The device Anti-Spoofing tab allows you to configure the anti-spoofing settings and violation actions for the selected device. Anti-spoofing must be configured and enabled on the device in order for individual port anti-spoofing settings to take effect. For more information about the anti-spoofing feature, see How to Configure Anti-Spoofing.
To access this tab, select a device on the left panel's Network Elements tab, then click the Anti-Spoofing tab in the right panel.
There are three sub-tabs that provide different anti-spoofing configuration information.
Device Configuration
This tab provides access to all device-level anti-spoofing configuration. The General Settings section allows you to enable or disable anti-spoofing, audit traps, and duplicate IP checking. The Violation Actions section lets you configure the actions to impose on users that violate the station bindings that are created through anti-spoofing.
Click the graphic for more information.
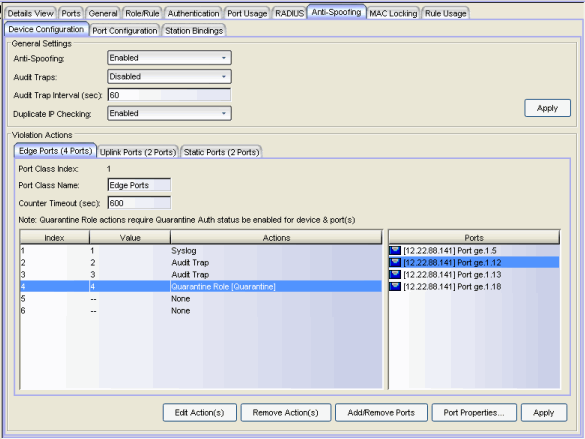
General Settings
Use the drop-down menu to enable or disable anti-spoofing for the device.
Use the drop-down menu to enable or disable audit traps for the device. This must be enabled if you have configured an audit trap as a threshold action, in order for the trap to be sent.
The number of seconds to wait before generating another audit trap for the same user. For example, in the case of a user who continually changes IP addresses, if you have multiple thresholds set to trigger audit traps, this interval prevents a large number of audit traps from being sent in a very short time. The default interval is 60 seconds. A value of zero (0) indicates that no audit traps related to anti-spoofing will be suppressed.
Use the drop-down menu to enable or disable duplicate IP checking on the device. This functionality logs duplicate IP addresses when they are bound to different MAC addresses, using syslog messages and audit traps. Read more about duplicate IP checking in How to Configure Anti-Spoofing.
Apply
Saves any change you made to the General settings.
Violation Actions
This section is where you define the threshold values and resulting actions that will be used when MAC-to-IP address binding violations occur on the device.
Thresholds are the number of violations that must occur on a single MAC-to-IP address binding before an action is performed. Each threshold can be assigned one or more of the following actions: sending a syslog message, sending an audit trap, or applying a quarantine policy.
You can define thresholds and actions for up to three different port classes per device. Port classes allow you to assign the ports on a device into different groups depending on port type.
For example, you might configure a port class for your edge ports and another port class for your uplink ports, and define different thresholds and actions for each port class. You might also want to configure a port class for ports with statically assigned addresses, allowing for a stricter threshold configuration. Another option is to configure port classes for ports that are using different methods to create MAC-to-IP bindings, such as DHCP snooping ports in one class and IP source guard ports in another class.
Up to six thresholds can be configured per port class. Typically, thresholds values are set to a low number. For example, you could configure a threshold value of 2 to trigger a syslog message to alert administrators of a binding violation. You could configure another threshold value of 5 to assign a quarantine role to a user. That way, if a user continues to violate a binding, you can restrict their access until the cause of the violation can be determined.
To create or edit a threshold and action, select a port class and then select an action index number in the table and click the Edit Action(s) button or double-click the row. The Edit Action window opens where you can configure the threshold value and action. If you assign a quarantine action, you must associate a valid quarantine policy with the quarantine action. For more information, refer to How to Create a Quarantine Role.
For each port class, you must assign the ports that will be part of the class. A port can be assigned to only one class. Use the Add/Remove Ports button to add or remove ports to or from the class. In addition, you can select a port and click the Port Properties button to open the Port Properties window where you can configure the port-level anti-spoofing options for the selected port.
Click the graphic for more information.
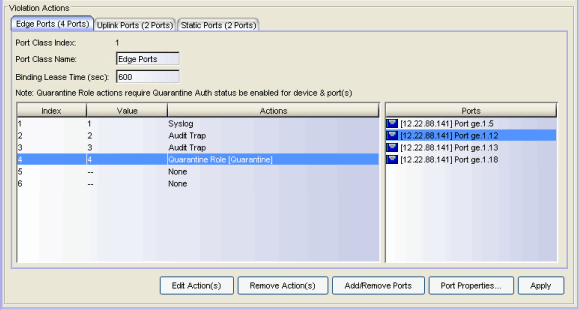
Up to three port classes can be configured on the switch. This index number shows which port class is being configured.
Use this field to set a name for the port class, for example, Edge Ports.
The number of seconds a binding will exist before being removed by the device.
Select an action and click this button to open the Edit Actions window, where you can configure the threshold value and action.
This button removes any selected actions.
Use this button to add or remove ports from this port class.
Select a port and click this button to open the Port Properties window where you can configure the port-level anti-spoofing options for the selected port. You can also configure port-level anti-spoofing options in the Port Configuration sub-tab.
Apply
Saves any change you made to the Violation Actions settings.
Port Configuration
This tab displays the port-level anti-spoofing settings for each port on the device. You can change port settings for one or more ports by multi-selecting ports and using the right-click menu. See below for a description of each column in the table.
Click the graphic for more information.
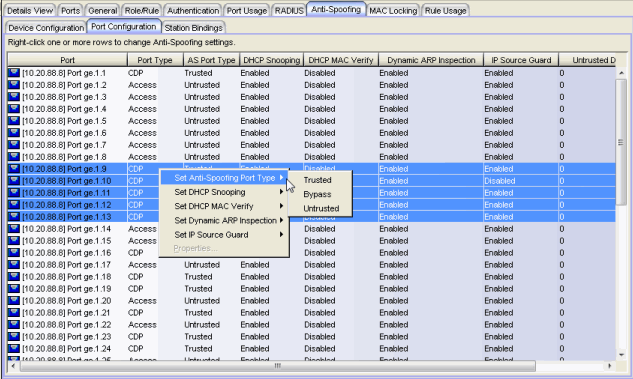
Displays the port name, constructed of the name or IP address of the device and either the port index number or the port interface name.
Type of port. Possible values include: Access, Interswitch Backplane, Backplane, Interswitch, and Logical.
The DHCP snooping port type configured for the port. Port type determines anti-spoofing behavior:
Trusted – DHCP server traffic is accepted and used to create bindings in the MAC-to-IP address binding table. Typically, only a port that is connected to a DHCP server would be set to trusted.
Bypass – Snooping of DHCP server traffic does not take place on the port. Typically, uplink ports out to the network would be set to bypass, as traffic would not be originating from that port.
Untrusted – The untrusted server counter is incremented when DHCP server traffic (DHCP ACK) is detected on the port, and the packets are dropped. DHCP RELEASE and DECLINE messages, sent by a client to free its IP address for use by another, are dropped if they are for a MAC address in the binding table that is on another port. If DHCP MAC Verify is enabled and the source MAC address does not match the Client Host Address in the DHCP payload (CHADDR), the packets are dropped. Typically, all edge ports with users would be set to untrusted.
Whether DHCP Snooping is enabled or disabled on the port.
Whether DHCP MAC Verify is enabled or disabled on the port.
Whether Dynamic ARP Inspection is enabled or disabled on the port. When set to inspection only, Dynamic ARP inspection will occur, but will not be used to create bindings.
Whether IP Source Guard is enabled or disabled on the port. When set to inspection only, IP Source Guard will occur, but will not be used to create bindings.
The number of DHCP server packets received on this port. This counter will only increment when the Port Type is set to untrusted.
Station Bindings
The Station Bindings table displays the current active bindings for the device set up through anti-spoofing. These bindings are the valid MAC/IP/Port associations detected on trusted ports from the various anti-spoofing methods such as DHCP requests. This tab also provides the ability to reset violation counters and clear bindings from the table. You must click the Retrieve button to display this information.
Click the graphic for more information.
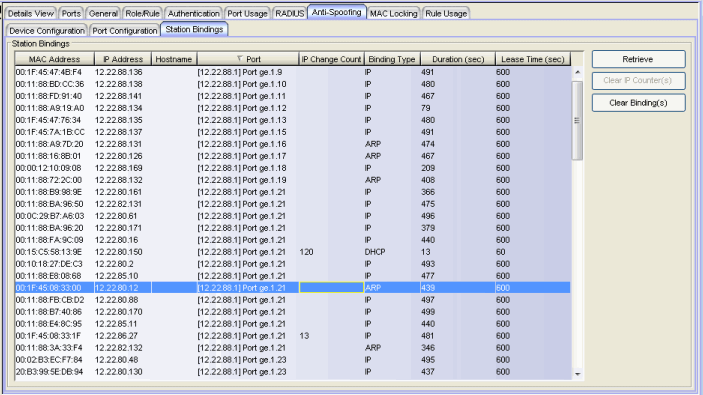
The MAC address of the binding.
The IP address of the binding.
An administratively-assigned hostname for the device. To determine the hostname, Policy Manager takes the IP address (when available) and uses the hostname cache on the NetSight server. The hostname cache must be explicitly enabled by selecting the "Enable Name Resolution" option in the Tools > Options > Suite Options > Name Resolution panel (by default, this option is disabled). Once the hostname cache is enabled, name resolution must be enabled for Anti-Spoofing Station Binding views using the Tools > Options > Policy Manager > Name Resolution (PM) panel.
The port that this binding currently resides on.
The number of times the IP address has changed for this binding.
Indicates which binding type (DHCP, ARP, or IP inspection) was used to create the entry.
The amount of time, in seconds, that this binding has been operational for.
The amount of time, in seconds, that this binding will be operational before being destroyed. A value of zero (0) indicates that this binding will not expire.
Retrieves the bindings for the device.
Resets the IP Change Count to zero for the binding.
Removes the binding from the table.
For information on related tasks: