadcast routing protocols, specific IP addresses, or even applications such as HTTP or SMTP.
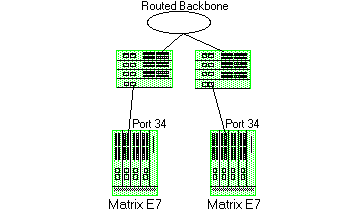
The figure above shows a common configuration in which a routed backbone is using both RIP and OSPF for its routing protocols. The network administrator does not want the multicast OSPF and broadcast RIP frames propagated to the end stations. The network is designed so that only end users are attached to the E7 devices.
To implement filtering in this scenario, a Layer 3 rule and a Layer 4 rule will be created.
Rule 1 (Layer 3) - Any frame received with an IP Protocol Type of 89 (OSPF) will be discarded.
Rule 2 (Layer 4) - Any frame received with a Bilateral UDP port number of 520 (RIP) will be discarded.
Based on this configuration, all RIP and OSPF frames will be filtered from the end users.
Traffic Security
Traffic Security uses the same concepts as Traffic Filtering. Imagine a scenario where network access is provided to a group of unknown users. There have been problems with these unknown users "hacking" into the router and altering the configuration. A simple classification rule can be put in place that will prevent these types of occurrences.
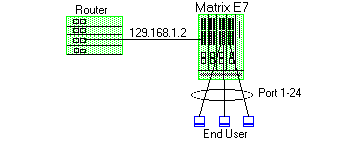
In the figure above, the network components include a router and an E7 device. In this configuration end-users connect to the ports of the E7 device.
Since the end-users would never need to communicate directly to the router using the router's IP address, a Layer 3 IP classification rule will be used.
Rule - Any frames received by the switch with a destination IP address of the router (129.168.1.2) will be discarded.
The end result is that any frames from a user trying to "hack" into the router will be discarded before ever reaching the router.
Traffic Prioritization
Classification rules can be used to specify that certain network applications receive the highest transmission priority. For example, a network administrator wants to assign priority to three network applications, SAP R/3, web traffic, and email, in that order.
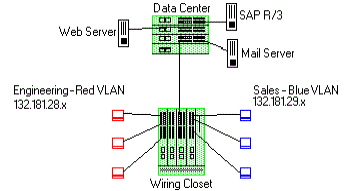
To accomplish the prioritization goals in this example, there are two main steps required: creating the classification rules, and then configuring the priority-to-transmit queue mapping for the switch, if needed.
First, create one Layer 3 and two Layer 4 classification rules.
Rule 1, Layer 3 (SAP R/3) - All frames to or from the IP address of the SAP R/3 server will be tagged with a priority indicator of 7 (highest).
Rule 2, Layer 4 (Web) - All frames with a TCP port number of 80 (HTTP) will be tagged with a priority indicator of 5.
Rule 3, Layer 4 (email) - All frames with a TCP port number of 25 (SMTP) will be tagged with a priority indicator of 3.
Note: An IP address classification was selected for Rule 1 because it has been observed that SAP R/3 dynamically negotiates the TCP/UDP port used, so the port number selections vary from session to session. If this was not the case, a Layer 4 UDP classification could be used.
Then, configure the priority-to-transmit queue mappings. Each switch has default priority-to-transmit queue mappings. You can use these defaults or change the mappings using local management or NetSight Console. In addition, Policy Manager provides the ability to configure transmit queues as part of the Role-Based Rate Limits and Transmit Queue Configuration class of service mode. This functionality is available only on certain devices such as the S-Series and N-Series Gold and Platinum devices (refer to the NetSight Firmware Support tables for specific device/firmware rate limit support).
Based on the default priority-to-traffic queue mapping for an E7 device, the priorities assigned above will work out so that each frame classification type will be mapped to the desired traffic queue. This means that no user configuration of the priority-to-transmit queue mapping would be required.
With the classification rules described above, the network traffic would be prioritized as shown in the table below:
| Application | Classification Type | Desired Priority | Priority Value | E7 Traffic Queue |
|---|---|---|---|---|
| SAP R/3 | Bilateral IP | High | 7 | 3 |
| Web | TCP Port Number | Medium | 5 | 2 |
| TCP Port Number | Low | 3 | 1 |
Classification Rules Precedence
When there is a role with multiple classification rules assigned to a port, the device determines which rule takes precedence based on an order of precedence that is predefined in the device. Network administrators should have a comprehensive understanding of classification precedence, as it can significantly impact the operation of traffic classification rules. The Device Support Tab (Role) provides rule precedence information for each role. For additional information on rule precedence, see your device hardware documentation.
The device determines the order of precedence based on the classification types. If there are multiple rules with the same precedence, the more granular rule takes effect. Here are two examples of how this works:
- A rule that uses an IP address with a full mask has precedence over a rule with an IP address with a less granular mask. For example, an IP address of 1.1.1.1/32 would have precedence over an IP address of 1.1.1.1/24.
- A rule that uses an IP address with a port number has precedence over a rule with an IP address that does not. For example, an IP address of 1.1.1.1:80 would have precedence over an IP address of 1.1.1.1. This means that an IP Socket rule has a higher precedence than an IP Address rule.
The Precedence Table lists the order of precedence with 1 being the highest precedence, and 27 being the lowest.
| Classification Rule | Precedence |
|---|---|
| MAC Address Source | 1 |
| MAC Address Destination | 2 |
| Application | 3 |
| IPX Network Source | 4 |
| IPX Network Destination | 5 |
| IPX Socket Source | 6 |
| IPX Socket Destination | 7 |
| IPX Class of Service | 8 |
| IPX Packet Type | 9 |
| IPv6 Address Source | 10 |
| IPv6 Address Destination | 11 |
| IPv6 Flow Label | 12 |
| IP Address Source | 13 |
| IP Address Destination | 14 |
| IP Fragment | 15 |
| IP UDP Port Source | 16 |
| IP UDP Port Destination | 17 |
| IP TCP Port Source | 18 |
| IP TCP Port Destination | 19 |
| ICMP | 20 |
| ICMPv6 | 21 |
| IP Type of Service | 22 |
| IP Protocol Type | 23 |
| Ethertype | 24 |
| DSAP/SSAP | 25 |
| VLAN ID | 26 |
| Priority | 27 |
| NOTES: | — The precedence of a rule based on a bilateral address match is determined
frame by frame depending on whether the
rule matches the destination or source address in the frame. A bilateral
address rule which matches the
source address has higher precedence than a rule which matches a destination
address (or any other lower precedence rule). — Device precedence lists show 31 entries and use a different numbering scheme than shown above. |
|---|
Precedence Scenarios
The following scenarios illustrate the classification rule precedence on S-Series and N-Series devices.
Scenario 1
A network administrator has defined two classification rules:
Rule 1- All frames with a UDP port number of 55 (ISI Graphic Language) are assigned to the Red VLAN.
Rule 2- All frames sourced from the 132.181.28.x subnet are assigned to the Blue VLAN.
If a frame is received with a source address of 132.181.28.99 and a UDP port number of 55, the frame will be assigned to the Blue VLAN because as shown in the Precedence Table, an IP Address rule takes precedence over a UDP rule.
Scenario 2
A network administrator defines two classification rules:
Rule 1- All frames with an IP ToS value of AA are assigned a priority of 7.
Rule 2- All frames with a TCP port number of 80 (HTTP) are assigned a priority of 3.
If a frame is received with a ToS value of AA and a TCP port number of 80, the frame will be assigned a priority of 3, because as shown in the Precedence Table, TCP port number classifications take precedence over IP ToS classifications.
For information on related tasks: