Getting Started with Policy Manager gives you an overview of Policy Manager, and provides a quick tour of its components using the Default Policy Domain. It also includes a summary of the basic steps you must perform to create and configure policies with Policy Manager.
Because Getting Started is meant to be used side-by-side with Policy Manager, it will be most useful if you install Policy Manager first. Once Policy Manager is installed, you can use the steps and suggestions below as an aid in planning and implementing your network policy profiles using Policy Manager.
It is recommended that you read the following Policy Manager information in sequence before you implement Policy Manager on your network:
- Installation
- Release Notes
- Getting Started with Policy Manager (this guide)
- Authentication Configuration Guide
- Policy Manager Concepts
This guide includes the following information:
Policy Manager Overview
NetSight Policy Manager is a configuration tool that simplifies the creation and enforcement of policies on networks, enabling network engineers, information technology administrators, and business managers to work together to create the appropriate network experience for each user in their organization.
Policy Manager enables you to create policy profiles, called roles, that are assigned to the ports in your network. These roles are based on the existing business functions in your company, and consist of services that you create, made up of traffic classification rules. Roles provide four key policy features: traffic containment, traffic filtering, traffic security, and traffic prioritization.
Policy Manager provides authentication via a RADIUS server to identify users at the time they log in to the network. Only after users have been authenticated are they given customized access capabilities based on the role they are assigned.
The illustration below shows the Policy Manager relationship hierarchy, with Rules at the base to define specific packet handling behaviors, Roles at the top to identify specific job functions in the organization, and Services in the middle, providing the interface between the two layers.

Using Policy Manager wizards and configuration tools, you can create multiple roles
tailored to your specific needs, and set a default policy for some or all of your
network devices and ports. These policies can be deployed on multiple
devices throughout your switch fabric. Once the network infrastructure
has been empowered to enforce the relationship hierarchy, no further communication
with the Policy Manager application is needed.

Quick Tour
The Quick Tour will acquaint you with Policy Manager by associating the concepts and features presented here with something you can actually see in the application. While the Quick Tour does not explain all of Policy Manager's features, it shows you how to do some of the basic Policy Manager operations. Links to more detailed instructions for performing basic and more complex Policy Manager tasks are provided throughout the Quick Tour. As you get into the Quick Tour, you will notice that each section of the tour begins with an explanation in regular type, followed by the actual steps you perform, highlighted.
The Quick Tour assumes that you have installed and launched Policy Manager. It also assumes you have installed and launched NetSight Console, and performed a Console Discover to populate the NetSight Database with your network devices. Refer to the Console online Help for information on performing a Discover operation.
By default, when Policy Manager opens, the main window is displayed using the "Consolidated Tab Configuration." In the Consolidated Tab Configuration, there are two left-panel tabs: Roles/Services and Network Elements/Port Groups. Access Control and Class of Service tabs are launched in separate configuration windows from the Edit menu. The Quick Tour is written according to this tab configuration. For more information on available Tab Configurations, see the Tab Configuration Option Help topic.
The Quick Tour covers the following features:
- Understanding Policy Domains
- Understanding Roles
- Understanding Services
- Working with Service Groups
- Understanding Traffic Classification Rules
- Adding Devices
- Configuring Devices for Authentication
- Working with Device Groups
- Viewing Port Configuration Information
- Working with Port Groups
- Working with VLANs
- Viewing Classes of Service
- Using Policy Manager Wizards
- Saving the Domain
- Enforcing
- Accessing Policy Manager Help
Understanding Policy Domains
Policy Manager provides the ability to create multiple policy configurations by allowing you to group your roles and devices into Policy Domains. A Policy Domain contains any number of roles and a set of devices that are uniquely assigned to that particular domain. Policy Domains are centrally managed in the database and shared between Policy Manager clients.
The first time you launch Policy Manager, you are in the Default Policy Domain. You can manage your entire network in the Default Policy Domain, or you can create multiple domains each with a different policy configuration, and assign your network devices to the appropriate domain. The Default Policy Domain is pre-configured with a Policy Manager Database file called Demo.pmd. The roles, services, rules, VLAN membership, and class of service in this initial configuration define a suggested implementation of how network traffic can be handled. This is a starting point for a new policy deployment and will often need customization to fully leverage the power of a policy-enabled network.
For more information about domains, see Policy Domains in the Concepts Help topic.
In the Quick Tour, we'll use the Default Policy Domain as a way to explore the basic features and functionality of Policy Manager. Later, you may find the Default Policy Domain useful as you create your own Policy Domains.
If you have just launched Policy Manager for the first time, you are in the Default Policy Domain and you can proceed to the next step, Understanding Roles. If someone else has been using Policy Manager before you, use the following steps to create a Demonstration Domain that you can use for the Quick Tour.
Note: If someone else has been using Policy Manager before you, when you create the new domain, you may be prompted to save the previous domain's configuration.
Quick Tour: Creating a Policy Domain.
-
Select Domain > Create Domain. Enter the domain name
Demonstration Domainfor the new domain and click OK. The new Demonstration Domain opens. -
Select File > Import > Import From File. The Import from File window opens.
-
Click the Browse button and select the Demo.pmd file. Click Open.
-
Click the Select All button to select all the data elements to import.
-
Click OK. The data elements will be imported from the Demo.pmd file into the new Demonstration Domain.
When you selected the Demo.pmd, you probably noticed that there are many .pmd files to select from. These different files are pre-configured domains that include roles, services, and rules designed for specific network scenarios.
For more information:
Now that you've created the Demonstration domain, we will explore Policy Manager in a little more depth.
Understanding Roles
Roles are usually designed to reflect different users in your organization and to provide customized access capabilities based on the role users have in your organization. For example, accounting and engineering personnel have different network access and priority needs and therefore might have different roles.
Quick Tour: Checking out roles.
-
Click on the left-panel Roles tab in the Policy Manager main window.
-
Hold the cursor over a role name to see a tooltip describing the role.
-
Click on the various roles listed in the left panel, and in the right panel you'll see tabs that display specific information for each role. Click the right-panel tabs to see the information they contain.
A role can be made up of one or more network access services that are defined in Policy Manager. These services determine how network traffic will be handled at any network access point configured to use that role. A role may also contain default access control (VLAN) and/or class of service designations that will be applied to traffic not handled specifically by the services contained in the role. A role can contain any number of services or service groups.
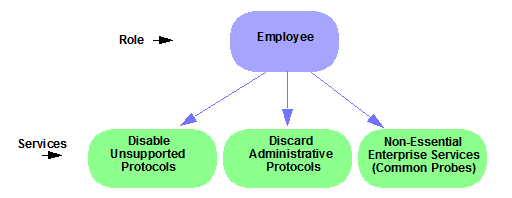
Roles are assigned to users during the authentication process. When a user successfully authenticates, the port is opened, and if there was a role assigned to the user, that role is applied to the port. A role can also be directly assigned to a port as a default role for instances when authenticated users are not assigned a role. If an end user on a port was not assigned a role when logging in (authenticating), or if authentication is inactive on a port, then the port's default role will take effect. However, if a user is assigned a role upon login, then that role will override any default role on the port.
To create and define a role, you can use the Role Wizard or do it using the right-panel Role tabs.
Right now, we will just create and name a role without defining it further:
Quick Tour: Creating a role.
-
In the Policy Manager left panel, select the Roles tab.
-
Right-click the Roles folder, and select Create Role.
-
Enter the role name
Office Assistantin the highlighted box and press Enter.
For more information:
Understanding Services
Roles can be made up of one or more network access services. These services determine how network traffic will be handled at any network access point configured to use that role. Policy Manager allows you to create Local Services (services that are unique to the current domain) and Global Services (services that are common to all domains). Services can be one of two types: Manual Service or Automated Service. Manual services contain customized classification rules that you create, while Automated services are associated with a particular set of network resources.
Manual services contain one or more traffic classification rules that define how a network access point will handle traffic for a particular network service or application. For example, you might create a Manual service called "Restricted Employee" that contains a classification rule that discards TCP HTTP traffic.
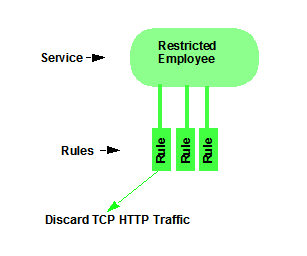
We will create a Manual service and add it to a role later on. Right now, we'll just take a look at the services in the domain.
Quick Tour: Checking out Services.
-
Click on the left-panel Services tab in the Policy Manager main window.
-
Expand the Service Repository folder and then the Local Services folder.
-
Expand the Services folder to view a list of services.
-
Hold the cursor over a service name to see a tooltip describing the service.
-
Expand a service or two to see the individual classification rules that make up the service.
-
Select a service or two in the left panel to see the right-panel tabs that display specific information for each service. Click the right-panel tabs to see the information they contain.
For more information:
Working with Service Groups
Services can be grouped together into Service Groups. This allows you to easily add a set of services to one or more roles.
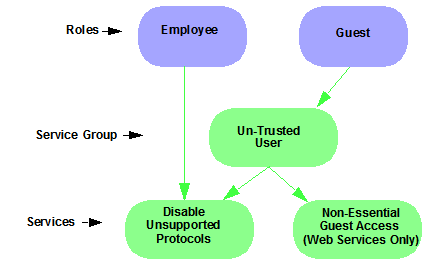
Quick Tour: Checking out Service Groups.
-
Click on the left-panel Services tab in the Policy Manager main window.
-
Expand the Service Repository folder and then the Local Services folder. Expand the Service Groups folder.
-
Expand the Acceptable Use Policy service group to see its services. Note that these services are also listed under the Services folder.
After you have defined and created your services, you can easily create a Service Group and then drag and drop your services into the group.
Quick Tour: Creating a Service Group.
-
Click on the left-panel Services tab in the Policy Manager main window.
-
Expand the Service Repository folder and then the Local Services folder.
-
Right-click the Service Groups folder, and select Create Service Group.
-
Enter the service group name
Trusted Userin the highlighted box and press Enter. -
Drag and drop one or two of the existing Acceptable Use Policy services from the Acceptable Use Policy service group into the Trusted User service group. Notice that this makes a copy of the existing service in the new folder.
For more information:
Understanding Traffic Classification Rules
Traffic Classification rules allow you to assign access control (VLAN membership) and/or class of service to your network traffic based on the traffic's classification type. Classification types are derived from Layers 2, 3, and 4 of the OSI model, and all network traffic can be classified according to specific layer 2/3/4 information contained in each frame.
A Traffic Classification rule has two main parts: Traffic Description and Actions. The Traffic Description identifies the traffic classification type for the rule. Actions apply access control, class of service, security, and/or accounting behavior to packets matching the rule.
You create a rule for a specific service, but a rule can be added to multiple services simply by using drag and drop to copy the rule from one service to another in the Services tab.
Quick Tour: Checking out Rules.
-
In the left-panel Services tab, expand the Acceptable Use Policy service group.
-
Expand the Deny Unsupported Protocol Access service and click on the Discard AppleTalk rule.
-
Click on the right-panel General tab to see the rule's Traffic Description and Actions.
-
Use the Edit button to add a description to the General Tab, for example: AppleTalk not supported on this network.
For more information:
Adding Devices
The first step in adding network devices to Policy Manager, is to add the devices to the NetSight database. You do this initially, by performing a Console Discover to populate the database, or by using Console to import devices from a .ngf file. We will assume that you have already done this. If you need more information, refer to your NetSight Console online Help.
Once devices have been added to the NetSight database, you must assign the devices to a Policy Domain using Policy Manager. As soon as the devices are assigned to a domain, they are automatically displayed in the Policy Manager device tree. Only devices assigned to the domain you are currently viewing are displayed.
Quick Tour: Assigning Devices to a Domain.
-
In the Policy Manager main window, select Domain > Assign Devices to Domain. The Assign Devices to Domain window opens.
-
In the left panel, the Unassigned device tree contains all the devices in the database that have not been assigned to a domain. The right panel displays the devices in the current domain.
-
For the Quick Tour, select a couple of devices to add to the domain and click Add. Click OK to add the devices.
-
You can also use this window to remove a device from the current domain. This removes the device from the current domain and places it in the Unassigned folder. It does not delete the device from the NetSight database.
After you have initially added your devices, you can use Policy Manager's Add Device window to add a single device to the database. Adding a device this way also automatically adds it to the current domain.
For more information:
Configuring Devices for Authentication
Now that you have added devices to your domain, you can configure them for authentication. In Policy Manager, several types of authentication are offered, including Web-based, 802.1X, MAC, and CEP authentication. In order to take advantage of the authentication features of Policy Manager, you need to configure your network and your devices to work with a RADIUS server. In the Quick Tour, we will take a look at the right-panel tabs where you can view and modify authentication and RADIUS configuration on devices.
Quick Tour: Viewing the Authentication Settings on a Device.
-
In the Policy Manager left panel, select the Network Elements tab.
-
Expand the All Devices folder and select a device.
-
In the right panel, look at the Details View tab. Expand a Ports or Slot folder to see ports on the device. Scroll to the right to see all the port information available on this tab.
-
Select the right-panel Authentication tab. This tab is where you specify the authentication type, enable or disable authentication, and configure your authentication settings for the selected device.
-
Select the RADIUS tab. On this tab you can enable the device as a RADIUS client, and set up communication between the RADIUS client device and the RADIUS server.
For more information:
Working with Device Groups
In the Network Elements tab, devices are listed individually, but they are also grouped into Device Groups. This can be useful when you want to configure policies for a group of devices. An example of how devices could be grouped is shown here.
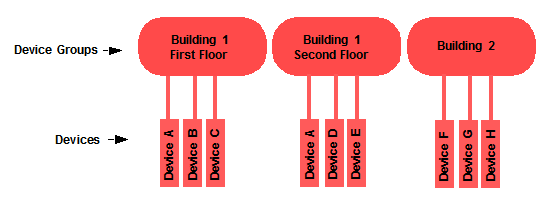
Policy Manager provides several system-created device groups for your convenience. When a device is assigned to a domain, it automatically becomes a member of the appropriate group:
- All Devices - contains all the devices that are assigned to the current domain.
- Grouped By
- contains five subgroups:
- Chassis -- contains subgroups for specific chassis in the domain.
- Contact -- contains subgroups of the devices in a domain based on the system contact.
- Device Types -- contains subgroups for the specific product families and device types in the domain.
- IP -- contains subgroups based on the IP subnets in the domain.
- Location -- contains subgroups of the devices in a domain based on the system location.
You can also create your own device groups, called user-defined device groups. Policy Manager system-created device groups are displayed with blue folders. Any group you add will be displayed with a yellow folder.
For more information:
Viewing Port Configuration Information
After devices have been imported into Policy Manager, you can view and configure their ports by selecting a device and displaying its ports in the right-panel Details View tab or Ports tab.
Quick Tour: Viewing Port Configuration Information.
-
Click on the left-panel Network Elements tab in the Policy Manager main window.
-
Expand the All Devices folder and select a device.
-
In the right-panel Details View tab, expand a Ports or Slot folder to display ports on the device.
-
Right-click on a port and select Properties. The Port Properties window opens.
-
Take a look at all the tabs where you can view and modify configuration information for the selected port.
For more information:
Working with Port Groups
Policy Manager allows you to group ports into User-Defined Port Groups, similar to the way you can group services into service groups. Port groups enable you to configure multiple ports on the same device or on different devices, at the same time. Policy Manager also provides you with Pre-Defined Port Groups. Every time one of the Pre-Defined Port Groups is accessed, Policy Manager goes to the devices in the current domain and retrieves the ports which fit the pre-defined characteristics of the port group.
Quick Tour: Checking out Pre-Defined Port Groups.
-
Click on the left-panel Port Groups tab in the Policy Manager main window.
-
Expand the Port Groups folder.
-
Expand the Pre-Defined Port Groups to see the groups.
Quick Tour: Creating a User-Defined Port Group.
-
Expand the Port Groups folder.
-
Right-click the User-Defined Port Groups folder, and select Create Port Group.
-
Type in a Port Group name in the highlighted box and press Enter.
-
Look at the Ports tab in the right panel. Notice that you can add a description of the port group and add individual ports to the group.
For more information:
Working with VLANS
All traffic in a Policy Manager network is assigned membership in a VLAN. Roles are used to assign VLAN membership to traffic either through the role's default access control or through the role's services which may include traffic classification rules that assign VLAN membership (access control).
When you open a new domain, the Global VLANs folder is prepopulated with the Default VLAN (not to be confused with a default VLAN that is assigned to a role, although the Default VLAN could be a default VLAN for a role). You can then create additional VLANs and assign them as default access control for a role and/or use them to define traffic classification rules. You can view the roles and services associated with a VLAN using the Role/Service Usage window accessed by right-clicking on a VLAN. You can also make role and service changes from this window.
Island VLANs are used in Policy VLAN Islands, which enable you to deploy a policy across your network, while restricting user access to only selected local devices. You must select the Policy VLAN Islands Enabled checkbox (on the Edit Menu) to see the Island VLANs folder and the Policy VLAN Islands folder.
Quick Tour: Checking out VLANs.
-
From the Policy Manager Edit menu, select Access Control Configuration. The Access Control Configuration window opens.
-
In the left panel, expand the Global VLANs folder to see the individual VLANs.
-
Click on the Default VLAN listed and view the General tab in the right panel.
For more information:
Viewing Classes of Service
Policy Manager lets you create a class of service (CoS) that includes one or more of the following components: an 802.1p priority, an IP type of service (ToS) value, rate limits, and transmit queue configuration. You can then assign the class of service as a classification rule action, as part of the definition of an automated service, or as a role default.
Quick Tour: Checking out Classes of Service.
-
From the Policy Manager Edit menu, select Class of Service Configuration. The Class of Service Configuration window opens.
-
Notice that the window is pre-populated with eight static classes of service, each associated with one of the 802.1p priorities (0-7). You can use these classes of service as is, or configure them to include ToS/DSCP, drop precedence, rate limit, and/or transmit queue values. You can also rename them, if desired. In addition, you can also create your own classes of service (user-defined CoS).
-
Scroll to the right to see that you can also use this window to define inbound and outbound rate limits and outbound transmit queue rate shapers for your classes of service.
-
Click on the Table Display Filter button to see a menu that lets you specify which columns you would like displayed in the table. For example, if you want to view the inbound rate limits that are configured, you can select to display only Inbound RL, making it easier for you to focus in on the desired information.
-
Click on the Domain Managed CoS Components button to see a menu you can use to specify the CoS components you will be configuring for this domain. This will determine what CoS settings will be written to your network switches on Enforce. For example, if you select only Inbound RL and Outbound RL, then Policy Manager will enforce the rate limits you configure, but will not overwrite any transmit queue settings configured on the device via the Command Line Interface (CLI).
For more information:
- Getting Started with Class of Service
- How to Define Rate Limits
- How to Configure Transmit Queues
- How to Create a Class of Service
Using Policy Manager Wizards
In Policy Manager, you can create roles, services, rules, and VLANs, and configure devices and ports, by selecting the appropriate item in the left panel and filling out the right-panel tabs. But Policy Manager also provides wizards that lead you through the steps required to perform these functions.
If you are creating roles, services, and rules, and configuring devices and ports from scratch, the wizards can be easier to use. Once you've created everything you need, you may find it easier to make changes and additions on the right-panel tabs, or you may still want to use the wizards, depending on the situation.
The wizards provided by Policy Manager include the Role Wizard, the Service Wizard, the Classification Rule Wizard, the Device Configuration Wizard, the Port Configuration Wizard, and the Policy VLAN Islands Configuration Wizard. The Service Wizard incorporates the elements of the Classification Rule Wizard, and the Role Wizard incorporates the elements of the Service Wizard, including the Classification Rule Wizard.

In the Quick Tour, we will use the Service Wizard to create a Manual service that includes one classification rule. We will then apply it to the role you created earlier in the Quick Tour.
Quick Tour: Creating a Service Using the
Service Wizard.
Let's create a service that discards TCP HTTP traffic.
-
In the Policy Manager left panel, select the Services tab.
-
Expand the Service Repository folder and then the Local Services folder.
-
Right-click the Services folder, and select Service Wizard.
-
Enter
Restricted Employeefor the service name and click Next. -
Make sure the Service Type selected is Manual, and click Next.
-
Enter
Discard HTTPfor the classification rule name and click Next. -
Choose Enabled as the Rule Status and click Next.
-
Choose All Devices as the Rule Type and click Next.
-
Leave the TCI Overwrite Status as Disabled and click Next.
-
Choose Layer 4 - Application Transport as the Traffic Classification Layer, and click Next.
-
Choose IP TCP Port Destination as the Traffic Classification Type and click Next.
-
Choose Well-Known Values and HTTP (80) as the TCP Type and click Next.
-
Adding an IP Address is optional, so just click Next.
-
Select the Deny Traffic option from the Access Control drop-down list. Click Next.
-
View the Classification Rule Summary and click Next.
-
Select the role you created earlier (Office Assistant) and click Finish.
-
Look at the right side of the Status Bar at the bottom of the window. The Enforce icon
 means your new
role and its service need to be enforced (written to the devices). We'll talk about
that later.
means your new
role and its service need to be enforced (written to the devices). We'll talk about
that later.
For more information:
- Using the Service Wizard
- Using the Classification Rule Wizard
- Using the Device Configuration Wizard
- Using the Port Configuration Wizard
- Using the Role Wizard
Saving the Domain
After a Policy Domain has been changed, you must save the domain to notify all clients that are viewing that domain of the change and automatically update their view with the new configuration. A Save icon is displayed in the status bar at the bottom of the main window when you have made changes to the domain that need to be saved.
Quick Tour: Saving the Domain.
-
Note that a Save icon
 appears on the
status bar. This is a reminder that you need to save changes you've made to
the domain.
appears on the
status bar. This is a reminder that you need to save changes you've made to
the domain.
-
From the menu, select File > Save Policy Domain.
-
The domain is saved and all clients viewing the domain will automatically have their view updated with the new configuration.
For more information:
Enforcing
Any time you add, make a change to, or delete a role or any part of it (any of its services and/or rules), the devices in your current domain need to be informed of the change so that your revised policy configuration can take effect. This is accomplished by enforcing -- writing your policy configuration to a device or devices. Enforce operations are performed only on the current domain.
To enforce to all
devices in the current domain, you would use the Enforce button
in the toolbar or the File > Enforce Role Set menu option. To
enforce to a single device, you would right-click the device and select Enforce
Role Set from the menu. If you have made any changes that need to be
enforced, the Enforce icon ![]() appears on the status bar at the bottom of the Policy
Manager window as a reminder.
appears on the status bar at the bottom of the Policy
Manager window as a reminder.
Policy Manager's Enforce Preview window enables you to view the information that will be written to your domain devices, before you actually enforce. This feature is particularly useful if you have devices that only support certain aspects of policy management. The Enforce Preview window appears whenever you initiate an enforce using one of the methods mentioned above, so that you always have a chance to review the effects of enforcing prior to actually performing the enforce. You can also access this window from the File > Enforce Preview menu option.
To determine if the roles currently in effect on your domain devices match the set of roles you have defined in your current Policy Domain configuration, use the Verify feature.
Quick Tour: Enforce Preview.
At this point, you probably don't want to actually enforce to the devices in the
domain. So let's just look at the Enforce Preview window.
-
Select File > Enforce Preview. The Enforce Preview window opens. Use the tabs in the window to check out all the information that would be written to your devices if you did perform an enforce.
For more information:
Accessing Policy Manager Help
All Policy Manager documentation is available in the Help system accessible from the application. To launch the NetSight Suite Online Help, select Help > Help Topics from the Help menu.
- Help on Policy Manager features is available via the Help > Help Topics menu option.
- Help for the tab currently displayed in the right panel is available via the Help > About This Window menu option.
- Help for a particular window is also available via a Help button on the window itself.
The Help system includes a Search feature that lets you search for specific instances of a term in all the help topics.
Quick Tour: Using the Help Search Feature.
-
Select the Help > Help Topics menu option. The NetSight Suite Online Help opens in a web browser.
-
In the left-panel you will see the Table of Contents that displays all the help topics for the NetSight Suite application.
-
At the bottom of the Table of Contents you will see a tab for Search All Topics and Favorites.
-
Click the Search All Topics tab. In the Search field, enter the word "role" and press Enter or click the Search button. A list of topics in which the term appears is displayed, along with the number of instances found in each topic. If you want to find a specific combination of words that are always next to each other in the same order, enter the search keywords within quotation marks (for example, "domain name").
-
The Search feature lets you refine the Search results by using the Filters drop-down menu to select which NetSight application's Help topics you are interested in searching. Use the drop-down menu to select the Policy Manager filter.
| TIP: | There is also a search field in the Help toolbar lets you search for a term only on the topic that is currently displayed. |
Where to Go from Here
If you have been following the recommended reading sequence, your next stop will be the Authentication Configuration Guide. If you've already done that, and have read the other recommended reading, then you are ready to start implementing your own policy configurations using Policy Manager.
Use the following summary to guide you through the basic steps for using Policy Manager.
- Configure your network for authentication (see the Authentication Configuration Guide.)
- Create your Policy Domains (see How to Create and Use Domains.)
- Add your devices to the NetSight Database and assign them to the appropriate domain.
- Configure authentication on devices and ports (see How to Configure Devices and How to Configure Ports).
- If desired, group your ports into port groups (see How to Create a Port Group).
- Create services (see How to Create a Service).
- If desired, group services into service groups (see How to Create a Service Group).
- Create roles (see How to Create a Role).
- Write your configuration to your devices (see Enforcing).
Now that you have set up your authentication and policy configuration, you can start exploring some of Policy Manager's other features:

|
and Device Access |
Use the Authorization/Device Access window to configure your
Policy Manager access privileges. The window has four tabs:
|
|

|
|
Policy Manager uses Server Locks to manage interactions between multiple clients and the server. When a user begins editing a Policy Domain, a lock is acquired for that domain at the server. That lock is not released until the same user saves the domain data. This guarantees a consistent view of that domain for all clients. | |

|
|
The Server Information window lets you view and configure certain NetSight Server functions, including management of client connections, database backup and restore, locks, and licenses. It also provides access to the server log and server statistics. | |

|
|
Use the Options window to set options for NetSight functions on a suite-wide and per-application basis. | |

|
|
Policy Manager supports Class of Service (CoS), which allows you to assign priority, modify rates, and change transmit queue behavior for your network traffic. | |

|
Network Resource Groups | Network Resource Groups are groups of network resources such as routers, VoIP (Voice over IP) gateways, and servers. You can create a network resource group and associate it with an Automated service. The Automated service automatically creates a rule with a specified action (class of service and/or access control), for each resource address in the network resource group. Automated rule types include Layer 2 MAC Address rules, Layer 3 IP Address and IP Socket rules, and Layer 4 IP UDP Port and IP TCP Port rules. | |

|
Policy VLAN Islands | Policy Manager offers you the ability to set up Policy VLAN Islands which enable you to deploy a policy across your network, while restricting user access to only selected local devices. | |

|
Web Update | Policy Manager provides an easy way to access and download product updates using a web update operation. You can perform an immediate check for updates, or schedule a routine check for updates. |
For information on related concepts:
For information on related tasks:
For information on related windows: